Accessing deep web is not an difficult now days. You just have to install TOR in your operating system. TOR is the freeware available over the internet to access deep web. There are many reasons why an user want to use TOR, mention ethical hacking professors. Tor provides privacy online as it creates an encrypted path between source and destination.
According the ethical hacking researcher of International Institute of Cyber Security deep explorer comes in handy if you are using TOR for researching purposes as it shows some active links related to your query.
Tor mostly uses .onion extension if you are using Tor. You probably uses TORCH search engines. But there are many other search engines like not evil, duckduckgo, searx etc. If you are surfing TOR, you will find some of the links probably don’t open, ethical hacking teachers clarifies. So before searching anything on the TOR browser. Use DEEP EXPLORER to get the links according to the query you want to search.
DEEP EXPLORER is a linux tool written in python to get active onion links. Deep explorer is written is search of hidden services on TOR network. If you search any keyword. Deep explorer will find that onion page that contains that keyword.
For showing you we have used KALI LINUX 2018.3
- For using deep explorer type git clone https://github.com/blueudp/Deep-Explorer.git in linux terminal.
- After cloning go to directory Deep-Explorer. Type cd Deep-Explorer
- Than type ls
- Before installing the required files for deep explorer make sure you update/install your python in Kali Linux.
- For updating python type sudo apt-get update
- Then type sudo apt-get install python3-pip
- After updating python type pip3 install -r requirments.txt
root@kali:/home/iicybersecurity/Deep-Explorer# pip3 install -r requirements.txt
Requirement already satisfied: interruptingcow in /usr/local/lib/python3.6/dist-packages (from -r requirements.txt (line 1))
Requirement already satisfied: beautifulsoup4 in /usr/lib/python3/dist-packages (from -r requirements.txt (line 2))
Requirement already satisfied: requests in /usr/lib/python3/dist-packages (from -r requirements.txt (line 3))
- We have already installed thats why it’s showing requirement already satisfied.
- After installing requirements type python3 deepexplorer.py
root@kali:/home/iicybersecurity/Deep-Explorer# python3 deepexplorer.py
__ __
.--| .-----.-----.-----. .-----.--.--.-----| .-----.----.-----.----.
| _ | -| -| _ | | -|_ | | | _ | | -| |
|||| | ||.| |||| ||| || |__|
dexplorer.py SEARCH NUMBER_OF_RESULTS crawl_options intext
Crawl Options:
all) crawl each link
none) dont crawl
default) crawl if not enough links
- For usage of deep explorer follow below steps.
Using Ransomware Query :-
- Type python3 deepexplorer.py ransomware 5 default
- ransomware is the query on which deep explorer will find.
- 5 is the no. of links that deep explorer will find.
- default means move forward if deep explorer are not able to find enough links.
root@kali:/home/iicybersecurity/Deep-Explorer# python3 deepexplorer.py ransomware 5 default
__ __
.--| .-----.-----.-----. .-----.--.--.-----| .-----.----.-----.----.
| _ | -| -| _ | | -|_ | | | _ | | -| |
|||| | ||.| |||| ||| || |__|
Checking Tor instance [OK]
Checking Tor proxy [OK]
Searching. . . [OK]
Checking links
http://crdclub4wraumez4.onion
http://gandcrab2pie73et.onion
http://auutwvpaxl4dtym4.onion
http://forohpysho2t5mjs.onion
http://auutwvpmfqfsmcen.onion
5
SEARCH COMPLETE [OK]
- After executing the above command it shows the 5 links related to ransomware.
- Now we will open some of the above onion links. The above onion links will open in TOR browser.
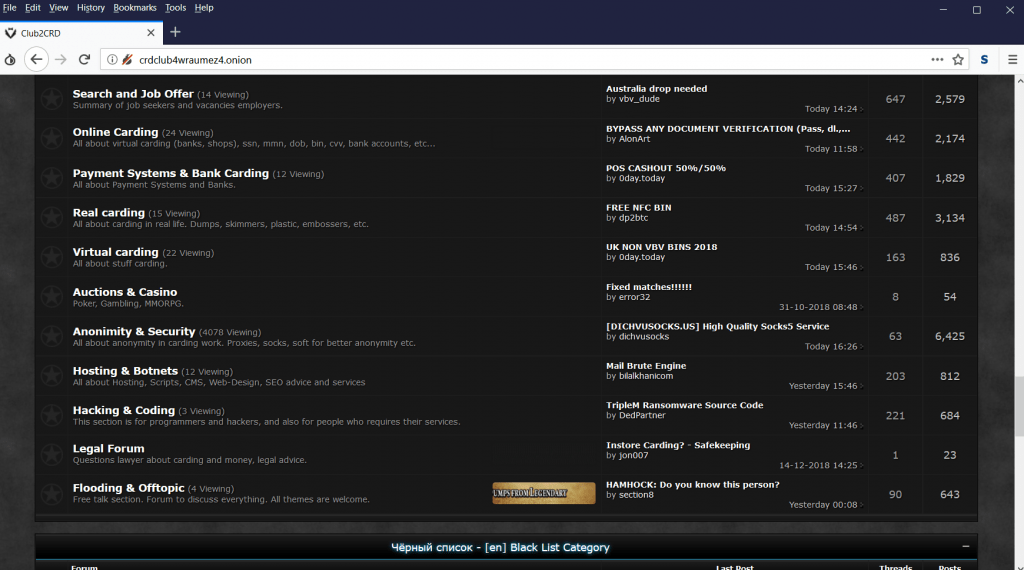
- The above screen shot shows the ransomware information on the onion link. Ransomware has become very much popular.
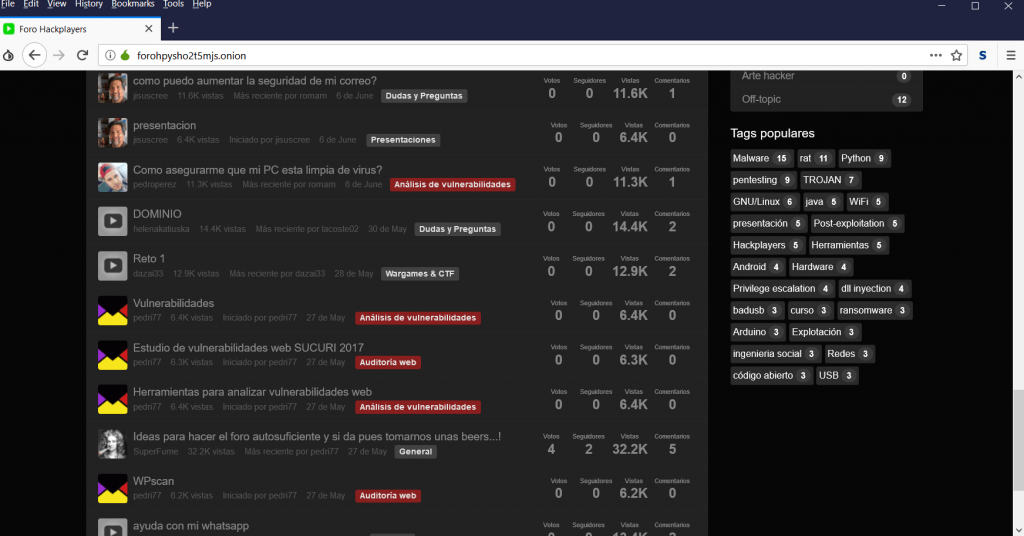
- Above screen shot gives an brief information about ransomware.
Using Creditcard Query :-
- Type python3 deepexplorer.py creditcard 20 none
- credit card is the query on which deep explorer will find.
- 20 is the no. of links that deep explorer will find.
- none will try to find as many data related to query above entered.
root@kali:/home/iicybersecurity/Deep-Explorer# python3 deepexplorer.py creditcard 20 none
__ __
.--| .-----.-----.-----. .-----.--.--.-----| .-----.----.-----.----.
| _ | -| -| _ | | -|_ | | | _ | | -| |
|||| | ||.| |||| ||| || |__|
Checking Tor instance [OK]
Checking Tor proxy [OK]
Searching. . . [OK]
Checking links
http://agartha2oooh2cxa.onion
http://cccenterjb27ubnm.onion
http://cavetord6bosm3sl.onion
http://cccentersemzrqne.onion
http://vendorcugc6oppvb.onion
http://freerj4lgqdjjuk6.onion
http://honeym4ms4nq7fdl.onion
http://3bbaaaccczcbdddz.onion
http://ntdcvkgv3kzrzdxp.onion
http://zlal32teyptf4tvi.onion
http://ox7ekwo2vrnxeghg.onion
http://crdclub4wraumez4.onion
http://dmania2naw2cprdm.onion
http://dlnfeuawnyh5fjlc.onion
http://gcardsmfp2ub6bwt.onion
http://gcardstguk366hru.onion
http://buyccoq36hlj6etg.onion
http://linkdirdgrhkr2zm.onion
http://v7avmdv2l6dio3cg.onion
http://eozm6j6i4mmme2p5.onion
20
5
SEARCH COMPLETE [OK]
- After executing the above command it shows the result related links to credit card.
- Now we will try to open some of the onion links which sells credit cards.
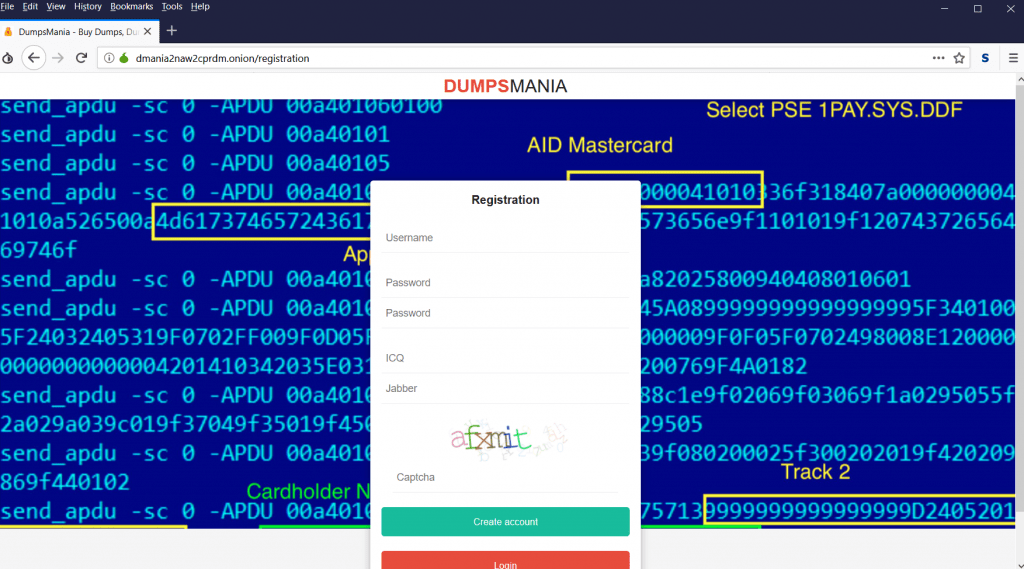
- The above screen shot is used to purchase fake credit card details. First you have to create a account then you can purchase fake credit card.
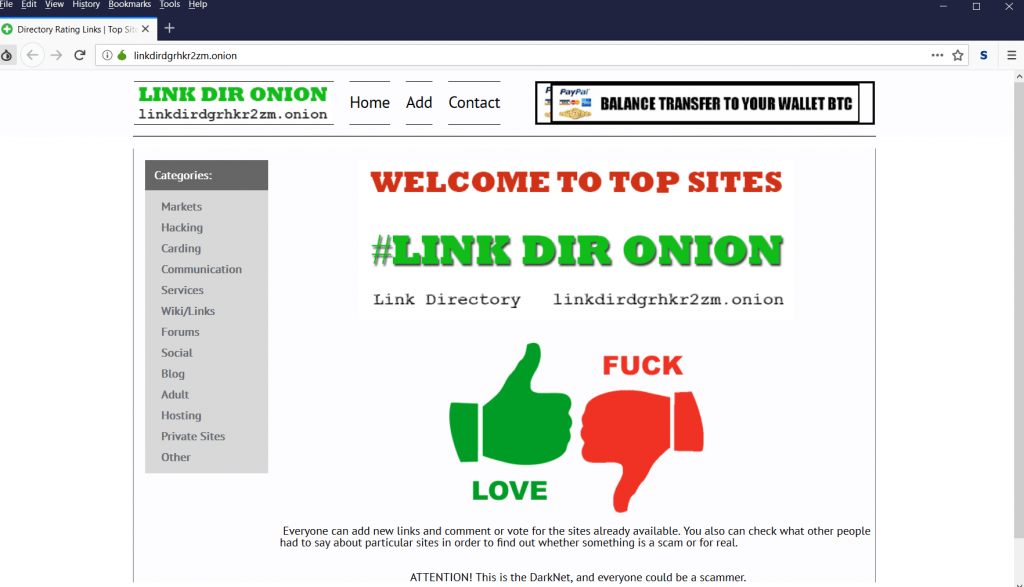
- Here is an another link which is used to purchase credit cards on onion link.
Using Proxies Query :-
- Type python3 deepexplorer.py proxies 20 all
- proxies is the query on which deep explorer will find.
- 20 is the no. of links that deep explorer will find.
- all will be used to show each link even if the link contains only the single query which has been used in search.
root@kali:/home/iicybersecurity/Deep-Explorer# python3 deepexplorer.py proxies 20 all
__ __
.--| .-----.-----.-----. .-----.--.--.-----| .-----.----.-----.----.
| _ | -| -| _ | | -|_ | | | _ | | -| |
|||| | ||.| |||| ||| || |__|
Checking Tor instance [OK]
Checking Tor proxy [OK]
Searching. . . [OK]
Checking links
http://dr5aamfveql2b34p.onion
Crawling from : [http://dr5aamfveql2b34p.onion]
http://cplfk4kp5dzeakwc.onion
Crawling from : [http://cplfk4kp5dzeakwc.onion]
http://crdclub4wraumez4.onion
Crawling from : [http://crdclub4wraumez4.onion]
http://www.dragonbyte-tech.com/vbecommerce.php?productid=2&do=product&utm_source=crdclub4wraumez4.onion
http://www.dragonbyte-tech.com/?utm_source=crdclub4wraumez4.onion
http://kkkkkkkkkk63ava6.onion
Crawling from : [http://kkkkkkkkkk63ava6.onion]
http://forums.kkkkkkkkkk63ava6.onion
http://bdfcctess3zhicun.onion
Crawling from : [http://bdfcctess3zhicun.onion]
http://jqs44zhtxl2uo6gk.onion
Crawling from : [http://jqs44zhtxl2uo6gk.onion]
http://vendpmmhx5ylctjf.onion
Crawling from : [http://vendpmmhx5ylctjf.onion]
http://beatnixo6vjocscp.onion
Crawling from : [http://beatnixo6vjocscp.onion]
http://parckwartvo7fskp.onion
Crawling from : [http://parckwartvo7fskp.onion]
http://rougmnvswfsmd4dq.onion
http://expyuzz4wqqyqhjn.onion
http://mattttttssi4lhud.onion
Crawling from : [http://mattttttssi4lhud.onion]
http://zfob4nth675763zthpij33iq4pz5q4qthr3gydih4qbdiwtypr2e3bqd.onion
http://m6su7s3ir7dxggwg.onion
http://jld3zkuo4b5mbios.onion
http://vwx4mjvwoszgnagzcrwdjlsq3pq3zyob3zpq5qissxdoivnuyylzn7yd.onion
http://hzmun3rnnxjhkyhg.onion
Crawling from : [http://hzmun3rnnxjhkyhg.onion]
LINKS COLLECTED!
- After executing the above command it shows the related links to proxies.
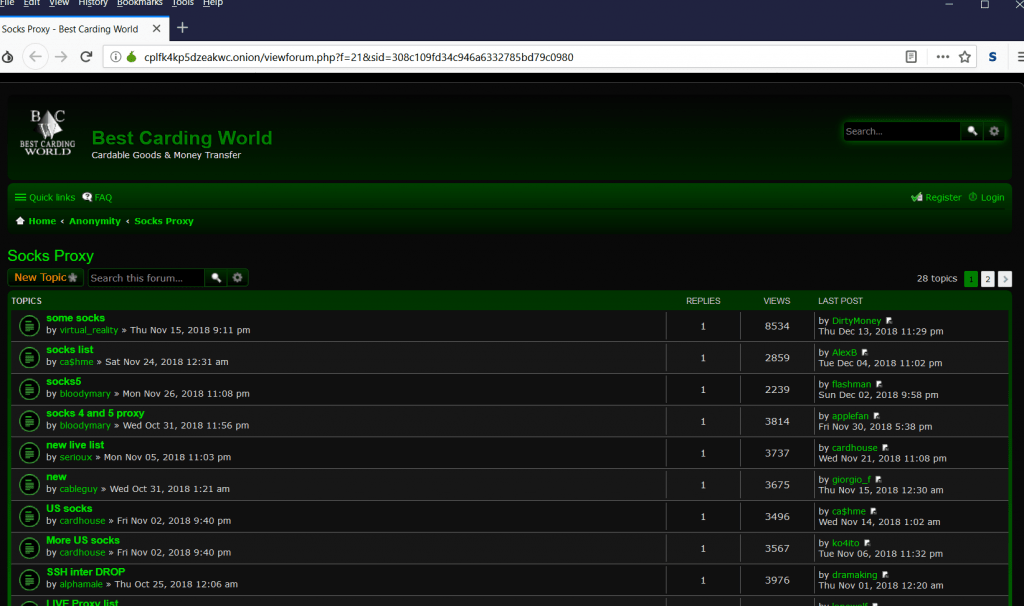
- The above site provide proxy list. These proxy list can be used to surf some another onion links.
- Some proxies may not work as it shows error while opening of the pages.
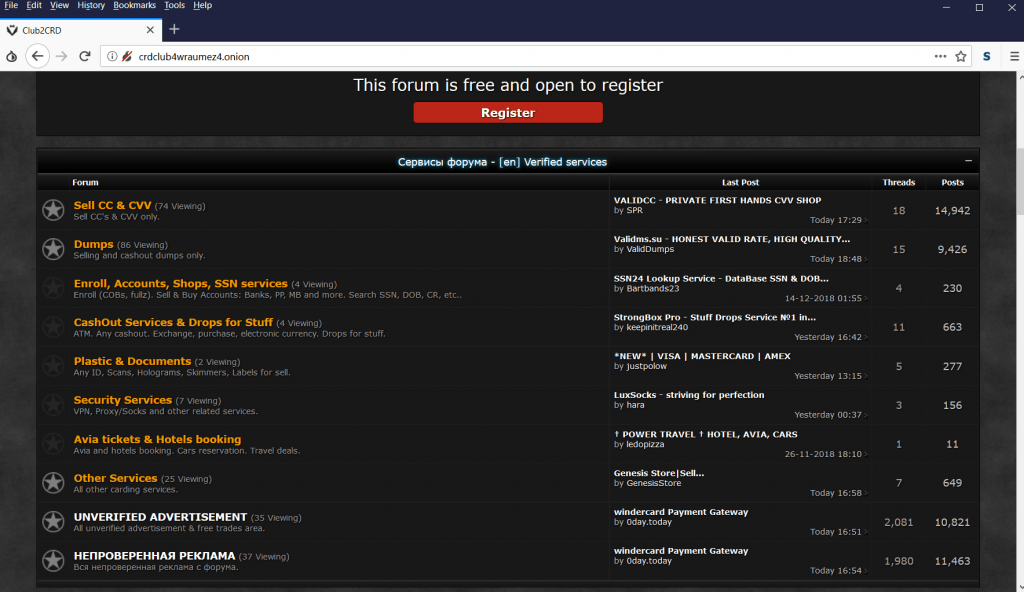
- The above screen shot gives some information about proxy and you can also get proxies list.
Using Porn Query :-
- DO NOT OPEN PORN SITES, THIS IS JUST FOR EDUCATIONAL PURPOSE. SO WE HAVE BLURRED THE PHOTOS. THESE TOR NODES SHOULD BE BANNED BY GOVERNMENT
- Type python3 deepexplorer.py porn 5 default
- porn is the query on which deep explorer will find.
- 5 is the no. of links that deep explorer will find.
- default means move forward if deep explorer are not able to find enough links.
root@kali:/home/iicybersecurity/Deep-Explorer# python3 deepexplorer.py porn 5 default
__ __
.--| .-----.-----.-----. .-----.--.--.-----| .-----.----.-----.----.
| _ | -| -| _ | | -|_ | | | _ | | -| |
|||| | ||.| |||| ||| || |__|
Checking Tor instance [OK]
Checking Tor proxy [OK]
Searching. . . [OK]
Checking links
http://hbmyffcf4x2f56ml.onion
http://pu23yyt5u5p3xd23.onion
http://cavetord6bosm3sl.onion
http://neboardo3svhysmd.onion
http://h3clhio3nera3sxw.onion
5
SEARCH COMPLETE [OK]
- The above are the porn links which opens some pornography sites. THESE TOR NODES SHOULD BE BANNED BY GOVERNMENT
- Here are the few links which we tried to open. There sites works by paying them in cryptocurrency in order to use their services.
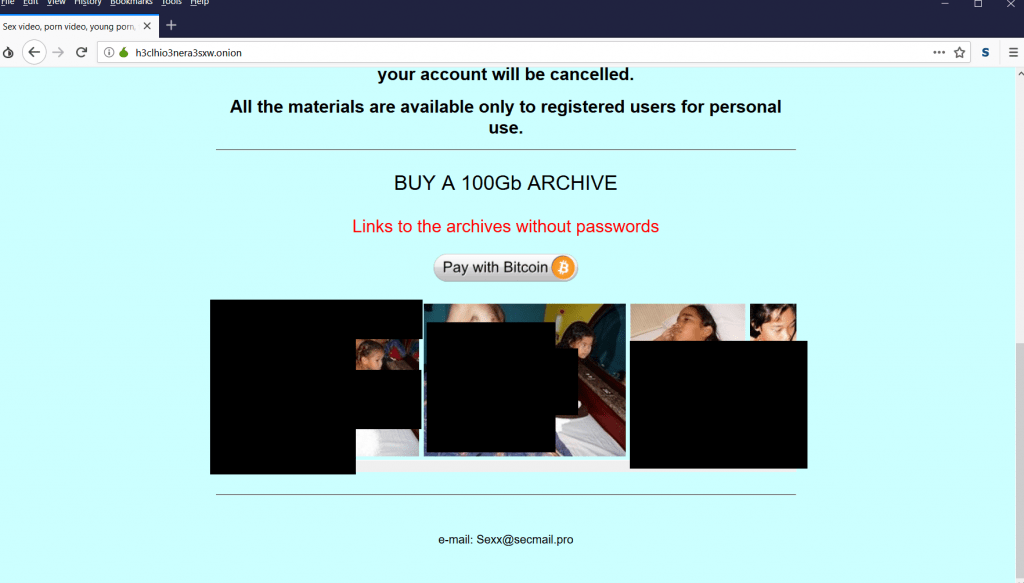
- The above is the porn sites listing that they have around 100Gb of archive.
- The above screen shot is the another example of pornography which are not good for kids.
Using Gun Query :-
- Type python3 deepexplorer.py guns 10 default
- guns is the query on which deep explorer will find.
- 10 is the no. of links that deep explorer will find.
- default means move forward if deep explorer are not able to find enough links.
root@kali:/home/iicybersecurity/Deep-Explorer# python3 deepexplorer.py guns 10 default
__ __
.--| .-----.-----.-----. .-----.--.--.-----| .-----.----.-----.----.
| _ | -| -| _ | | -|_ | | | _ | | -| |
|||| | ||.| |||| ||| || |__|
Checking Tor instance [OK]
Checking Tor proxy [OK]
Searching. . . [OK]
Checking links
http://godnotorweygn7ne.onion
http://l62y7ilqoioymugj.onion
http://wywg65dio2lhe76z.onion
http://pistolcqex2ecr5r.onion
http://drkseidwayn6uc5x.onion
http://2kka4f23pcxgqkpv.onion
http://godnotordyhrk4fs.onion
http://tuu66yxvrnn3of7l.onion
http://agartha2oooh2cxa.onion
http://2kka4yzbx3mjymsd.onion
10
SEARCH COMPLETE [OK]
- The above are the gun links where guns can be purchased by paying them bitcoins.
- Her are the come of the onion links which we have opened to show you.
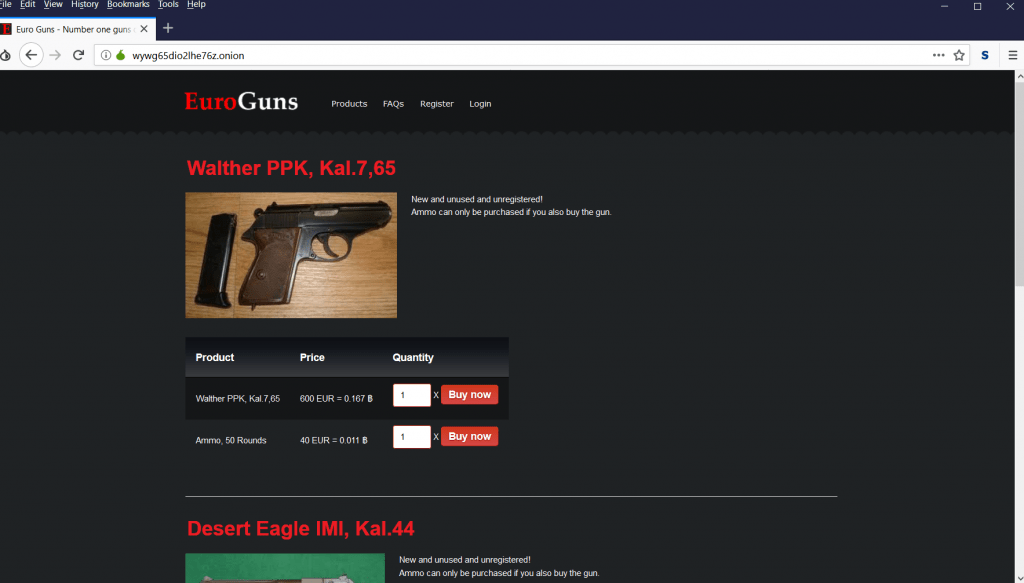
- The above screen shot is of onion link which sell guns on deep web.
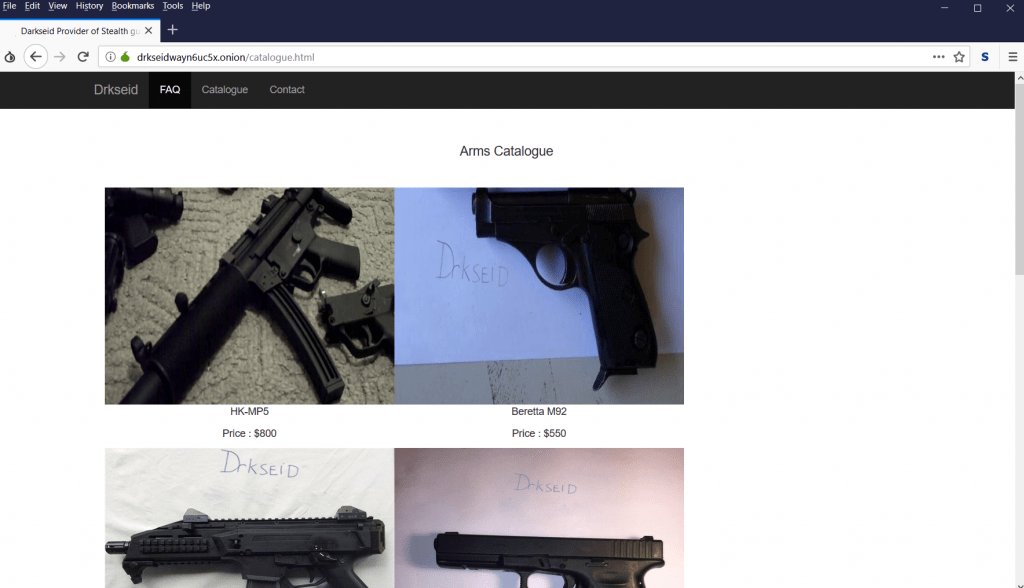
- Here is the another screen shot of onion link which are selling rifles on deep web.
You can also try for some different keywords to search. The above method shows most active onion links. Ethical hacking researcher of International Institute of Cyber Security recommend you use onioff, if you want to check any onion link is active or not you can check with onioff







