A new zero-day vulnerability has been found by Google’s Threat Analysis Group (TAG), and it is being actively exploited by hackers who are aiming their attacks at users in South Korea.
During the month of October 2022, the TAG team at Google identified this zero-day vulnerability, and immediately thereafter, the team informed the Microsoft security team about the issue. The vulnerability that was being exploited was swiftly addressed by Microsoft, and patches were made available to protect users from further attacks.
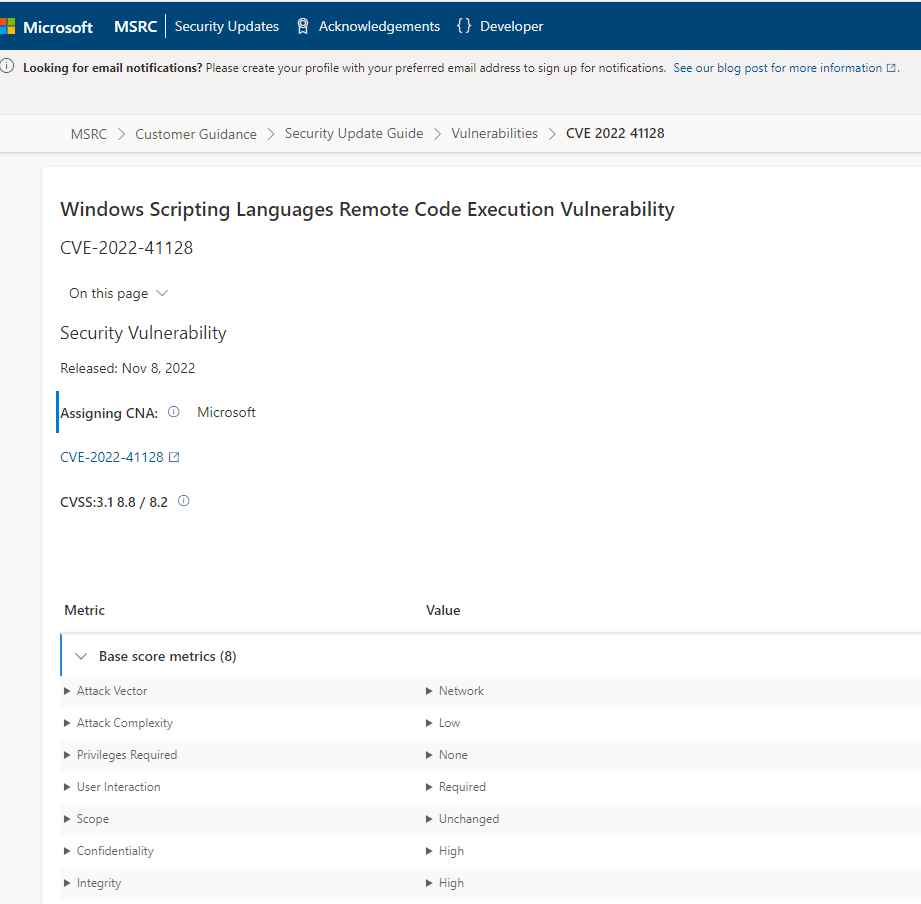
Google believes that the activity was carried out by members of a group known as APT37 who are supported by the North Korean government. Hackers are inserting malicious code into Microsoft Office documents, and these malicious documents exploited a 0-day vulnerability in the JScript engine that was present in Internet Explorer (CVE-2022-41128).
The TAG team at Google discovered a vulnerability that affects the JScript9 scripting language. This vulnerability resides within “jscript9.dll,” which is the JavaScript engine of Internet Explorer. This vulnerability can be exploited to execute malicious code when rendering an attacker-controlled webpage.
Before the attacker can successfully exploit the vulnerability, they must first deactivate the protected view and then retrieve the remote RTF template.
In addition, the Google TAG team discovered more files that may be abusing the same vulnerability and using targeting that is comparable; these publications may be a part of the same campaign.
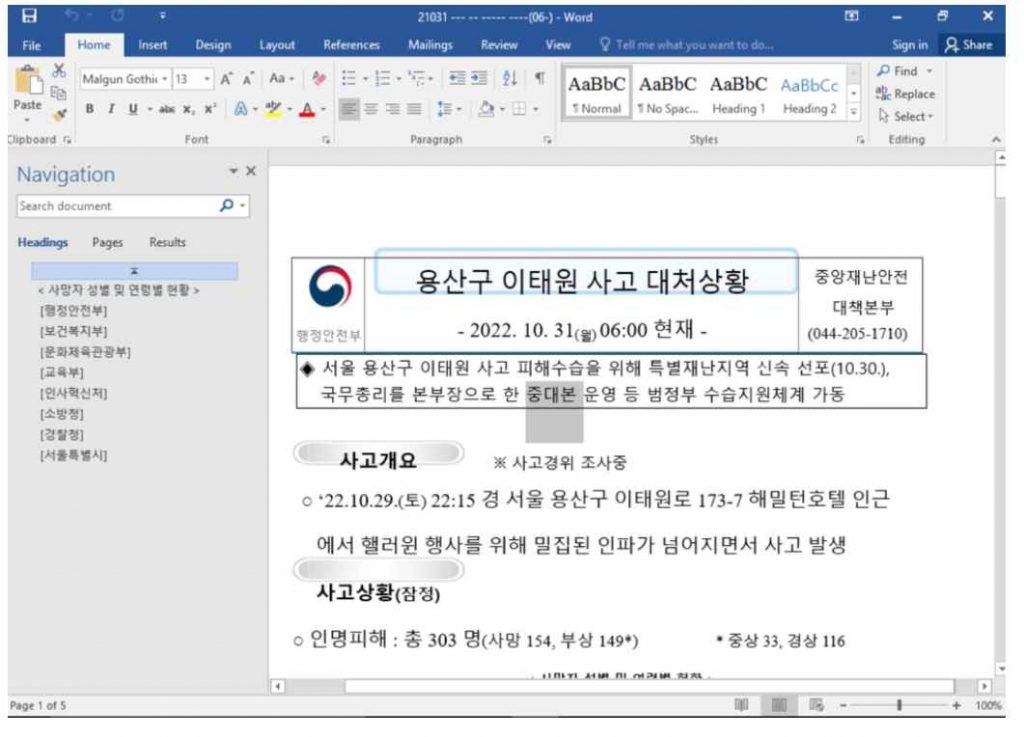
On October 31, 2022, many submitters from South Korea uploaded a Microsoft Office document to VirusTotal in order to report new malware. The fatal event that occurred in the area of Itaewon in Seoul, South Korea on October 29, 2022, during Halloween festivities is mentioned in the document with the title “221031 Seoul Yongsan Itaewon accident reaction situation (06:00).docx.”
The malicious document that was shared with others caused a remote rich text file (RTF) template to be downloaded, which then downloaded remote HTML content. Since Office uses Internet Explorer (IE) to produce this HTML information, this method has seen widespread usage to deliver Internet Explorer (IE) vulnerabilities via Office files since since 2017. (e.g. CVE-2017-0199). When executing Internet Explorer exploits using this vector, it is not necessary for the target computer to have Internet Explorer set as the default browser, nor is it necessary to chain the attack with an EPM sandbox escape.
Indicators of compromise (IOCs)
Initial documents:
- 56ca24b57c4559f834c190d50b0fe89dd4a4040a078ca1f267d0bbc7849e9ed7
- af5fb99d3ff18bc625fb63f792ed7cd955171ab509c2f8e7c7ee44515e09cebf
- 926a947ea2b59d3e9a5a6875b4de2bd071b15260370f4da5e2a60ece3517a32f
- 3bff571823421c013e79cc10793f238f4252f7d7ac91f9ef41435af0a8c09a39
- c49b4d370ad0dcd1e28ee8f525ac8e3c12a34cfcf62ebb733ec74cca59b29f82

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.