Threat actors have taken note of the large number of UEFI vulnerabilities that have been found in recent years, as well as the many missed opportunities to fix these flaws or revoke vulnerable binaries within a time frame that is considered to be acceptable. As a direct consequence of this, the first UEFI bootkit that is known to the general public may now circumvent the crucial platform security feature known as UEFI Secure Boot. Experts have found a new UEFI bootkit, which is capable of operating on even fully updated versions of Windows 11 computers that have UEFI Secure Boot enabled. Because of the functionality of the bootkit and the individual features that it possesses, researchers have reason to believe that researchers are dealing with a bootkit known as BlackLotus. BlackLotus is a UEFI bootkit that has been sold on hacking forums for at least five thousand dollars since at least October 2022. UEFI bootkits are extremely dangerous because they have complete control over the operating system’s boot process. Because of this, they are able to disable a variety of OS security mechanisms and install their own kernel-mode or user-mode payloads in the early stages of the operating system’s startup process. Because of this, they are able to do their business in a highly covert manner and with a great degree of privilege.
The following is a rundown of the most important information on BlackLotus, that provides a concise summary of the sequence of events that are connected to it.
It is possible to operate on the most recent versions of Windows 11 that have all available patches installed and UEFI Secure Boot enabled. It does this by exploiting a vulnerability that is more than a year old (CVE-2022-21894) in order to get around UEFI Secure Boot and establish persistence for the bootkit. This is the very first instance of this vulnerability being exploited in the field and being widely aware about it.
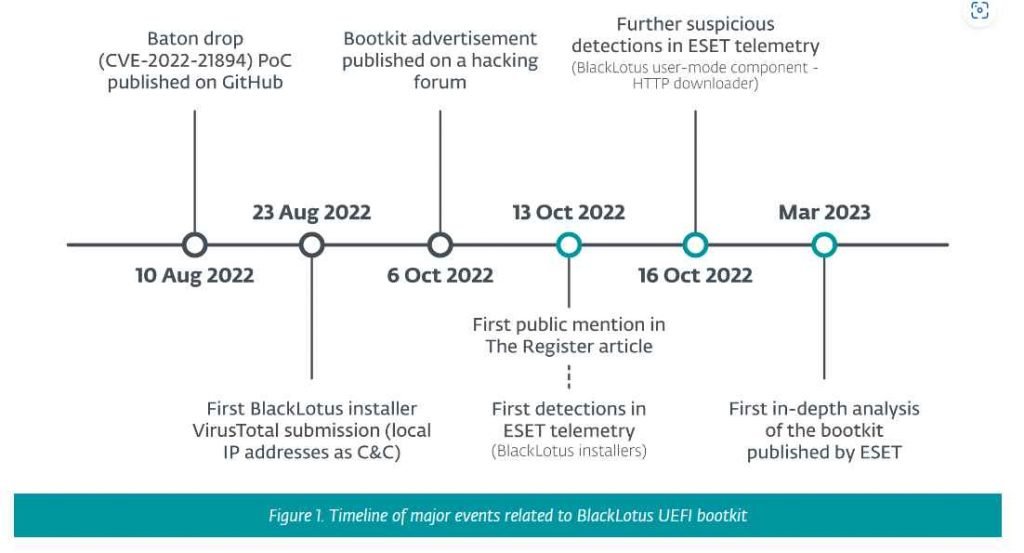
Despite the fact that the vulnerability was patched in the update that Microsoft released in January 2022, its exploitation is still feasible since the impacted binaries that have been legitimately signed have not yet been placed to the UEFI revocation list. BlackLotus makes use of this fact by introducing its own versions of valid binaries that are, nonetheless, susceptible to exploits into the system in order to take use of the vulnerability.
It is possible to disable operating system security measures including BitLocker, HVCI, and Windows Defender amongst others.
Once it has been installed, the primary objective of the bootkit is to install a kernel driver, which, among other things, prevents the bootkit from being removed, as well as an HTTP downloader, which is responsible for communication with the command and control server and is able to load additional user-mode or kernel-mode payloads.
At the very least, BlackLotus has been promoted and offered for sale on underground message boards since October 6th, 2022.
It is interesting to note that some of the BlackLotus installers that have been investigated do not continue with the installation of the bootkit if the compromised host utilizes one of the following locales:
- Romanian (Moldova), ro-MD
- Russian (Moldova), ru-MD
- Russian (Russia), ru-RU
- Ukrainian (Ukraine) , uk-UA
- Belarusian (Belarus), be-BY
- Armenian (Armenia), hy-AM
- Kazakh (Kazakhstan), kk-KZ
A rundown of the attack
Image illustrates a condensed version of the BlackLotus compromise chain’s overall structure. It is made up of these three primary components:
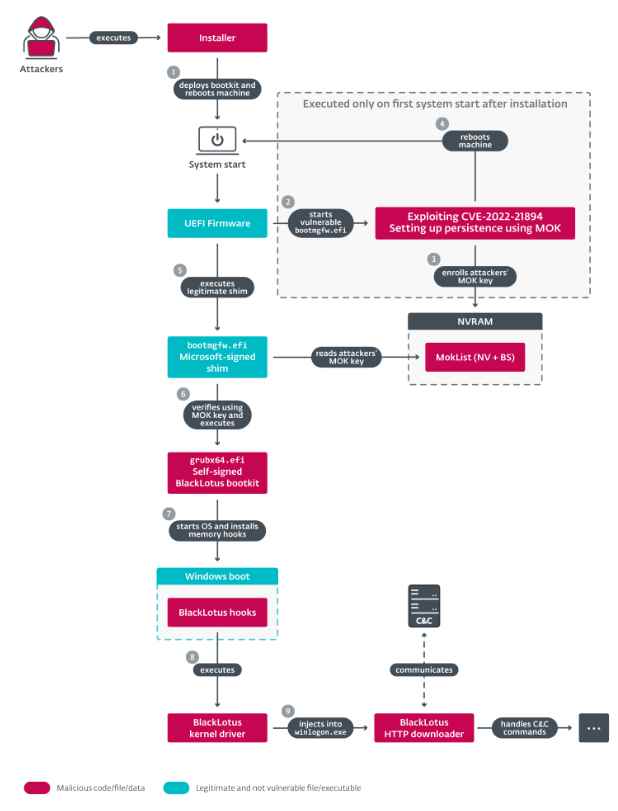
It begins with the execution of an installer, which is shown as step one . This installer is in charge of deploying the bootkit’s data to the EFI System partition, turning off HVCI and BitLocker, and then restarting the computer.
Exploitation of CVE-2022-21894 and subsequent enrolment of the attackers’ Machine Owner Key (MOK) occurs after the first reboot to achieve persistence even on systems with UEFI Secure Boot enabled. This happens after the vulnerability has been exploited. The computer is restarted once again at this point.
Execution of the self-signed UEFI bootkit occurs on all future boots, at which point it delivers both its kernel driver and user-mode payload, in the form of an HTTP downloader. Combined, these components provide the bootkit the ability to withstand removal attempts and allow for the downloading and execution of further user-mode and driver components obtained from the C&C server as per experts.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.