Files of over 20 Games Encrypted by TeslaCrypt Ransomware – Out of 185, 50 file extensions are game-oriented.
TeslaCrypt is a crypto-ransomware that has targeted more than 50 custom game files of at least 20 famous products for encryption.
Drive-by attacks are used for delivering the threat through Flash Player (CVE-2015-0311) whereas Internet Explorer (CVE-2013-2551) exploits the Angler attack tool.
MUST READ: US Police Dept Pays Crypto-Malware Ransom to retrieve sensitive records
Famous Game Titles Hijacked for Ransom
Emsisoft’s Fabian Wosar originally discovered TeslaCrypt. Wosar noticed that attackers offered two types of payment to the victims; first one is to fulfil the demand of $1,000 sent via PayPal My Cash and the other asked for $500 in bitcoin digital currency.
Kotov says that the payment procedures, regardless of the type, are all run through a website on Tor (The Onion Router).
Single-player desktop titles the data of which was encrypted by teslaCrypt include: Call of Duty, Star Craft 2, Minecraft, Half-Life 2, The Elder Scrolls (Skyrim-related files), WarCraft 3 and Assassin’s Creed.
List of online games include: Warcraft, League of Legends and World of Tanks.
MUST READ: Fake Google Chrome update leads to CTB Locker/Critroni Ransomware
Moreover, Kotov revealed that the malware also affects objects belonging to Steam platform, RPG Maker (a game development software), Unreal Engine and Unity 3D.
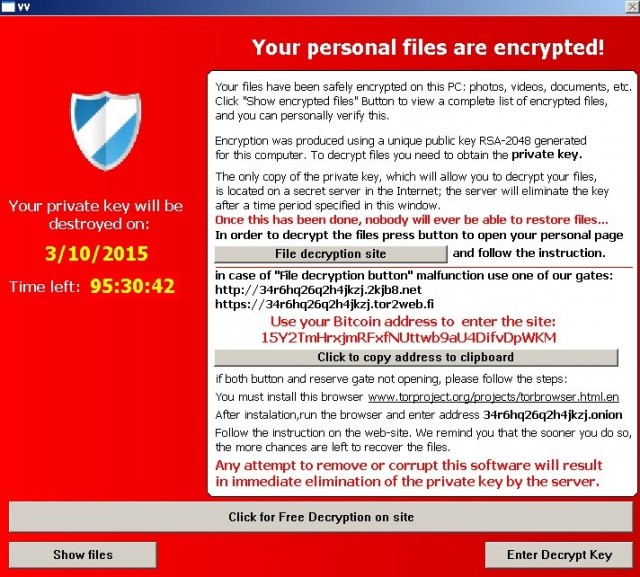
Though the ransom notice promotes that strong encryption (2048-bit RSA key) has been employed for avoiding unlocking of the files but security researchers found no proof of this claim.
Conversely, researchers carried out an introductory analysis and couldn’t found answers to some of their queries such as they identified a file names “key.dat” but its contents are unidentifiable.
Similarities between TeslaCrypt and Cryptolocker
An analysis, steered by Bromium security company’s researchers, revealed that Teslacrypt targeted around 185 extensions and it relies upon the AES encryption algorithm for locking down the data.
MUST READ: Ransomware: Cyber-hijacking Malware now has a new deadly face
The file types of games that have been hijacked by this threat include saved games, user profile data, mods and maps, etc. However, some games also offer users the option of storing the data on an account that is maintained on their server. But this doesn’t happen in all situations.
According to researchers, the threat appears similar to Cryptolocker. It was the infamous ransomware delivered and distributed by the GameOver Zeus botnet. It was disrupted by law enforcement and private security firms in 2014.
MUST READ: Beware of New Ransomware Scams Targeting Android Devices!
Vadim Kotov, Bromium researcher, states that the similarities between these two crypto-malware variants aren’t many and just 8% similarity can be observed, which indicates that cybercriminals are only trying to benefit from Cryptolocker’s popularity.