A couple of months ago Ubuntu and Debian officials published security advisories related to CVE-2022-0543, a vulnerability derived from a bug in the Redis package in operating systems that received a score of 10/10 according to the Common Vulnerability Scoring System (CVSS). According to security advisories, insufficient disinfection of the Lua environment, employed by Redis, could trigger the arbitrary execution of Lua and the evasion of The Redis sandbox environment, compromising thousands of Linux servers.
Last March, researcher Reginaldo Silva, who was credited with finding this vulnerability, published a proof-of-concept (PoC) code, followed by the report of a case of active exploitation just days later.
At this point, the cybersecurity community assumes that there are more public and private exploits, so threat actors will continue to actively try to exploit the flaw until a permanent fix is released.
Who is affected?
When the report was released, it was mentioned that the flaw only affected distributions that use Ubuntu or Debian Redis packages, in addition to the fact that exploitation requires a non-default configuration in Redis and exposure of this dangerous configuration on the Internet.
Although the massive exploitation of CVE-2022-0543 would appear to be a remote exploitation, the Rapid7 researchers decided to analyze the conditions that could facilitate a large-scale attack, in an attempt to calculate how many vulnerable implementations might be currently available. In addition, the exploitation requires a non-default configuration in Redis and exposure of this dangerous configuration on the Internet.
After a month of testing, experts discovered approximately 33,000 Redis servers connected to the Internet allowing unauthenticated access. Although the vulnerability also affects hosts that require authentication, the analysis focused on implementations that facilitate remote access.
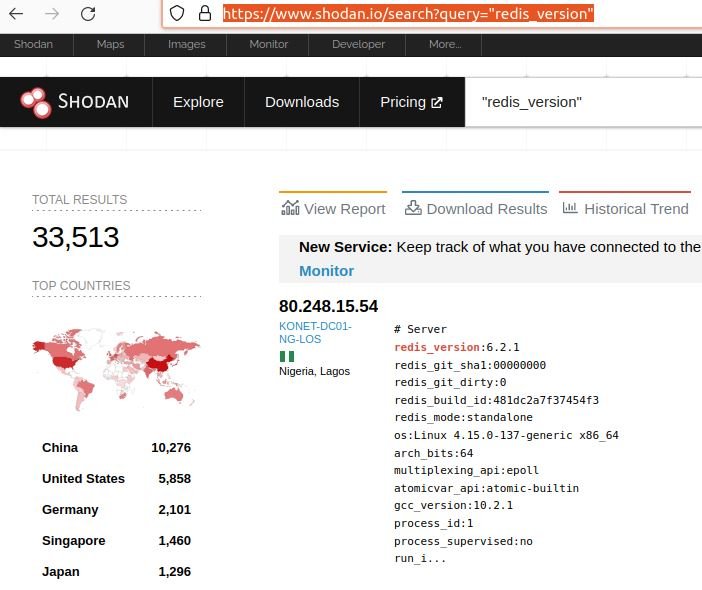
Based on this finding, it was simpler for the researchers to determine how many of these servers could be exposed to the exploitation of this flaw, for which they used the well-known Shodan search engine.
Next, experts began to filter potential affected implementations by applying criteria such as analyzed distribution and Redis version.
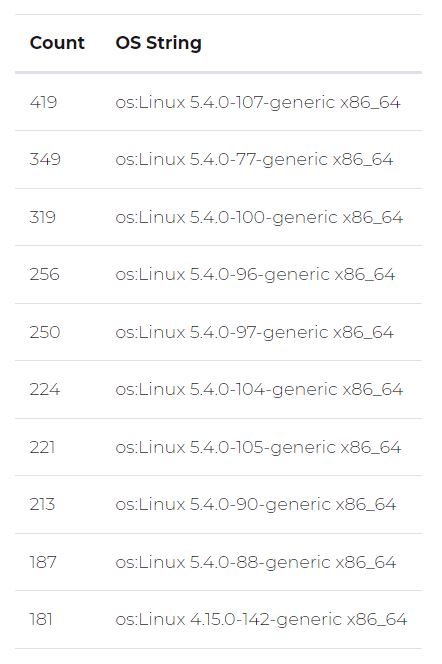
At the end of this process, up to 2,000 potentially vulnerable Redis servers were identified. Although it is not possible to know how many of these hosts installed Redis using affected packages, how many have received updates, or how many are honeypots, the risk should be taken seriously.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















