Tutorials
-

 345
345Detect Web Application Firewall (WAF) before you attack
WEB APPLICATION FIREWALL BASICS:- WAF (Web application firewalls) plays an important role in securing the websites. As they filter/monitor the traffic. Web...
-

 383
383HOW TO BE ANONYMOUS ON INTERNET
INTRODUCTION:- In this digital era, our information is more public than private. The massive growth of internet users is increasing day by...
-

 504
504XSS Shell- Cross Site Scripting
XSS-Shell Intro:- XSS Shell framework uses cross-site scripting to get reverse shell. In order to attack on the victim’s web browser you...
-
 286
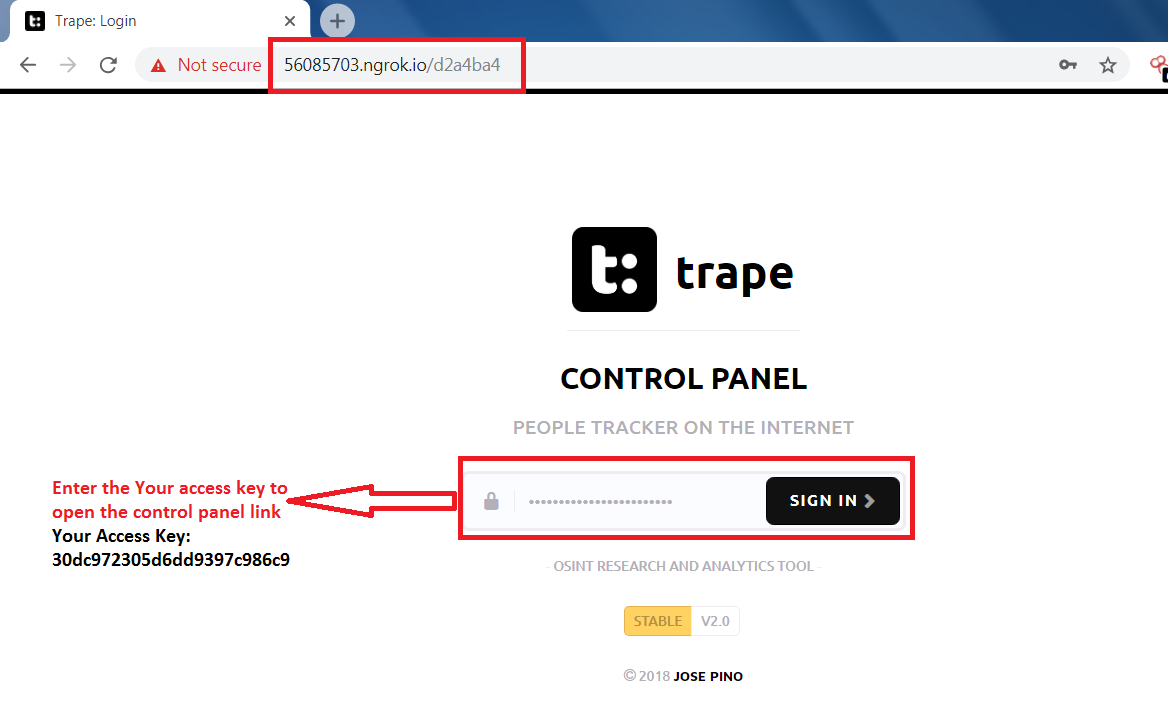
286Track people on internet – Trape demo tutorial
Trape Intro:- Trape is a OSINT (Open Source Intelligence Tool) is a tracking tool in which you can execute social engineering attack in...
-

 421
421CREATE YOUR OWN WORDLIST WITH CRUNCH
CRUNCH INTRO:- While cracking the password, attacker always needs an wordlist. Normally, wordlist use thousand of words per second to crack the...
-
 315
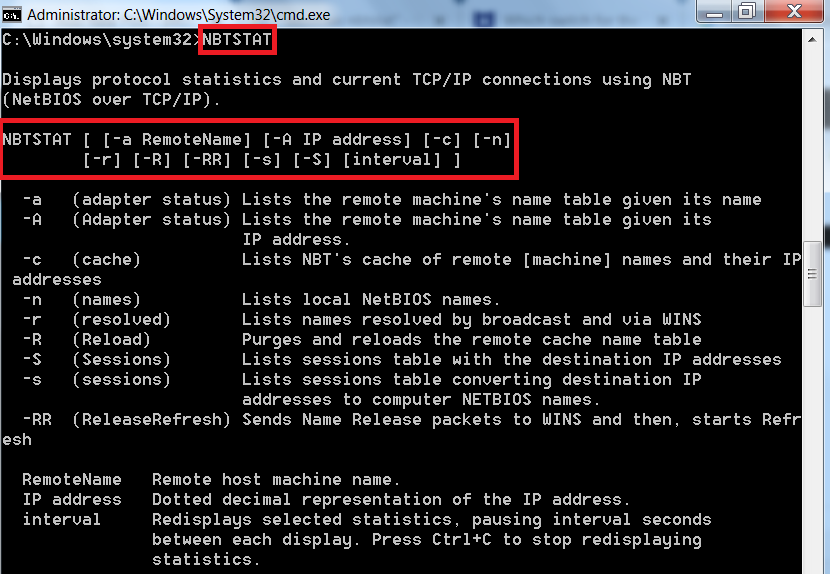
315Netbios Over TCP/IP – nbtstat usage in detail
As per ethical hacking professionals, Nbtstat is a network tool that is used to check the running TCP/IP connections. Nbtstat list all...
-

 350
350Crack Windows password with john the ripper
JOHN THE RIPPER:- John the ripper is a password cracker tool, which try to detect weak passwords. John the ripper can run...
-
 227
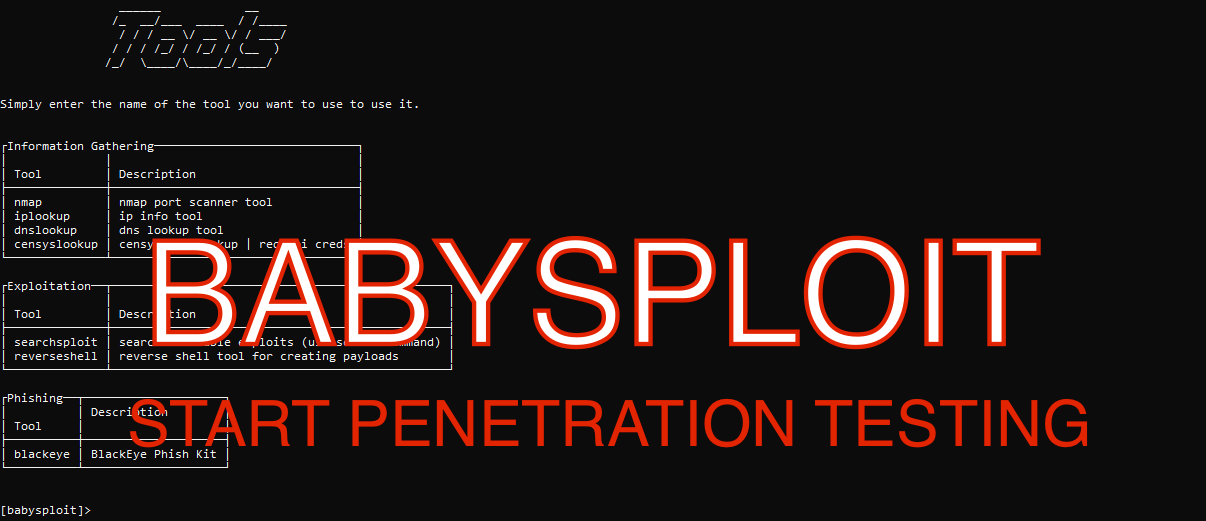
227BABYSPLOIT – AN BEGINNER PENTESTING TOOL
BABYSPLOIT INTRO:- Babysploit is a pentesting tool kit used in initial phase of pentesting. BabySploit mostly covers each and every scan. This...
-
 388
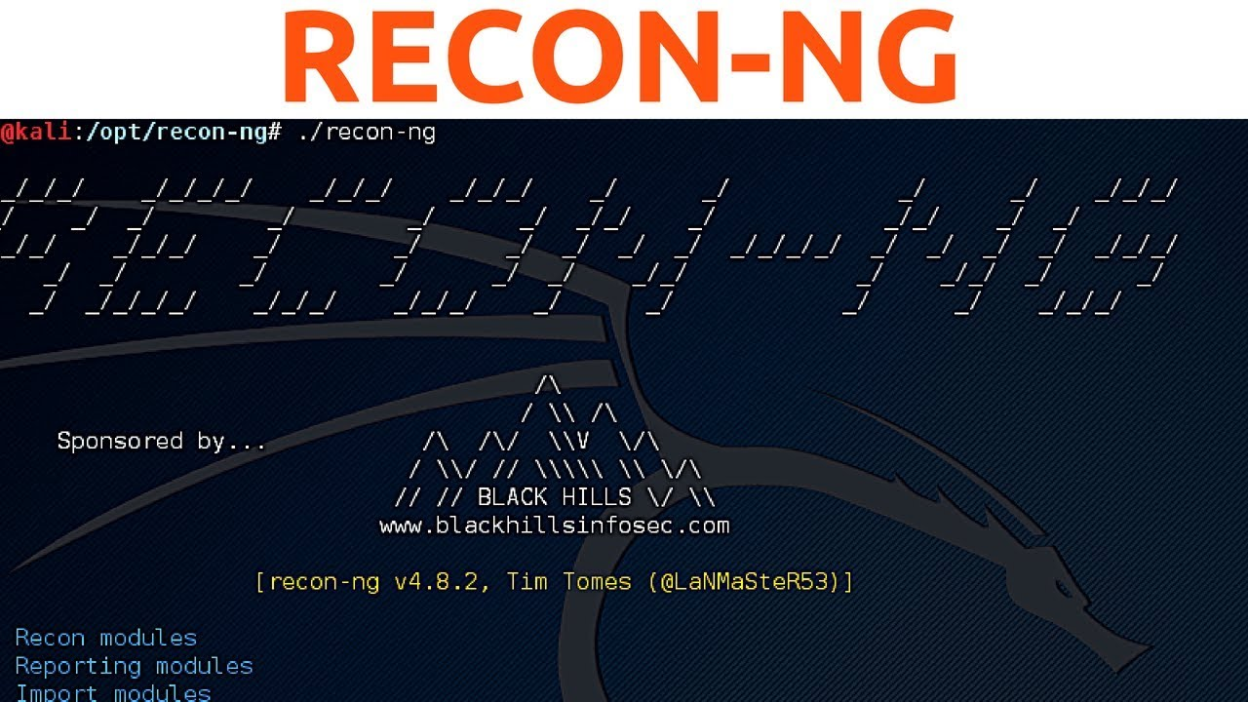
388recon-ng – Good tool for Information Gathering
Recon-ng is a tool written in python mostly used in information gathering with its independent modules, keys list and other modules. This...
-
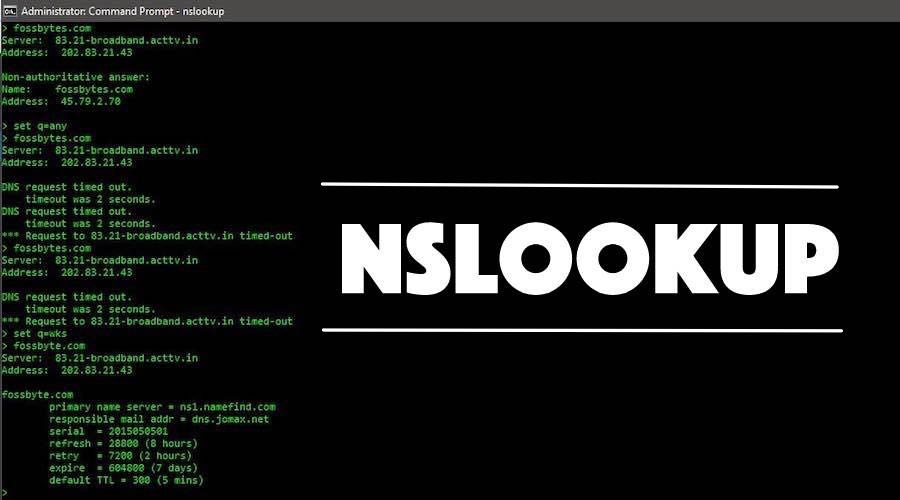
 385
385Use nslookup for footprinting
WHAT IS A DNS (DOMAIN NAME SERVER)?Domain Name Server or we can say Domain Name System is a distributed method that helps...
-

 232
232SSL vulnerability scanner – MassBleed
MASSBLEED:- Massbleed is a SSL vulnerability scanner. Its mainly check vulnerability in ssl of the target sites, as per ethical hacking investigators....
-

 315
315Use dig for footprinting
Domain Name Server or we can say Domain Name System is a distributed method that helps humans to remember name of any...
-

 277
277Uncover virtual hosts of domain with Fierce
FIERCE DNS SCANNER:- Fierce is a another domain scanner. It is written by Robert Hansen aka RSnake. It helps to locate non-contiguous...
-
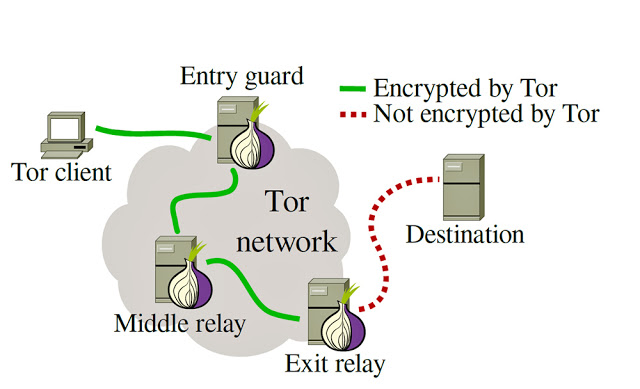
 307
307TOR EXIT RELAY SCANNER USING EXITMAP
TOR EXIT RELAY SCANNER:- As we all know tor is used for anonymous communication in anonymity network. Exitmap modules implement tasks that...
-
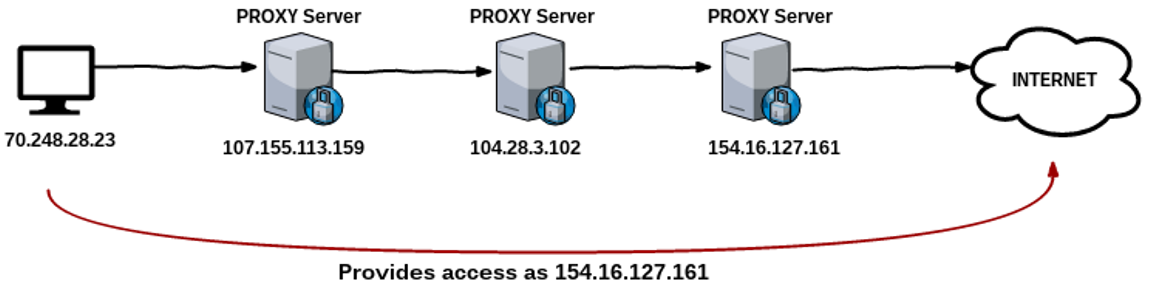
 260
260EVADE USING PROXYCHAINS
EVADE USING PROXYCHAINS:- Whenever attacker attacks in any network, all traffic of the attacker can be logged which can reveal the identity...
-
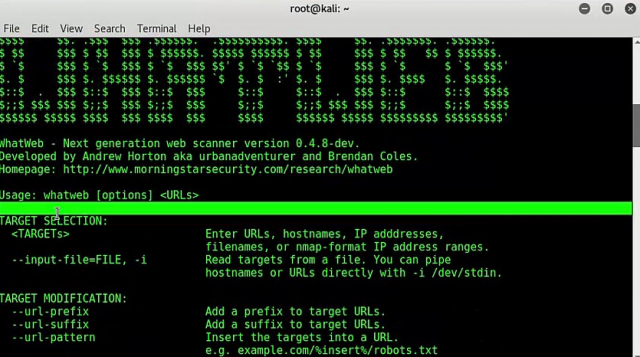
 265
265What is that website – whatweb
WHATWEB:- Whatweb is a next generation information scanner. Its name speaks “what is that website”. According to ethical hacking expert of International Institute...
-

 273
273How to find, is link malicious/URL or not
AUTOMATER:- Automater is a tool to analyze URL, IP, MD5 hash for intrusion analysis. Automater scans the given target by using the...
-

 202
202Scan your LAN for vulnerabilities
NETBIOS ENUMERATOR:- Netbios was suggested that how to use remote network support. Netbios enumerator basically scans the range of IP addresses that...
-
 354
354Scan Joomla websites using Joomscan
Joomscan is a web vulnerability scanner used to detect command execution, sql injection and other web application attacks. As name suggest, joomscan...
-

 352
352Create wordlist from Twitter using Twofi
TWOFI:- Twofi was written by Robin Wood at DigNinja. This tool can use to grab the contents of the user’s or company’s...
-
 235
235Footprinting a target with datasploit
DATASPLOIT:- Datasploit is a tool used in footprinting a target or defending target. It allows you to collect relevant information about the...






