A free operating system that is similar to Unix and Berkeley Unix is called FreeBSD. It is derived from Research Unix via the Berkeley Software Distribution (BSD), which is also called Berkeley Unix.
Who is Actually Utilizing FreeBSD?
Perhaps a much larger number of individuals than you anticipate. FreeBSD may be found almost everywhere. In point of fact, there’s a strong probability that you’re making use of some code that was developed from FreeBSD in your day-to-day activities. FreeBSD is likely already installed on your device if you use services like Netflix or WhatsApp to communicate with friends or play games on your PlayStation 4, which are among the most popular gaming consoles today.
The developers and maintainers of the FreeBSD operating system have published patches to fix a major flaw in the ping module that was given the CVE identifier CVE-2022-23093. This vulnerability has the potential to be exploited in order to acquire remote code execution.
Ping is a tool that may be used to verify the reachability of a remote host by sending ICMP packets; however, in order to access raw sockets, it needs elevated privileges. Unprivileged users may access it by installing a setuid bit set on their system to make it accessible. This indicates that each time ping is executed, it first establishes the raw socket and then revokes the elevated privileges it has previously been granted.
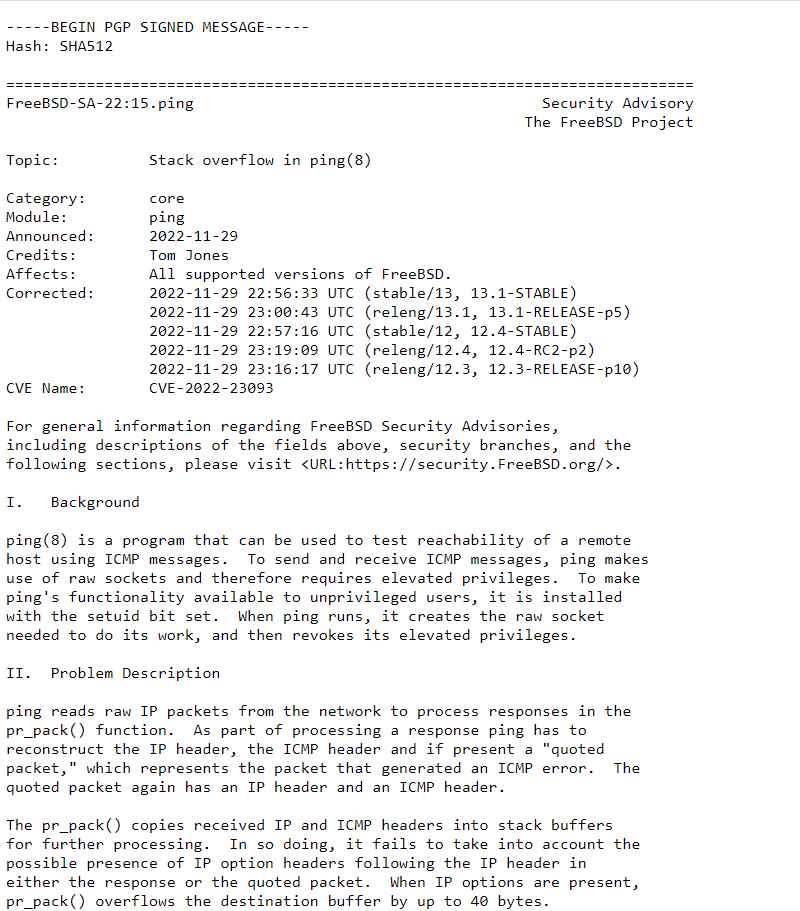
The vulnerability may be triggered by an attacker located remotely, which will result in the ping application crashing and may also lead to the remote execution of code contained inside ping.
On all affected versions of FreeBSD, the ping process operates in a capability mode sandbox, which severely limits how it may communicate with other components at the time when the problem can manifest.
“In order to prepare for further processing, the pr pack() function copies incoming IP and ICMP headers into stack buffers. As a consequence of this action, it does not take into consideration the potential inclusion of IP option headers after the IP header in either the answer or the quoted packet.”
Because of this, the destination buffer may experience an overflow of up to 40 bytes whenever the IP option headers are included in the packet.
According to the FreeBSD Project, the ping process operates behind a capability mode sandbox, which means that it is restricted in the ways in which it may communicate with the rest of the operating system.
The open-source firewall and routing software OPNsense, which is based on FreeBSD, has also published a patch (version 22.7.9) to address the security vulnerability, in addition to a number of other problems.
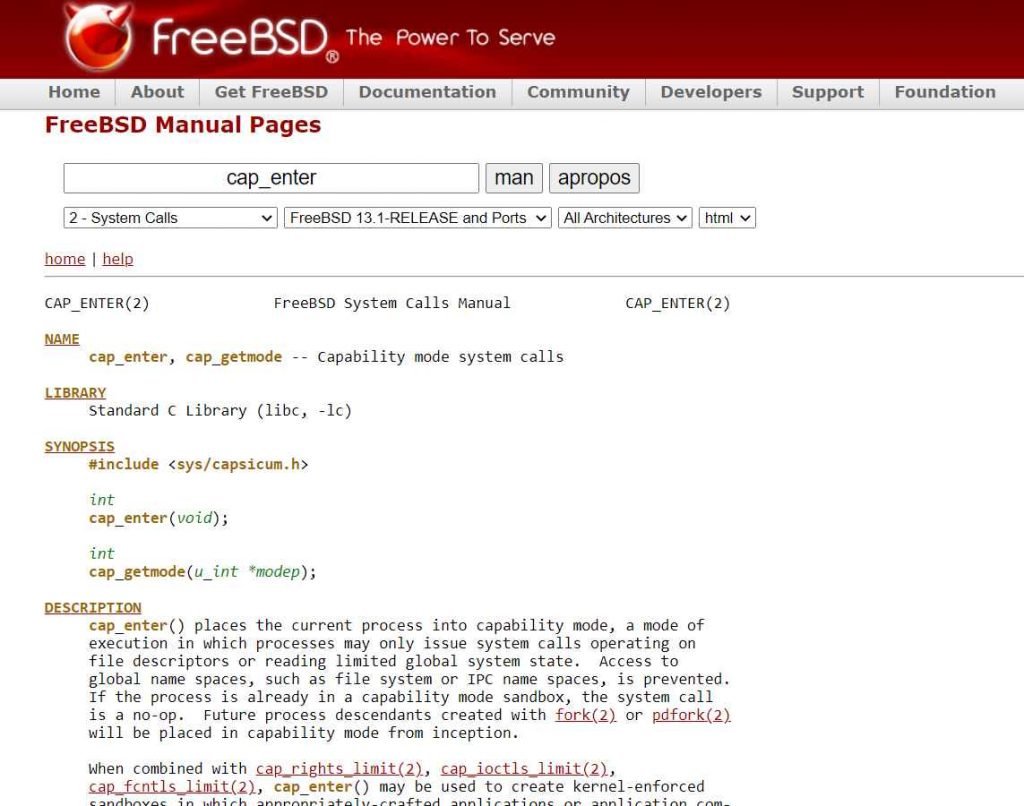
Researchers have suggested that susceptible systems be upgraded to a supported version of the FreeBSD stable or release / security branch (releng) with a date that is later than the date of the fix.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.