A Ukrainian hacking group ”Pravyy Sector” has breached the servers of Central Ohio Urology Group (COUG) and leaked a trove of data and by trove we mean TROVE!!
A group of Ukrainian hackers going by the handle of Pravyy Sector has contacted HackRead with a data breach and it’s shockingly massive. It happened yesterday on Twitter when Pravyy Sector claimed to have hacked into the server of Central Ohio Urology Group (COUG) and stole a massive amount of highly confidential data and uploaded all stolen files on Dropbox before leaking it online for all to view.
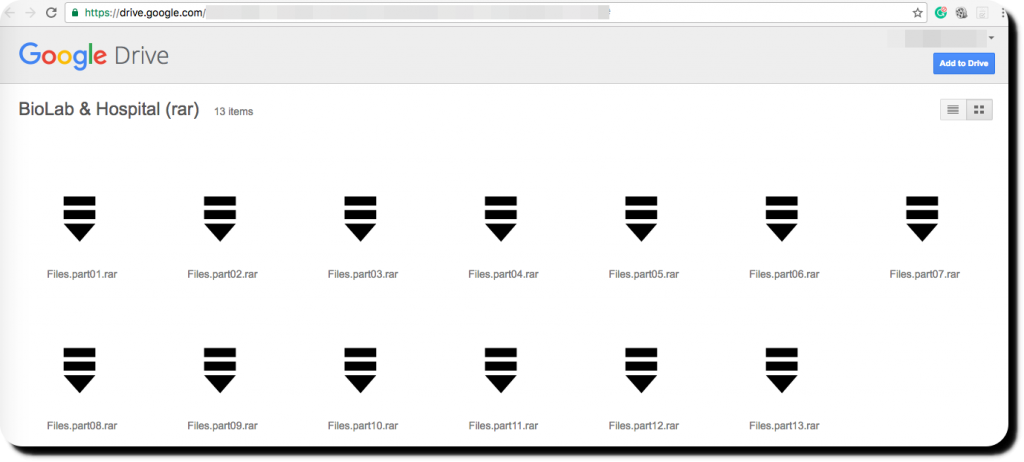
13 files contain 223GB of leaked data from COUG available for public view and download
COUG is one of the largest urology practices in Ohio. With 28 urologists working in the major hospital systems in Central Ohio.
We requested the Israeli data mining Hacked-DB to scan the data and at first sight, they have confirmed the data is massive, stating that ”this is the Hacking Team sort of data breach, so it is huge and it will take a while to come up with complete results.”
Hacking Team is an Italian firm known for providing malware and spyware to governments and regimes around the world before getting hacked and losing its licence in April 2016.
Here’s what the researchers have found till now:
Hacked-DB has dedicated three of its cyber analysts Yogev Mizrahi, Atar Kochavi and Oren Yaakobi to scan the data and until now they have found Architecture topology designs of the network, terminal servers overview details, data information flow, and process, firewall configuration details, payment notices, remote app shortcuts with server details without the need to enter a password, x-ray files, document files with user and passwords to access servers.
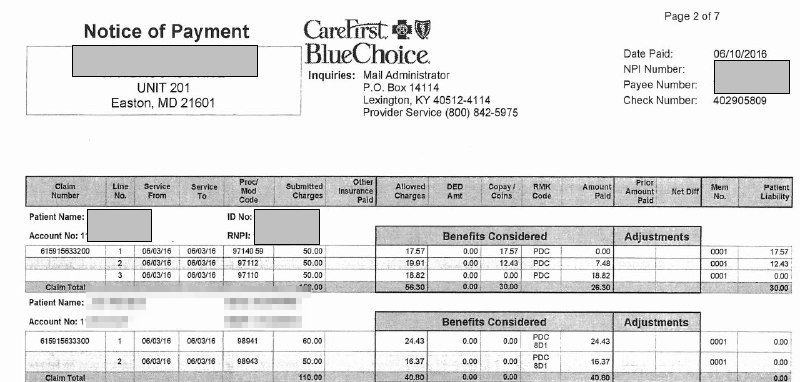
Payment details screenshot
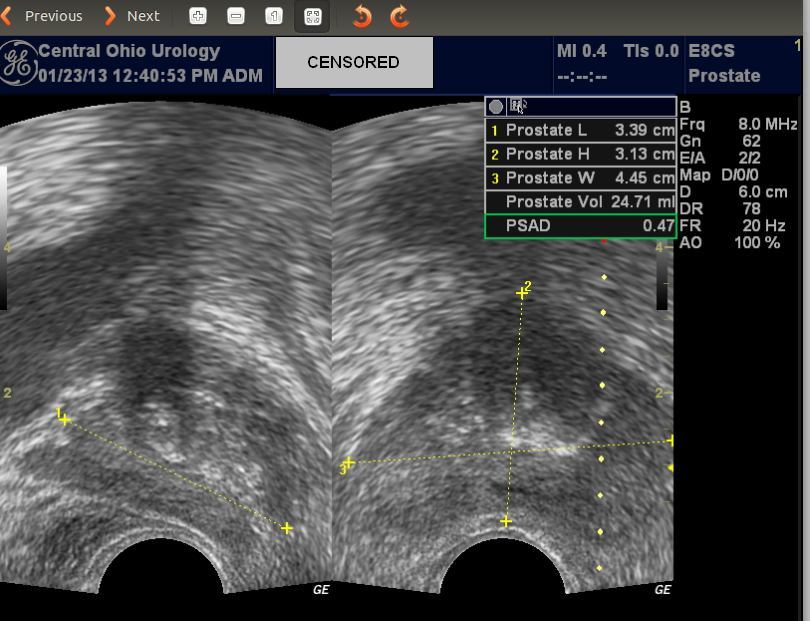
Screenshot of patient’s ultrasound from the leaked data
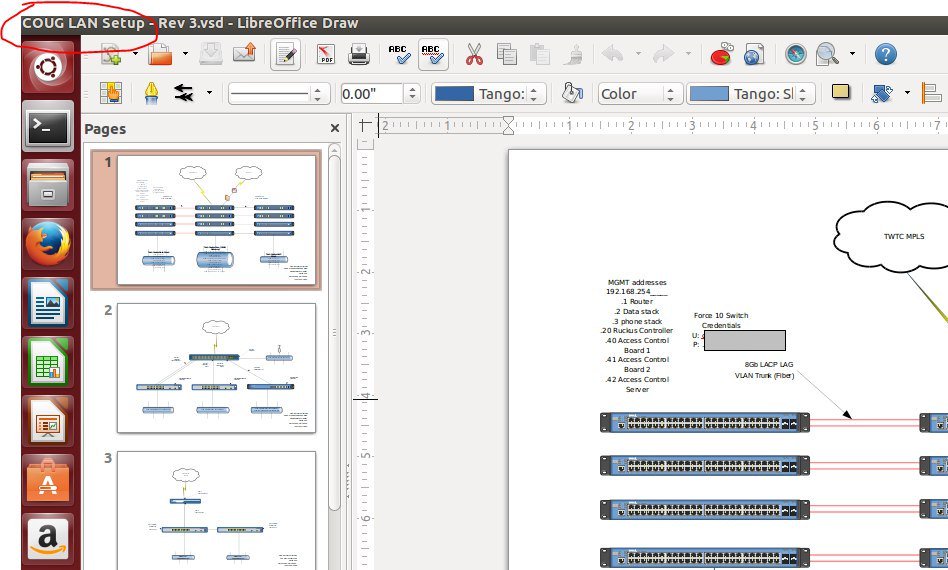
Coug’s LAN setup settings publically available at the moment
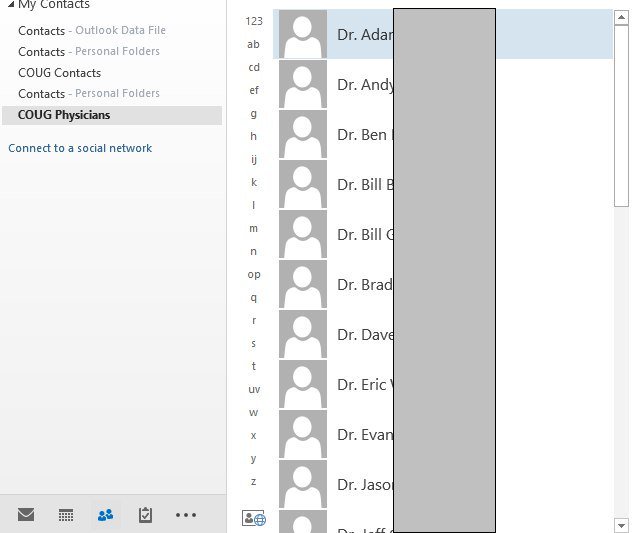
One of the PST files shows details about COUG Physicians
There are 401,828 files within the data breach including 16,646 text files, 1,212 ZIP files, 13 RAR files, 108 SQL files, 130 CSV files, 10 BAK files, 33,841 DOC/Docx files, 150,325 XLS/XLSX files, 8 video files, 64,312 pdf files, 1,234 jpg files, 4264 TIF files and 9,327 .crypt files.
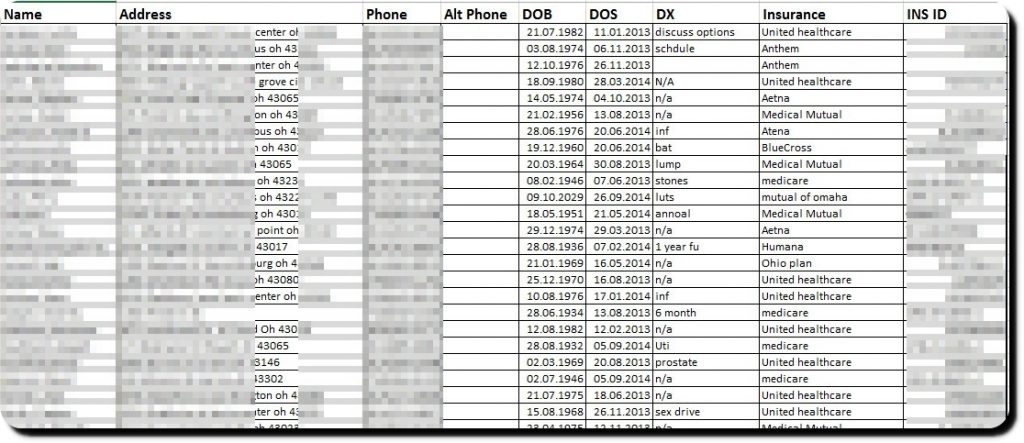
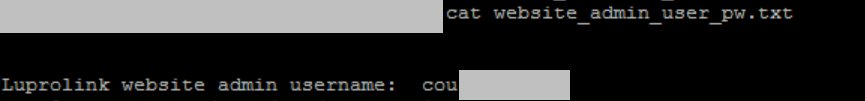
At the moment, researchers are working on scanning payment info and patients medical data stored in COUG’s server with very poor security measures. Researchers at Hacked-DB have also located user names and clear text password within text files and documents. That’s not all; the entire architecture design of the data center is also among the leaked data with absolutely no security whatsoever.
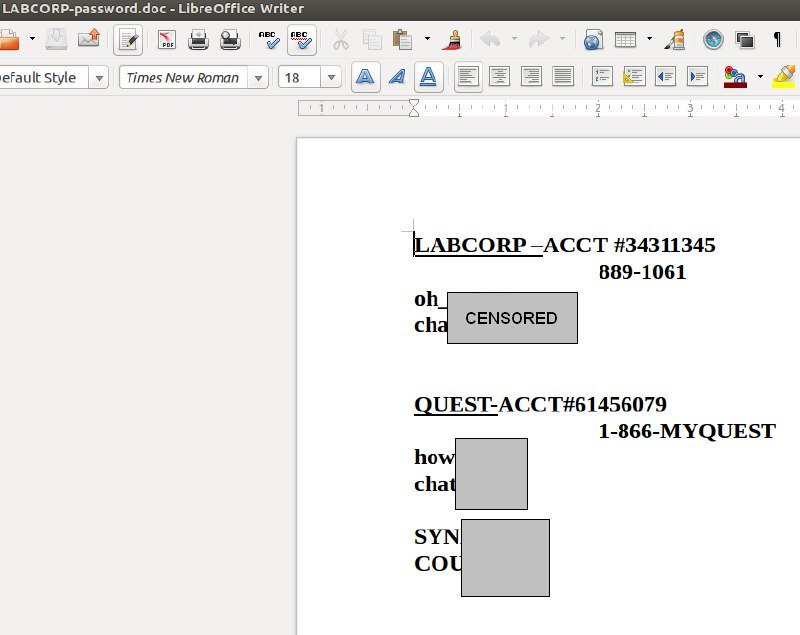
Some of the patient medical records include complaint/reason history of present illness, active medications, allergies, past medical/surgical history, diagnostics history and family history.
Statement from Hacked-DB:
Oren Yaakobi of Hacked-DB commented on the data breach according to which ”Based it seems that the data was taken from the storage system of the hospital, which may be executed with the cooperation of internal employee. The exposed data includes network designs, detailed communication data flow, login details to various servers, internal hospital documents, payments info, medical records and history of patients, x-rays, internal and external communication between co-workers and clients, PST files, backup files and more.”
”This kind of security breach endangers the hospital reputation and may lead to lawsuits, as this is a serious violation of handling and maintaining the PII and medical records of patients in a secure manner,” Yaakobi added.
We have contacted COUG and waiting for their response.
Expert comment from Scott Gordon, chief operating officer at FinalCode:
“Healthcare organizations are prime targets for hackers, and ensuring adequate protection of sensitive information across data types, users and systems is paramount. The breach of the Central Ohio Urology Group illustrates how healthcare system file collaboration has become the new data leakage frontier,” said Scott Gordon, chief operating officer at FinalCode. “Given HIPAA and HITECH legislation, providers need to assume incidents will occur. A proactive stance, invoking available encryption and usage control on files such as the more than 100,000 exposed Microsoft and Adobe documents in the Ohio breach, would have secured this regulated data and enabled breach disclosure safe harbors.”
If you are surprised with the above information have a look here at the previous data breach in which a hacker was selling medical records of 655,000 US-based patients
By the name of it the ”Pravyy Sector” sounds like a group with far-right political ideology as group’s online handle ”Pravyy Sector” means Right Sector which is a far-right Ukrainian nationalist political party that originated in November 2013 as a paramilitary confederation at the Euromaidan revolt in Kiev, where its street fighters fought against riot police. The coalition became a political party on 22 March 2014, at which time it claimed to have perhaps 10,000 members.
This is not the first high-profile hack from Pravyy Sector. A couple of months ago; the same group claimed responsibility for hacking Polish ministry of defence server and demanded $50 000 transferred to specified account or bitcoin address in exchange for not leaking the data.
We will update you with more analysis soon:
As mentioned above; the COUG data is under analysis so be patient and we will share more exclusive findings within a few hours!
Update (8:36 PM Thursday, August 4, 2016, Coordinated Universal Time (UTC):

As promised here we are with part 2 of Central Ohio Urology Group (COUG) data breach, thanks to Hacked-DB again and here’s what was found:
Further analysis of the data that was exposed on Google Drive shows a file containing email archives from the Cheif Administrator Officer, risk assessment documents, company security policies, above 100 HR policies and procedures including CVs, tape records of doctors, hire and termination dates, salary and more.
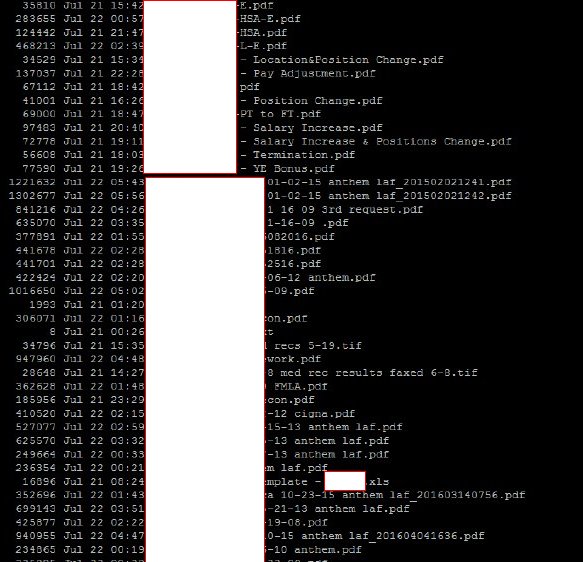
Screenshot of the leaked files from the HR department
Furthermore, the researchers found bank account details, signature, date of employee termination, telephone numbers, mobile numbers, marital status, height and weight, weekly hours of work, salary increase by year, position changes, termination of work date, bonuses details, personal and sensitive documents of employees from the human resource department including social security and personal identification numbers.
The researchers have also detected more than 250 employee details with information as described above, in addition to the analysis user names and clear text passwords of the VPN connection service used by the firm are also among the leaked data.
We contacted COUG through their website a couple of days ago but there was no response from them whatsoever.