Security researchers over at FireEye have discovered a serious security flaw within the ATM (Automated Teller Machine) that could be exploited by the hackers to infect the machine with a next-generation of ATM malware that have the ability to hold an inserted card inside the machine, and works on the will of hackers.
FireEye suggests that attackers could use this technique to purposely jam your card and “retained to be ejected to the crooks once you walk away asking for help.” This would allow hackers to safely use your account without being noticed.
[must url=”https://www.hackread.com/100-millions-stolen-through-bank-malware/”]Hackers Steal $100 millions+ from US and global banks via Malware[/must]
The malware is codenamed “SUCEFUL” because the researchers found out that developers of this malware had used this keyword at the end of the detected malware, “Backdoor.ATM.Suceful.” Apparently, it is believed that the word “successful” was mistyped by the writers, which resulted in a word “Suceful.”
Malware specifically designed to target ATMs is not new, because security threats in 2013 and 2014 were revealed which were codenamed PadPin and Ploutus and were used by crooks around the world to empty cash stored within the ATMs.
But this new malware SUCEFUL compromises of an advanced threat and is designed to targeted cards inserted by the cardholders.
This malware was uploaded to VirusTotal (VT) from Russia and is seems to be produced on August 25th of this year, which indicates that the malware is recently created and still under development and in the early phase of distribution. Nevertheless, the features retained by this malware are “never seen before” in the ATM malware.
Capabilities Of SUCEFUL Malware
FireEye researchers got hold of the malware and tested it out to find out the real potential of SUCEFUL and what it is capable of and they found that it could:
Read all the data of the credit/debit card, read data from the chip of the debit/credit card, control malware using ATM’s PIN pad, steal physical debit/credit cards on demand, could defeat ATM sensors to avoid detection.
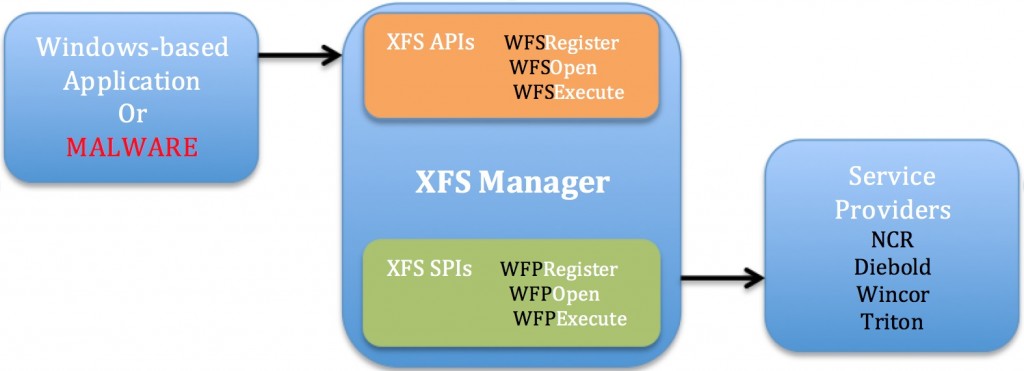
The malware interacts with a middleware known as XFS Manager, part of XFS/WOSA, which is very much similar to the earlier malware Ploutus and PadPin.
In this case, XFS Manager is working as an interface between the malware and all the peripherals equipped in the ATM. As you can see in the illustration below.
As designed in the image above, malware is depending on the XFS Manager and XFS API to communicate with the ATM, this shows that the malware is independent of the vendor and can run transparently on multiple hardware vendors. While XFS SPI is dependent on the vendor in order to provide personalized functionality within the hardware.
These features have made this malware a first of its kind to target cardholders and have the ability to exploit multi-vendor ATMs, which is not only designed to steal the cash from the accounts but also to steal the credit/debit cards.
Watch 2013 presentation by hackers on ATM hacking:
[must url=”https://www.hackread.com/standard-chartered-bank-hacked-money-stole-via-atms/”]Standard Chartered Bank hacked — Hackers stole money Via ATMs[/must]
It is suggested that every ATM user should keep an eye on the machine during transaction, and if any unusual activity is detected then they should not leave the ATM unattended and call the bank immediately to let them know about the issue.
[src src=”source” url=”https://www.fireeye.com/blog/threat-research/2015/09/suceful_next_genera.html”]FireEye[/src]