A sweeping and “highly active campaign” that originally set its sights on Myanmar has broadened its focus to strike a number of targets located in the Philippines, according to new research.
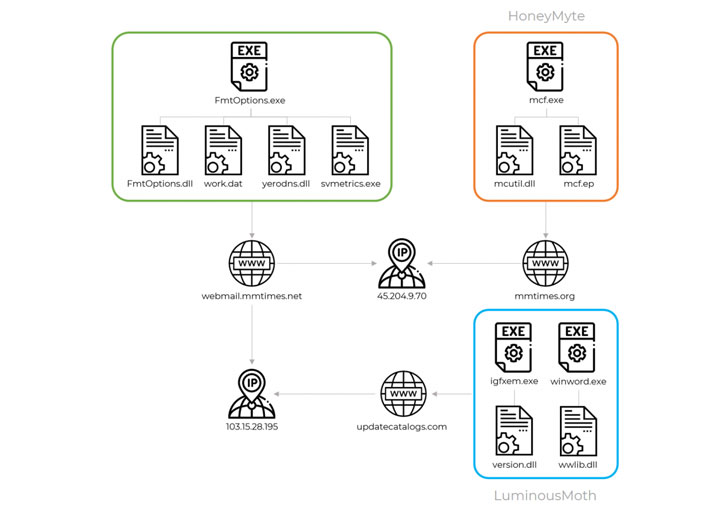
Russian cybersecurity firm Kaspersky, which first spotted the infections in October 2020, attributed them to a threat actor it tracks as “LuminousMoth,” which it connected with medium to high confidence to a Chinese state-sponsored hacking group called HoneyMyte or Mustang Panda, given its observed victimology, tactics, and procedures.
About 100 affected victims have been identified in Myanmar, while the number of victims jumped to nearly 1,400 in the Philippines, although the researchers noted that the actual targets were only a fraction of the initial numbers, including government entities located both within the two countries and abroad.
The goal of the attacks is to affect a wide perimeter of targets with the aim of hitting a select few that are of strategic interest, researchers Mark Lechtik, Paul Rascagneres, and Aseel Kayal said. Put differently, the intrusions are simultaneously wide-ranging and narrow-focused, enabling the threat acor to siphon intelligence from high-profile targets.
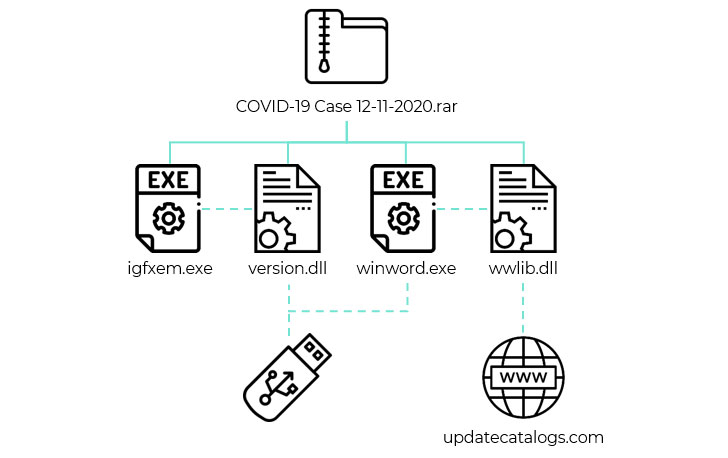
The infection vector used in the campaign involves sending a spear-phishing email to the victim containing a Dropbox download link that, when clicked, leads to a RAR archive that’s designed to mimic a Word document. The archive file, for its part, comes with two malicious DLL libraries (“version.dll” and “wwlib.dll”) and two corresponding executable files that run the malware.
Upon successfully gaining a foothold, an alternative infection chain observed by Kaspersky leverages removable USB drives to propagate the malware to other hosts with the help of “version.dll”. On the other hand, the purpose of “wwlib.dll” is to download a Cobalt Strike beacon on the compromised Windows system from a remote attacker-controlled domain.
In some instances, the attacks incorporated an extra step wherein the threat actor deployed a post-exploitation tool in the form of a signed-but-rogue version of Zoom video conferencing app, using it to hoover sensitive files to a command-and-control server. A valid digital certificate was used to sign the software in an effort to pass off the tool as benign. Also spotted on some infected machines was a second post-exploitation utility that steals cookies from Google Chrome browser.
LuminousMoth’s malicious cyber operations and its possible ties to Mustang Panda APT may also be an attempt to shift tactics and update their defensive measures by re-tooling and developing new and unknown malware implants, Kaspersky noted, thus potentially obscuring any ties to their past activities and blurring their attribution to known groups.
“APT actors are known for the frequently targeted nature of their attacks. Typically, they will handpick a set of targets that in turn are handled with almost surgical precision, with infection vectors, malicious implants and payloads being tailored to the victims’ identities or environment,” Kaspersky researchers said.
“It’s not often we observe a large-scale attack conducted by actors fitting this profile, usually due to such attacks being noisy, and thus putting the underlying operation at risk of being compromised by security products or researchers.”