It’s been a few weeks since a researcher accidentally disclosed the PrintNightmare vulnerability, a zero-day bug in the Windows print service that would allow threat actors to execute remote code on affected systems. Although Microsoft released updates to address the bugs, both researchers and malicious hackers have revealed some methods to bypass security measures and get a successful attack.
One of these methods was developed by researcher Benjamin Delpy, who created an Internet accessible remote print server with which any Windows user with limited privileges can gain full control of a vulnerable device through the installation of a specially designed driver.
Delpy, researcher and creator of the popular Mimikatz tool, created a print server in //printnightmare.gentilkiwi.com, which installs a print driver and launches a DLL with SYSTEM privileges. This DLL writes a special file to the C:WindowsSystem32 folder, which could only be modified by an elevated privilege user.
After a testing stage, Delpy modified the driver to launch a SYSTEM command line, so that any user, legitimate or malicious, could gain administrative privileges only with the remote installation of this driver. A successful attack would allow threat actors to add new user accounts, install unauthorized software, and even execute any commands on the affected system.
Specialists mention that this technique could be very functional for hackers trying to compromise the security of an affected network in order to deploy a ransomware infection, as this method allows quick access to the affected devices. A group of experts decided to test this driver, installing it on a Windows 10 21H1 computer with full patches.
As shown in the following image, once the printer is installed and Windows Defender is disabled, a command prompt is launched that allows hackers to obtain all SYSTEM privileges.
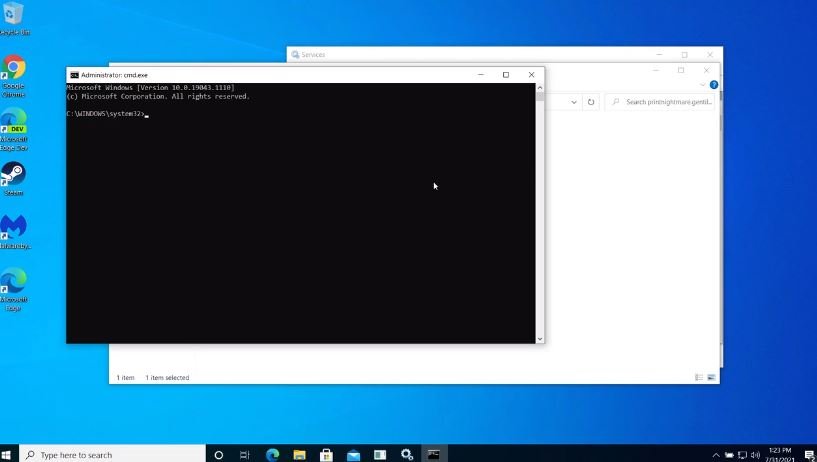
In this regard, Delpy mentions that he disclosed his research in order to pressure Microsoft to have the vulnerability fully addressed. Finally, the researcher mentions that he sees it highly likely that threat actors will continue to abuse this flaw, especially considering the new findings revealed by the cybersecurity community on the capabilities of threat actors to exploit these flaws.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















