Tutorials
-

 302
302All-New App Store For Hackers, Kali NetHunter
Many times pentesters/ security researchers needs to scan URLs or they need to do penetration testing immediately. For that pentesters cannot use...
-
 413
413Turn Any Android Device Into An Pentesting Device
Pentesters/ security researchers uses many devices for testing their hacking skills or finding new bugs in any web application. Mostly users uses...
-
 330
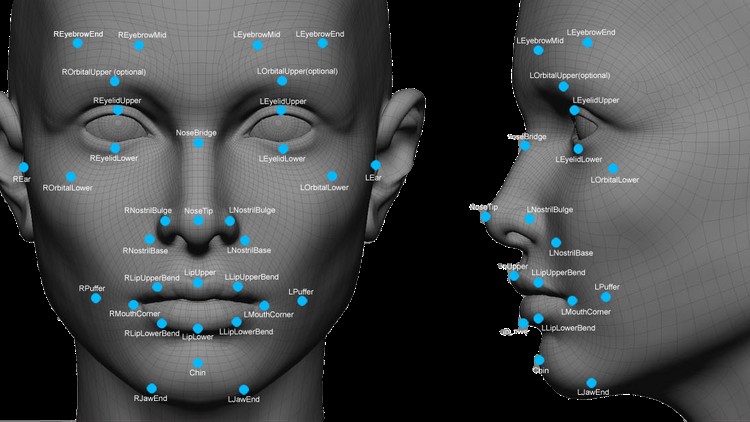
3308 methods for bypassing surveillance cameras and facial recognition software
Facial recognition systems are becoming more sophisticated. When we post a photo on Facebook accompanied by our closest friend, it is almost...
-

 349
349How to Secure any Linux Server | Automated Server Hardening script
There are many open source developers who want to show their skills by developing web applications. Every developer tries to show something...
-

 460
460How to Check if your Mobile phone is hacked or not?
Mobile has become more important part of our life. No one can live without there mobile devices. Users spend most of the...
-
 281
281Check If Your WhatsApp is Hacked Or NOT ?
WhatsApp, a very popular mobile application used for chatting, sharing different types of files. It is estimated, as of 2018 WhatsApp has...
-
 473
473How to analyze USB Traffic
Everyone would have well known with capturing network packets using analyzer tools. But very few have known with capturing with USB packets....
-
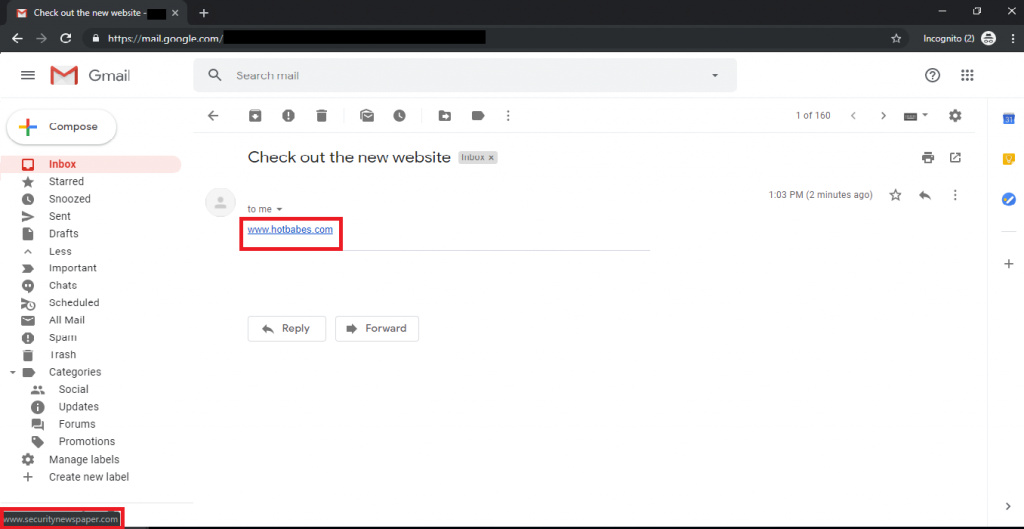
 334
334HOW DO YOU CHECK THAT A WEBSITE IS UNSAFE?
Whenever you opens your email id, you can probably see lots of unknown email with unknown URLs. Everyone wants to open such...
-
 323
323Having problem with Windows 10 Updates? Disable in 2 minutes
Regular updates of any operating system is an good maintenance option. It not only keeps computer from malware attacks, but also gives...
-

 578
578How to open unknown files that have malware in Windows 10 with Sandbox
According to experts in security audits, from the May update of 2019 Windows Sandbox is available for Windows 10 system administrators. This...
-
KillShot to hack any website
The KillShot tool can crawl target web applications and find backend web technologies, identify CMS (Content Management System) in use, and scan...
-
Talk secretly with your friends – Everything about Steganography
Privacy is everything what users should aware off. Every users wants to hide their sensitive information on the internet. Many time when...
-
 306
306Solution to spamming, Check any Unknown Email ID existence
Email spamming is most common from last 10-20 years. There are many individual or groups of attackers who spread malicious content by...
-
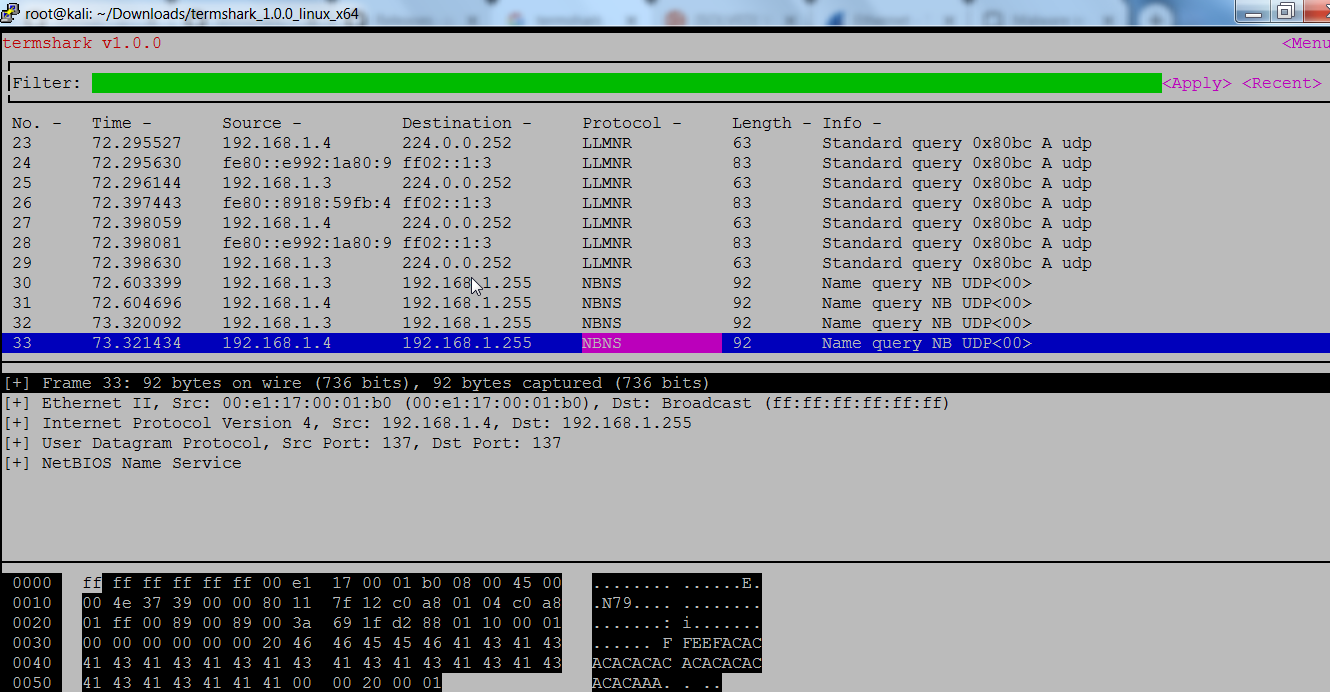
 303
303Light weight Packets Analyzer is here!
There are many tools used in by network administrator to scan network. Continuous network scanning is done to check if any malicious...
-
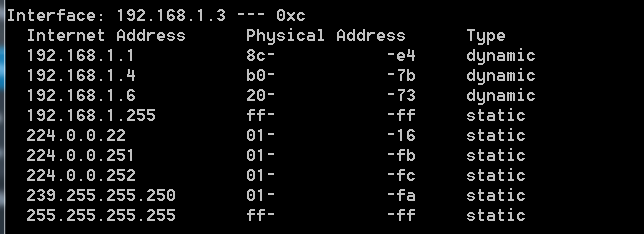
 207
207Smart way of discovering computer on network using ARPING
Earlier we have shown many scanning tools where you can gather lot of information about your target, in internal network or few...
-

 402
402TOP 5 Tools Used By Cyber Criminals Recently
Cyber crime is taking next level of steps for taking control on digital world. Research done by ethical hacking researcher of International...
-

 388
388Find Details Of any Mobile Number, Email ID, IP Address in the world (Step By Step)
OSINT (Open Source Intelligence) is way to collect data from public sources. There are many tools & techniques which are capable of...
-

 226
226Convert any Malicious IP Into URL to HACK YOUR FRIEND
Phishing attacks are very common these days. Most large companies face phishing attacks. International Institute of Cyber Security ethical hacking course includes...
-

 874
874Send fake mail to hack your friends
Social engineering is an trick to enter credentials on malicious web pages by manipulating human interaction with basic level of security. According...
-

 330
330TOP 6 Hacking mobile Apps – must have
Android has become a top mobile operating system. International Institute of Cyber Security has been constantly updating users on the new android...
-
 478
478Hack Whatsapp account of your friend
Social Engineering attacks still works. Most of the attackers do use social engineering methods to trick targets. According to ethical hacking researcher...






