GitLab Inc. is an open-core corporation that runs GitLab, a software package that may be used to build, protect, and administer software. GitLab is operated by GitLab Inc. Large DevOps and DevSecOps projects may benefit from using GitLab since it provides a repository for open source code and a platform for collaborative software development. GitLab does not charge users on an individual basis. GitLab is a platform that provides a space for the online storage of code as well as tools for bug tracking and CI/CD.GitLab Community Edition (CE) and GitLab Enterprise Edition (EE) have received an update to version 16.0.1 from the firm. GitLab Community Edition and Enterprise Edition have both been found to have a problem, although version 16.0.0 is the only one that affects. When an attachment is present in a public project that is nested inside at least five other groups, it is possible for an unauthenticated malicious user to exploit a path traversal vulnerability and access arbitrary files stored on the server. The Critical Vulnerability Scoring System assigns a score of 10.0 to this vulnerability.
Exploitation of the CVE-2023-2825 vulnerability might result in the disclosure of sensitive data, such as confidential program code, user passwords, tokens, files, and other private information.
This requirement lends credence to the hypothesis that the problem is associated with the manner in which GitLab handles or resolves paths for connected files that are nested inside many levels of group hierarchy. However, owing to the severity of the issue and the fact that it had just recently been discovered, the vendor did not provide a great deal of information at this time.
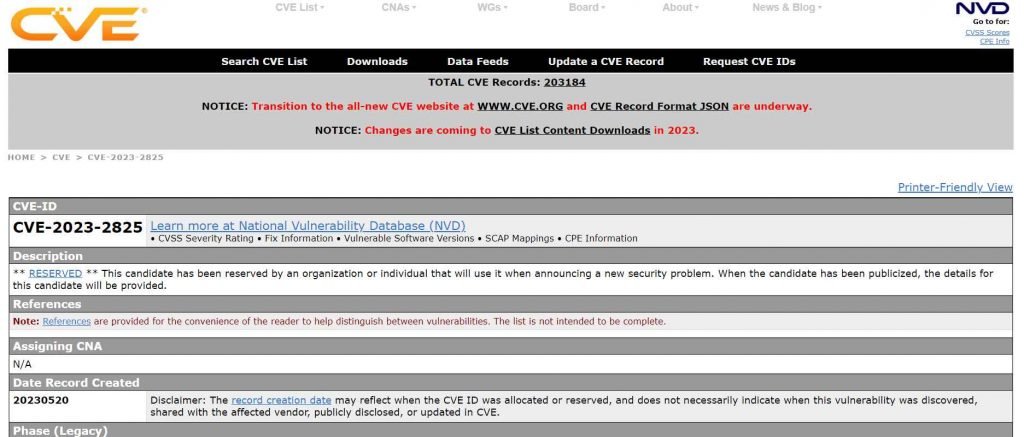
Instead, GitLab emphasized the need of promptly implementing the most recent security update as soon as it was made available. GitLab.com is already using the updated version of the software.
The fact that the vulnerability cannot be exploited until certain circumstances are met, such as their being an attachment in a public project that is nested inside at least five groups, which is not the structure that is used in all GitHub projects, is a factor that helps to reduce the severity of the issue.
Despite this, it is strongly suggested that anybody using GitLab 16.0.0 upgrade as soon as possible to version 16.0.1 in order to reduce the potential for danger. There is currently no way around this problem, which is really unfortunate.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.