The infamous APT39, the alleged Iran-funded cyber espionage team has been identified by FireEye as actively targeting Europe, USA, Australia, South Korea and the Middle East region for their espionage campaign. “APT39 marks the fourth Iranian cyber threat actor that FireEye has elevated to the designation Advanced Persistent Threat (APT). APT39’s focus on personal information likely supports the planning, monitoring, and tracking of intelligence operations that serve Iran’s national priorities. APT39’s focus on the telecommunications and travel industries suggests its intent to collect proprietary or customer data for purposes that serve strategic requirements or create additional accesses and vectors to facilitate future campaigns,” explained Benjamin Read, Sr. Manager of FireEye, a cybersecurity consulting firm.
APT39 has been known for quite some time in operating in many countries in order to gather personally identifiable information, using web-based apps with vulnerabilities known only by a selected view, also known as zero-day exploits. In their official blog, FireEye disclosed the operations of APT39 in connection to another group known only under the alias ‘Chafer’, allegedly the Iranian espionage group collaborated with another party in order to increase their presence in the field of global espionage.
“APT39 primarily leverages the SEAWEED and CACHEMONEY backdoors along with a specific variant of the POWBAT backdoor. While APT39’s targeting scope is global, its activities are concentrated in the Middle East. APT39 has prioritized the telecommunications sector, with additional targeting of the travel industry and IT firms that support it and the high-tech industry,” emphasized FireEye.
In the below figure released by FireEye, details the exact countries in the world where this collaborative group is actively detected:
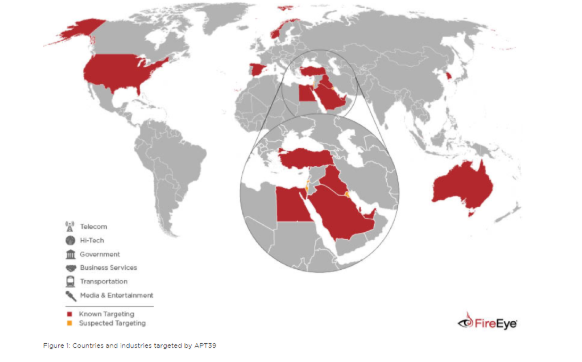
From the perspective of APT39 and their collaborators, the most productive targets are telecommunications, tech industry, media, transportation, services, and government institutions. These sectors hold a lot of information on their current and prospective customers. Also, being a state-actor, APT39 group is interested of spying on governments of other nations. The team knows how effective collaborative campaigns are instead of doing it alone.
“We have moderate confidence APT39 operations are conducted in support of Iranian national interests based on regional targeting patterns focused in the Middle East, infrastructure, timing, and similarities to APT34, a group that loosely aligns with activity publicly reported as “OilRig”. While APT39 and APT34 share some similarities, including malware distribution methods, POWBAT backdoor use, infrastructure nomenclature, and targeting overlaps, we consider APT39 to be distinct from APT34 given its use of a different POWBAT variant. It is possible that these groups work together or share resources at some level,” added FireEye.
APT39 is a knowledgeable group and uses a lot of tools to perform their espionage. Many of the same tools they use are also used by legitimate system administrators for maintaining computers:
- Remote Desktop Protocol (RDP)
- Secure Shell (SSH)
- RemCom
- PSExec
- XCmdSvc
They also use internally-develop tools using SOCKS5 proxies: BLUETRIP, REDTRIP, AND PINKTRIP. They love using compression in order to hide the stolen information from users, using zip compression tools. “There are some indications that APT39 demonstrated a penchant for operational security to bypass detection efforts by network defenders, including the use of a modified version of Mimikatz that was repacked to thwart anti-virus detection in one case, as well as another instance when after gaining initial access APT39 performed credential harvesting outside of a compromised entity’s environment to avoid detection,” concluded FireEye.









