Researchers have found Locky Ransomware being used against healthcare industry in the United States — It’s time for the cyber security firms to come up with proper security measures!
Medical centers and hospitals in the United States have become lucrative targets for malicious actors and scammers. In the latest of these scam campaigns to be identified by the FireEye security research team, the highly advanced Locky Ransomware has been utilized by cyber criminals.
Locky Ransomware uses the file encrypting software to penetrate and infect the entire system within a short span of time. It is being regarded as an utterly notorious ransomware because the victims are asked for a hefty ransom. A majority of the targets of this ransomware are hospitals and most of the attacks occurred in the first half of August 2016.
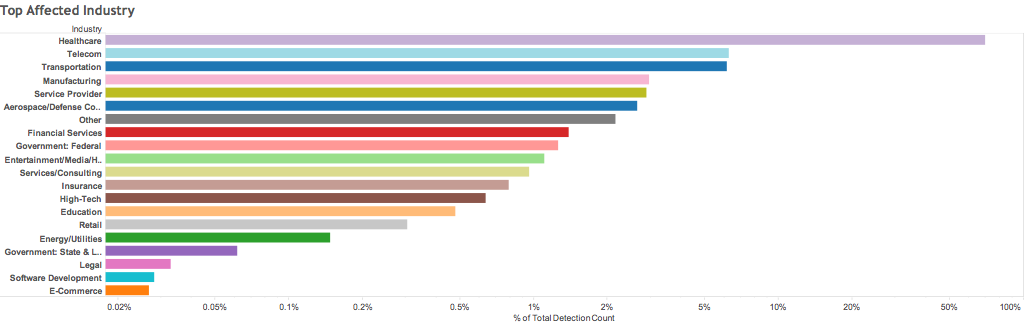
List shows healthcare and telecom industries are mostly targeted!
Related: How to secure your cyber infrastructure from threats like ransomware?
Wondering why hospitals are being targeted?
That’s because IT plays an important role in the day-to-day activities at hospitals and they also have critically important data related to the patients and staff members. This sort of information is useful for cybercriminals while the extensive use of IT at medical centers presents scammers an exclusive opportunity to get their infected software distributed to a wider audience.
The ransom asked by the victims is usually in Bitcoin, the digital currency. Previously, a hospital in Southern California was asked to pay 9000 BTC ($3.6M) ransom because of Locky ransomware infection.
It has been identified by security researchers that there is a definite hike in the distribution of phishing emails to spread Locky ransomware campaign. FireEye has also discovered that the number of Locky ransomware downloads is also increasing at a constant pace while the attackers are constantly changing their techniques. Therefore, users are required to remain alerted so as to avoid getting victimized by this ransomware.
According to Rong Hwa Chong from FireEye the latest campaign reminds us that users need to be cautious “cautious when it comes to opening attachments in emails or they run the risk of becoming infected and possibly disrupting business operations.”
Should victim pay a ransom?
In July 2016, one of the Nascar race teams witnessed their chief’s computer getting hacked with a ransomware malware locking up his files and demanding ransom in Bitcoin. When contacted FBI, the team was told to pay the ransom and that’s what they did.
[fullsquaread][/fullsquaread]
However, now good news is that IT security giants Intel and Kaspersky with the assistance of Europol and Dutch Police have developed an anti-ransomware portal called ‘No More Ransom’ to help users against the growing threat of ransomware and recover their data for free in order to discourage the trend of paying ransom for decryption of their encrypted data.