Last Wednesday the Internet was full of news reports regarding a new sophisticated phishing scam using Google Docs to trick users into giving away their login credentials by opening a fake Google document. The scam highlighted the importance of how people should be careful while clicking on an unknown link.
The good news is that Google was quick to shut down the whole scam within a few hours. In a statement released later in the day, Google said it had been able to stop the campaign, which reportedly affected less than 0.1 percent of its users, within about an hour. However, the bad news is that within those few hours it did a lot of damage.
We’ve addressed the issue with a phishing email claiming to be Google Docs. If you think you were affected, visit https://t.co/O68nQjFhBL. pic.twitter.com/AtlX6oNZaf
— Google Docs (@googledocs) May 3, 2017
According to a report by ABC News, the Minnesota state’s chief information security officer Christopher Buse said that “2,500 state employees received the phishing email, altogether they received 13 different variants of the attack. Dealing with it cost taxpayers nearly $90,000, mainly because of the amount of time state employees spent dealing with the attack as opposed to their normal day-to-day jobs.”
“I estimated 3 minutes of time per employee, and it may be much more than that in many cases,” Buse added.
How the Google Doc Phishing scam worked:
Just got this as well. Super sophisticated. pic.twitter.com/l6c1ljSFIX
— Zach Latta (@zachlatta) May 3, 2017
How can you protect yourself from phishing attacks?
Protecting yourself from phishing attacks is actually an easy job. All one has to do is be vigilant and keep an eye who’s sending the email and what the sender is forcing you to do. For example, recently we exclusively reported two highly sophisticated phishing campaign targeting Facebook and iCloud users. The Facebook scam tricked users into believing that their account had been disabled and to get access back they needed to click on a link but doing so asked them to enter their credit card data and Facebook login credentials.
In the iCloud scam, users were tricked into believing that their Apple ID was logged in from a different device and for security reason users need to click on a link. The link took users to a phishing website asking their credit card data, personal details, a government issued ID card and access to their device’s microphone and camera.
Both scams could have been easily identified by the grammar mistakes in the body of both emails. However, it is advisable to look but don’t click the link, check the spelling mistakes in the email, look for threating language, check if the email contains exclamation marks, review the signature of the email, do not download files from an unknown email, copy the subject of the email and search it on Google, you can also copy the phishing link without clicking it and search it on Google or scan it on sites like VirusTotal.
If you are using web browsers like Safari, Opera or FireFox there are chances that these browsers won’t warn you about a suspicious link meanwhile usually Chrome does warn users. For example in the iCloud discussed above the malicious link was already marked as a deceptive site to visit by Chrome browser.
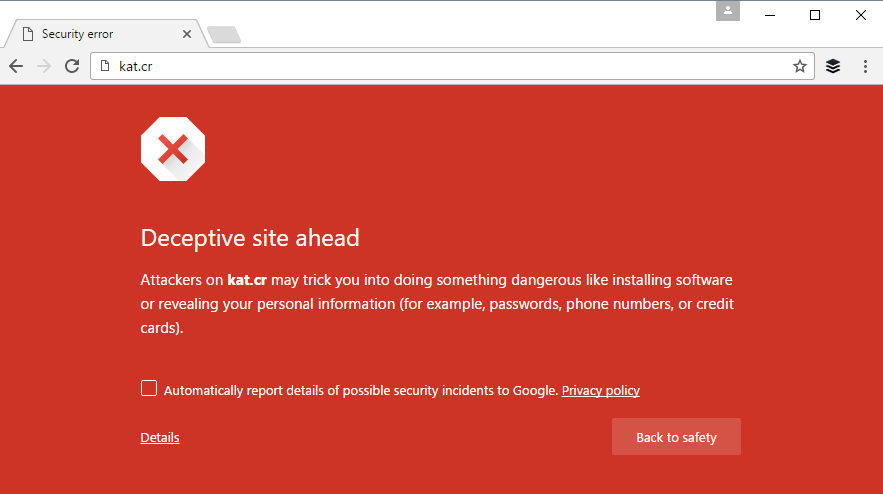
Deceptive warning website message on Kat.cr last year
[fullsquaread][/fullsquaread]
Also, phishing scams targeting PayPal, Facebook, Twitter, iCloud and banks etc are at large where scammers are using highly sophisticated tricks to steal login credentials from unsuspected users. If you have an account on these platforms, it is advisable to log in to your account by entering the web address into your browser’s address bar or via their official app. Stay safe online.
DDoS attacks are increasing, calculate the cost and probability of a DDoS attack on your business with this DDoS Downtime Cost Calculator.