The Federal Bureau of Investigation (FBI), in collaboration with the Australian Federal Police announced the end of Operation Ironside or Trojan Shield, based on the administration of an encrypted chat platform and the interception of thousands of messages, leading to the deployment of thousands of raids and arrests against all kinds of criminal groups, including drug gangs.
During the announcement, Australian police representatives mentioned that this operation began in 2018, when a specialized FBI group managed to shut down Phantom Secure, an encrypted chat platform really popular in the cybercriminal world; because of this, the authorities expected that the criminals would try to find a reliable platform. To do this, authorities created Anøm (also called AN0M), a chat platform that FBI agents could access through an insider.
Like other similar platforms and services, AN0M relies on the use of secure smartphones specially configured to run only the messaging app. These services allow users to send encrypted text and voice messages between devices with the app installed in a completely confidential manner. All data on these devices is fully protected and no phone number is required to use the app.
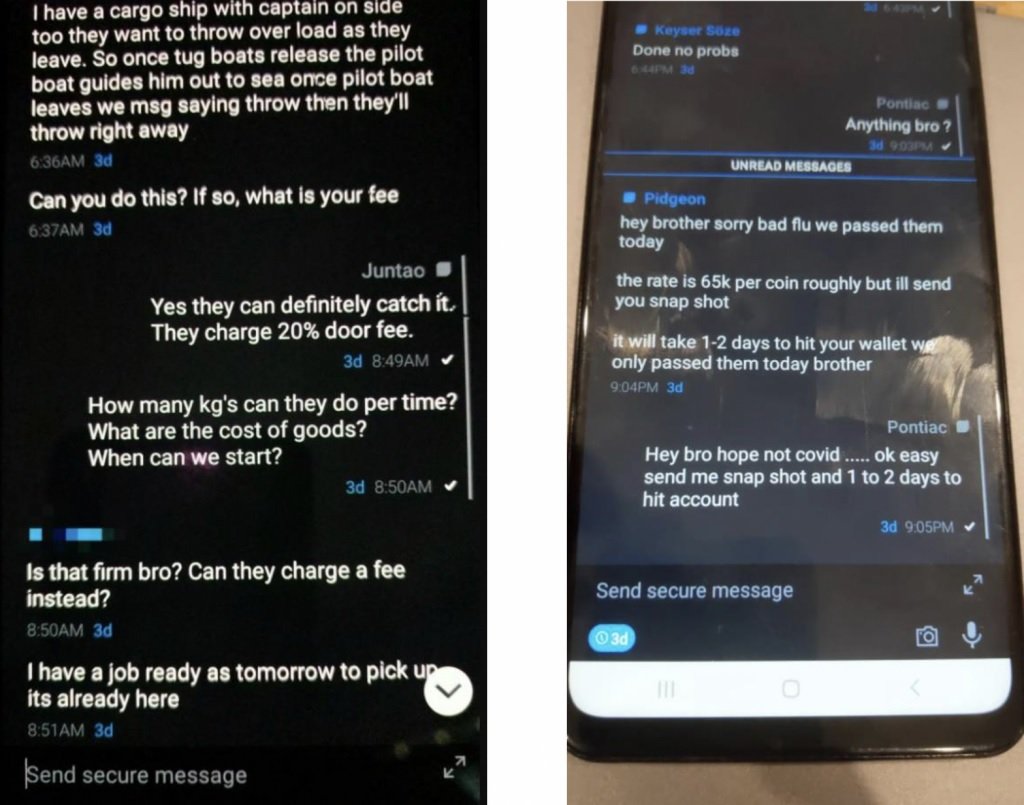
As mentioned above, agents were able to access sensitive information managed by AN0M through an intermediary that provided copies of all messages sent through this platform as of October 2018. The interception of these messages was made possible by the fact that devices running AN0M were configured to send a hidden copy of all their messages to an XMPP bot. Later the bot was in charge of decrypting the messages and re-encrypting them, this time using encryption keys handled by the FBI.
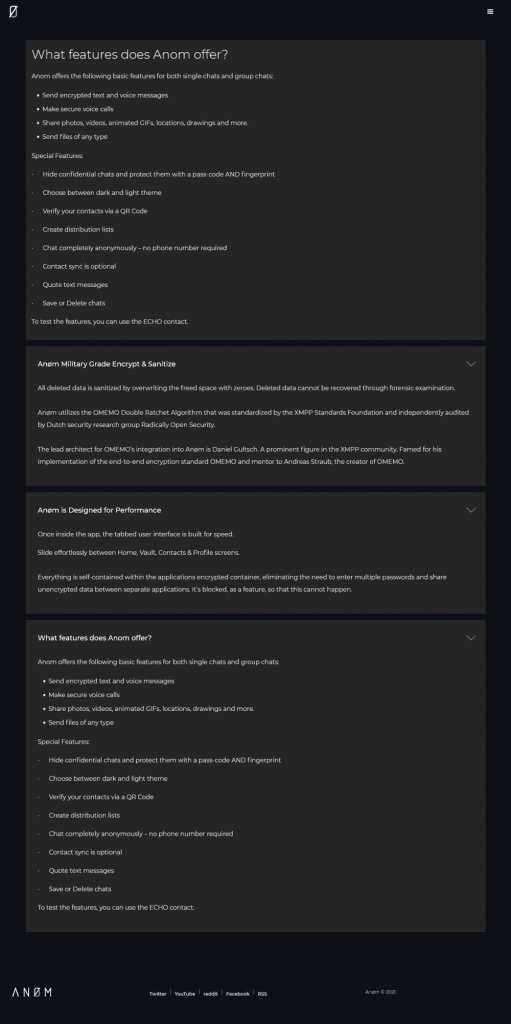
In the operation, the FBI was in charge of managing the intermediary scheme while the Australian authorities reviewed the messages sent on AN0M on a regular basis. The judicial report of this operation points to the involvement of a third country (unnamed) that hosted another bot server to extract and analyze around 25 million encrypted messages.
Although it is mentioned that some cybercriminal groups detected the leak of their conversations since March 2021, Operation Ironside remained active until this June 7 and is already considered one of the largest intelligence operations in the history of the FBI. The vast majority of criminal cases brought as a result of this operation are still active, so we will have to wait a little longer to know the final number of arrests and detentions resulting from this intelligence work.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.