According to SentinelOne, Iranian hackers have developed a combo of disk wiper and ransomware and their target is Israeli cyberinfrastructure.
The Agrius hacking group has surfaced again, and this time it is causing much more destruction than ever before. According to a research report from SentinelOne, the group has stopped using destructive wiper malware and instead has developed a combo of disk wiper and ransomware.
The malware is dubbed Apostle by SentinelOne, while researchers revealed that Agrius is back in action after launching attacks against Israeli targets in 2020.
Apostle – A Never Seen Before Malware
According to SentinelOne researchers, Apostle is a unique and never-seen-before disk wiper malware disguised as ransomware. It unleashes destructive attacks on different targets in Israel.
Apostle was initially deployed to wipe data, but it couldn’t do so due to a logic flaw in its code. The internal name its developers have given it was wiper-action. But its later version is far more lethal as the bug has been fixed and the malware is equipped with full ransomware functionalities, such as leaving ransom notes in exchange for a decryption key.
Campaign Tied to Iranian Government
Researchers have categorically stated that this campaign and Agrius hacking group are state-sponsored, and the Iranian government is involved in this campaign. This analysis is based on the servers Apostle reports to and its code.
The ransom note that researchers recovered revealed that Apostle was used against a UAE-based facility, but its main target was Israel.
SentinelOne researchers wrote in their blog post published Tuesday that it is difficult to determine the actual intentions of the threat actors.
“The usage of ransomware as a disruptive tool is usually hard to prove, as it is difficult to determine a threat actor’s intentions. Analysis of the Apostle malware provides a rare insight into those kinds of attacks, drawing a clear line between what began as a wiper malware to fully operational ransomware.”
About Agrius
Agrius group uses a custom-made toolset and readily available security software to deploy either a custom wiper-cum-ransomware or a destructive wiper variant. But unlike other ransomware gangs like Conti or Maze, Agrius isn’t motivated by money, and its primary focus is on data destruction and cyber espionage.
In some attacks, they have used a wiper only. They pretend to have encrypted data to extort victims. However, the data is already destroyed, which shows they intentionally disguise their activities as ransomware attacks but actually engage in destructive attacks against targets in Israel.
How Attack Works?
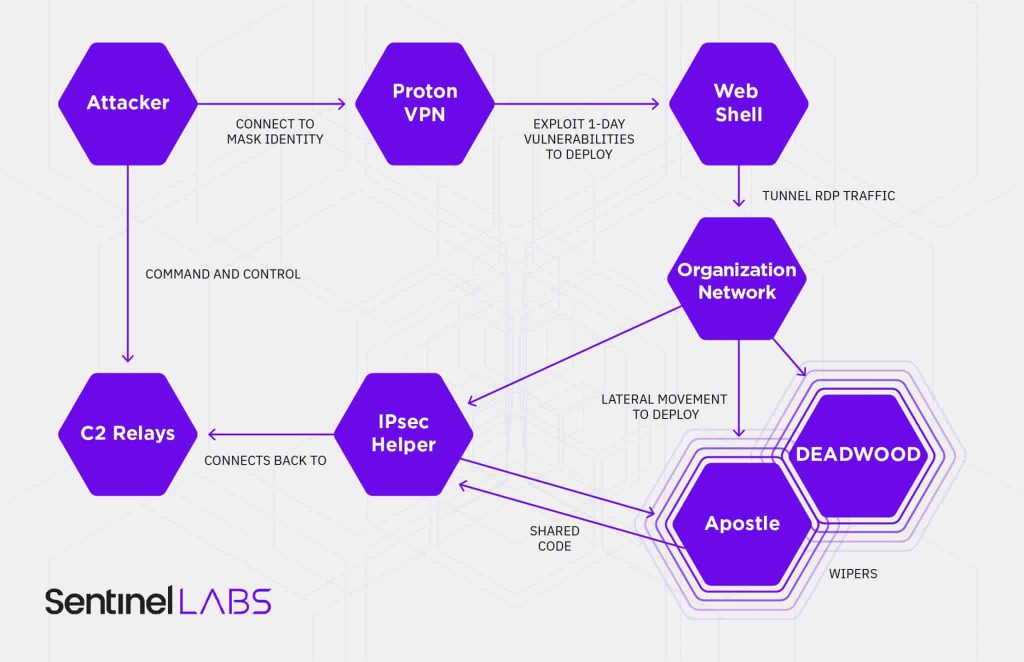
In the first stage, Agrius uses VPN software to access public-facing applications or services that belong to their target and then attempts an exploit, usually via compromised accounts or software flaws. For instance, it has used the FortiOS vulnerability (CVE-2018-13379) extensively to exploit attempts against its Israeli targets. Then they deploy webshells and use publicly available cybersecurity tools to steal credentials and network movement before deploying malware payload.
Agrius Toolkit
The group’s toolkit includes Deadwood, which is also called Detbosit. Research revealed that the Deadwood wiper was used by Agrius against a target in Saudi Arabia back in 2019. It is a destructive wiper malware strain also used by APT33 and APT34.
Both these groups are reportedly connected to wipers, including Shamoon, Deadwood, and ZeroCleare. Agrius also deploys a custom .NET backdoor known as IPsec Helper to maintain persistence and connect with the C&C server. Apostle and IPsec Helper are works of the same developer.