An article published by The Guardian in 2011 on the topic Cybercrime: is it out of control? received a nasty response from a hacker who inserted a malicious URL inside one of the syndicated link embedments in the article.
The article published by the website was headlined “Cybercrime: Is it out of Control?” and the hacker gave a proper response to the writer by inserting a malicious URL which directed the user to a page having Angler Exploit Kit malware.
This was found by researchers (J.Gomez, Kenneth Hsu and Kenneth Johnson) from a security firm “FireEye”. Though, they found this on 1st December but published their findings in a blog post on 9th December. The blog post about the exploit said:
“When the syndication link is loaded in the background, readers are eventually redirected to Angler’s landing page via injected HTML that crafts the request to the Angler landing page”
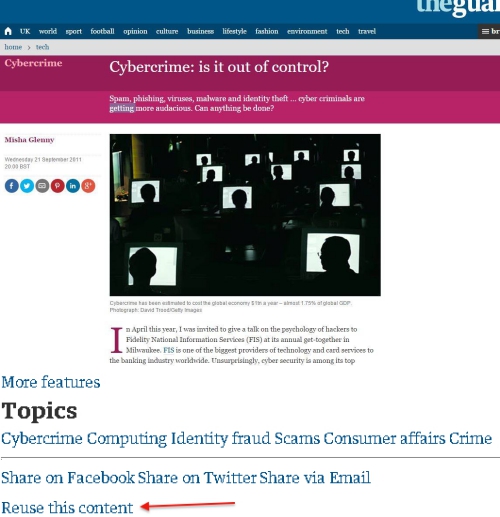
Image Source: FireEye
Furthermore, the researchers noted the vulnerability in VBScript in the attack and also a Flash exploitation.
[fullsquaread][/fullsquaread]
“Angler unconditionally attempted to exploit a popular vulnerability CVE-2014-6332. This is a memory corruption vulnerability in Windows Object Linking and Embedding (OLE) Automation that can be triggered through VBScript with Internet Explorer”.
Researchers also noted that this exploit was based on proof-of-concept which is publicly available. Techniques used in this attack are also based on the same concept.
The Angler Exploit Kit is very difficult to track down as it continually looks out for any security programs and if it founds any it quickly force abandons the attacks before the program notifies or runs a suitable docile script.
The Angler exploit role in this attack is what it is designed for i.e. to exploit any vulnerabilities in the browser or any other plugins in the browser once it finds the vulnerability it exploits by delivering the payload.
Guardian’s officials, when reached to comment on these findings, said, “We are aware of FireEye’s claims and are working to rectify the issue as soon as possible.”
[src src=”Source” url=”https://www.fireeye.com/blog/threat-research/2015/12/cybercrime-news.html”]FireEye[/src]
[src src=”Featured Image Via” url=”http://www.raidious.com/wp-content/uploads/2015/08/Dollarphotoclub_76939568.jpg”]Raidious[/src]