Officials at Check Point, the IT security vendor, have discovered a rogue app on the Google Play Store that is exploiting the recently identified Certifi-gate bug.
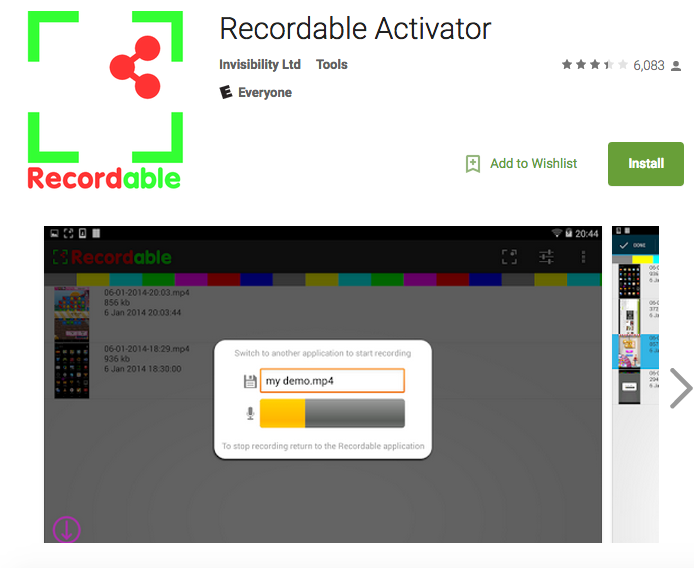
Recordable Activator (downloaded by 6,083 users), the application that has been accused of this malicious behavior, is a screen-recording app that was created by Invisibility, a UK-based company.
[must url=”https://www.hackread.com/android-malware-apps-hacking-facebook/”]One Million Android Users Infected With Facebook Hacking Malware Apps[/must]
This bug allows unauthorized access to a person’s Android device, giving the attacker complete control over it. However, in the case of Invisibility’s app, an attacker’s control is extremely limited – they can only mirror the contents of the affected device’s screen.
The app has been removed from Google Play store
Although Google promptly proceeded to take the app off the Store, the underlying cause for the bug still lies in the operating system’s core plugins. The ‘Remote Support Tool’ (mRST) plugin comes pre-installed by a majority of device manufacturers and is used primarily for services like TeamViewer.
To limit the harm caused by the bug, TeamViewer developers implemented safety measures into their app, according to a press release.
A spokesperson from the company stated that their “updated version of TeamViewer QuickSupport for Android includes an improved security mechanism to ensure safe communication between internal app components”.
However, since older versions of the plugin still exist on many devices, Check Point has cautioned that attackers can still find a way into them through a third-party server.
The director of Invisibility, Christoper Fraser, has stated that he was oblivious about the existence of the bug and that he never intended to exploit people’s privacy. Fraser added that while he was getting his own plugin for the app signed, he discovered the open-source TeamViewer QuickSupport app.
“The plugins allowed [third-party] applications to access the screen so I added support for using that via the Recordable Activator app,” he said.
From almost 30,000 scan results collected by Check Point, they have concluded that although only 0.01% of the devices were exploited, almost 42% devices were vulnerable and 16% had vulnerable versions of the plugin.
Report typos and corrections to [email protected]
[src src=”Source” url=”http://blog.checkpoint.com/2015/08/25/certifigate-statistics-exploitation-mitigation/”]CheckPoint[/src]