Spam Campaigns Using Trickbot Banking Trojan on the Rise Targeting Cryptocurrencies and Non-traditional currencies.
A campaign involving Trickbot banking Trojan has been identified by Forcepoint Security Labs that is targeting cryptocurrencies. This Trojan is known for targeting financial institutions and its malware strain was firstly identified in fall 2016. According to security experts, the malware was developed by the same authors who were responsible for creating the now non-functional Dyre banking Trojan. Some operators if Dyre were arrested in Russia in the final quarter of 2015.
The newly discovered Trickbot campaign is very much alive and active at the moment, and experts have observed that the malware, which can already target financial platforms like Paypal, is further aiming to expand its scope by reaching out to institutions from Nordic countries. Moreover, it now possesses additional support for stealing funds stored in Coinbase (dot) com accounts. The new campaign uses an email that is apparently sent by the Canadian Imperial Bank of Commerce (CIBC); however, it is nothing else but a social engineering trap.
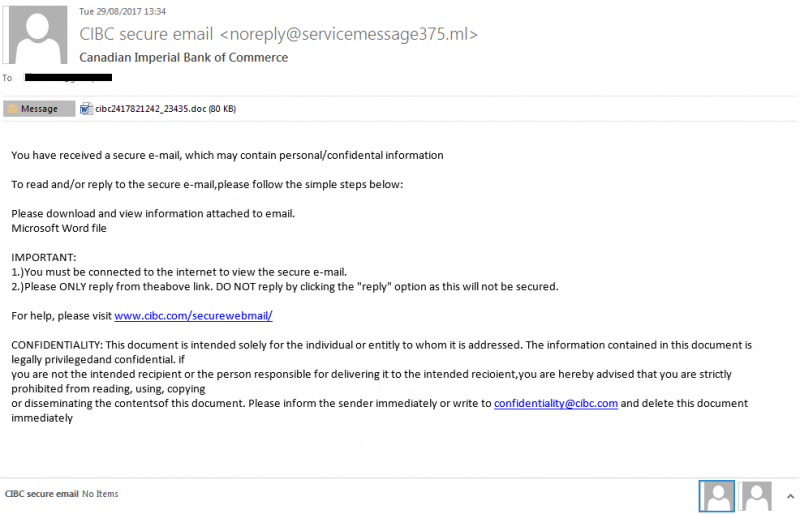
Screenshot of the email (Credit: Forcepoint)
Trickbot has claimed its targets around the globe. In the latest Trickbot campaign, more than 8,600 emails have been sent out until now, and main target locations include the UK, Australia, France and Canada, while most of the recipients have the TLD/top-level domain of “.com,” stated Forcepoint Labs in their official blog post.
[fullsquaread][/fullsquaread]
“Coinbase is a crypto-currency exchange site that operates exchanges of Litecoin, Bitcoin, Ethereum, and other digital assets. With Coinbase being targeted, non-traditional currencies are now also at risk of being stolen from would-be victims of the Trickbot banking Trojan,” said researchers.
Researchers claim that the new campaign has been active for the past few months; the malware has stolen the login details, authentication codes and other sensitive personal data from its target systems. The Blockchain platform hasn’t prevented the attacks, and as per the blog post by SANS ISC’s Brad Duncan, all the domains that have been identified were registered with GoDaddy. Different names and privacy services were used, states Duncan, and these domains used complete details of email authentication and HTTPS for getting implemented on the servers while a majority of the recipients were easily trapped into opening the malicious attachments.
The group tag “kas2” has been allotted to the new Trickbot variant that is to be downloaded. It also contains decrypted configuration files with a list of targets just like previous campaigns. However, what’s different this time is that the website coinbase.com has been added to track sites for web injections specifically the malware is appended for the Static Injection “sinj” configuration file.
Coinbase is a popular exchange platform that involves a variety of cryptocurrencies such as Bitcoin, Litecoin, and Ethereum, etc. Naturally, cyber crooks are interested in accessing the Coinbase’ user accounts credentials and transfer Bitcoins or other cryptocurrencies.
The samples discovered by Forcepoint security experts show that Trickbot instructs its configuration files to generate and overlay an unauthentic login page whenever the website Coinbase.com is visited by a user in the targeted device’s browser. Since the latest campaign targets Coinbase, therefore, it is apparent that the cryptocurrencies are also vulnerable at the moment.
We can easily state that the current campaign is a challenge to the reliability and stability of Blockchain platform considering if cryptocurrency gets stolen through malware attack then it will be a grave issue because every coin has a unique code. This also makes non-cryptocurrency accounts equally vulnerable and at risk.









