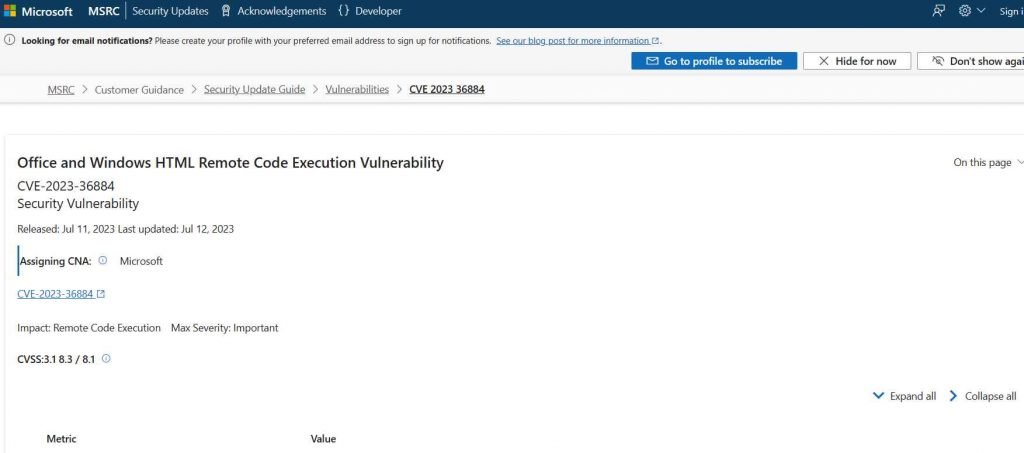
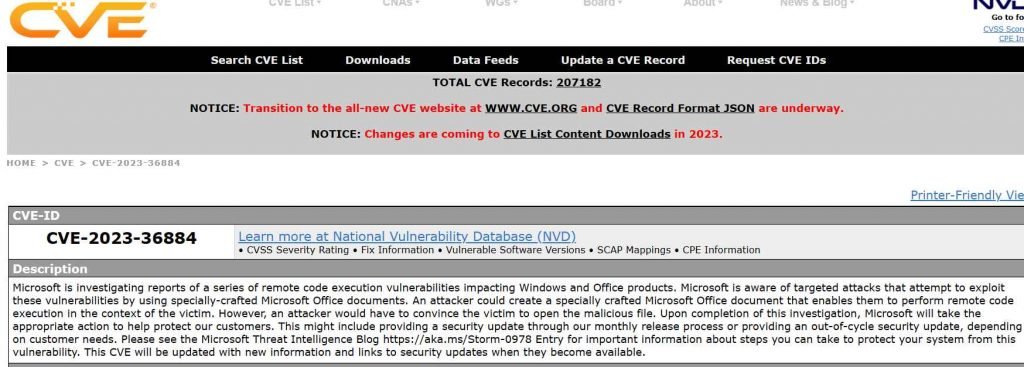
Microsoft reported a previously unknown vulnerability known as a zero-day flaw that was present in many versions of Windows and Office and was being actively exploited in the wild. The vulnerability, which was tracked and given the identifier CVE-2023-36884, was used by nation-state actors and cybercriminals to acquire remote code execution by using infected Office documents. The massive information technology company is looking into allegations of many vulnerabilities that allow remote code execution and affect Windows and Office products. The firm said that it is aware of high-targeted attacks that aim to exploit these weaknesses using specially created Office documents. These attacks were exposed by the corporation. Microsoft is attempting to remedy the issue, and security researchers have suggested that it may be remedied with an out-of-band patch that can be sent prior to the August Patch Tuesday update.
Microsoft revealed in a separate article that it has identified a phishing effort as having been carried out by the Russian cybercrime organization known as Storm-0978 (also known as DEV-0978 and RomCom), with the intention of targeting military and government organizations in Europe and North America. It was discovered that threat actors were attempting to take advantage of the vulnerability CVE-2023-36884 by utilizing lures associated with the Ukrainian World Congress.
This zero-day vulnerability enables high-complexity attacks to be carried out by unauthenticated attackers without the need for any involvement on the part of the user.
Storm-0978, sometimes known as DEV-0978, is a cybercriminal organization based in Russia that is notorious for engaging in the illegal actions listed below:
- Extortion with ransomware used for opportunistic purposes
- Campaigns aimed specifically towards the collection of credentials
- Possibly aiding in the activities of intelligence agencies
The Storm-0978 malware targets companies by spreading trojanized copies of popular software, which ultimately leads in the installation of RomCom, the malware’s backdoor. RomCom is the name of their backdoor.
If attackers are successful in exploiting it, they will get the following abilities:
1.Obtaining access to confidential information
2. Disables system protection
3. Denies access
Patches will be made available to all of Microsoft’s customers as quickly as possible, an assurance that the company gave them despite the fact that the vulnerability has not yet been resolved.
Mitigations
- Customers that make use of Microsoft Defender for Office are safeguarded against attachments that make an effort to take advantage of this vulnerability.
- The adoption of the Block all Office programs from starting child processes Attack Surface Reduction Rule will prevent the vulnerability from being used in the present attack chains. This rule will reduce the attack surface.
- In order to avoid being exploited, organizations that are unable to make use of these precautions may prevent themselves from being exploited by setting the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry entry. Please be aware that despite the fact that the aforementioned registry adjustments would prevent the problem from being exploited, they could disrupt the normally operating functionality of specific use cases that are linked to these apps. In this registry entry, add the names of the applications in the following list as values of type REG_DWORD with data 1:
ComputerHKEY_LOCAL_MACHINESOFTWAREPoliciesMicrosoftInternet ExplorerMainFeatureControlFEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
- Excel.exe
- Graph.exe
- MSAccess.exe
- MSPub.exe
- Powerpnt.exe
- Visio.exe
- WinProj.exe
- WinWord.exe
- Wordpad.exe

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.