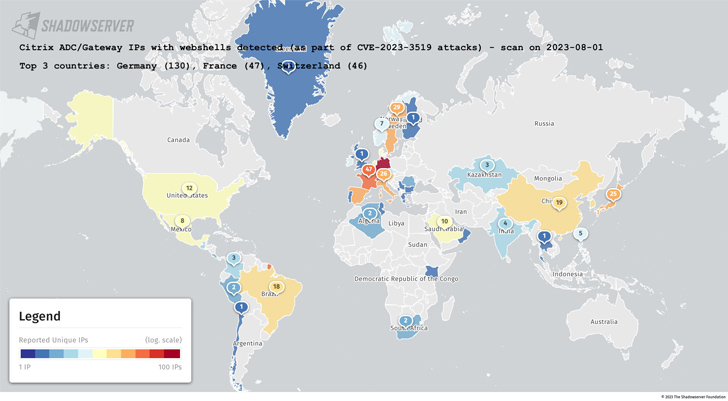
Hundreds of Citrix NetScaler ADC and Gateway servers have been breached by malicious actors to deploy web shells, according to the Shadowserver Foundation.
The non-profit said the attacks take advantage of CVE-2023-3519, a critical code injection vulnerability that could lead to unauthenticated remote code execution.
The flaw, patched by Citrix last month, carries a CVSS score of 9.8.
The largest number of impacted IP addresses are based in Germany, followed by France, Switzerland, Italy, Sweden, Spain, Japan, China, Austria, and Brazil.
The exploitation of CVE-2023-3519 to deploy web shells was previously disclosed by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which said the attack was directed against an unnamed critical infrastructure organization in June 2023.

The disclosure comes as GreyNoise said it detected three IP addresses attempting to exploit CVE-2023-24489 (CVSS score: 9.1), another critical flaw in Citrix ShareFile software that allows for unauthenticated arbitrary file upload and remote code execution.
The issue has been addressed in ShareFile storage zones controller version 5.11.24 and later.
Attack surface management firm Assetnote, which discovered and reported the bug, traced it to a simpler version of a padding oracle attack.
“[Cipher Block Chaining] mode and PKCS#7 padding are the default values for AES encryption in .NET,” security researcher Dylan Pindur said.
“Look at how it behaves when invalid versus valid padding is provided. Does it result in an error? Are the errors different? Does it take longer or shorter to process? All of these can lead to a potential padding oracle attack.”