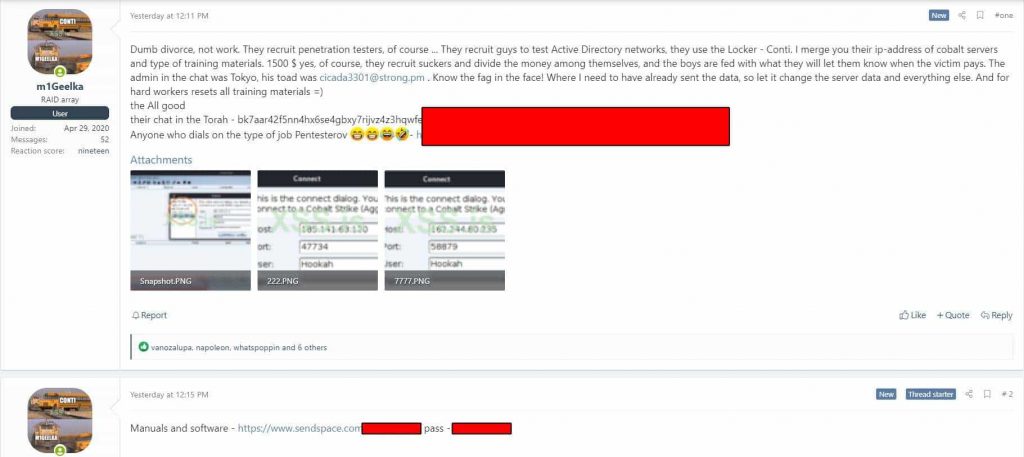
The member who goes by the username of “m1Geelka” expressed resentment on the notion that recruited hackers are not paid reasonably by the Conti ransomware gang.
Over the past decade, we have seen a range of ransomware attacks. But very rarely do we get a glimpse into their insider working on how these groups coordinate their attacks. In the latest, one such incident has occurred which allows us to observe so.
Apparently, an alleged former member of the infamous Conti ransomware gang, active since 2020, has released the group’s data on a Russian language hacking and cybercrime forum named XSS revealing sensitive information including tools used by the group, technical documentation, and the IP addresses for its servers.
The member who goes by the username of “m1Geelka” on the forum expressed resentment on the notion that recruited hackers are not paid reasonably with them only having received $1500 for being involved in a ransomware attack.
SEE: Conti ransomware gang demanded $40m from US school district
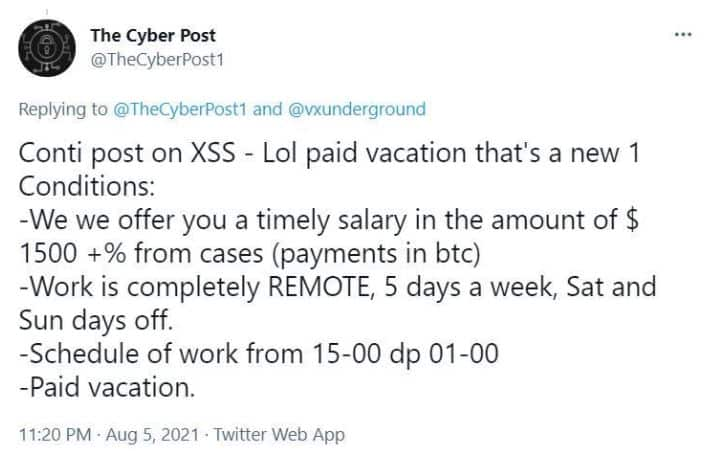
A Twitter user offers more insight on the working conditions offered to quote the defector from another post on the forum:
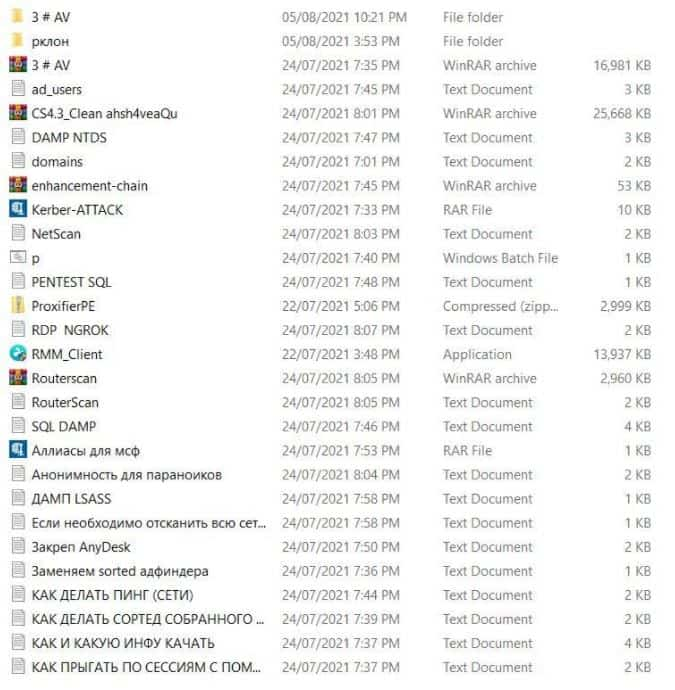
Alongside, an archived folder has also been shared which includes the training manuals mentioned above, certain tools, and several other documents in Russian:
These are believed to be used by groups that perform attacks using the ransomware benefitting from the training information given. This training information includes instructions on how to configure malicious programs, perform certain actions such as brute-forcing devices, and disabling Windows Defender among others.
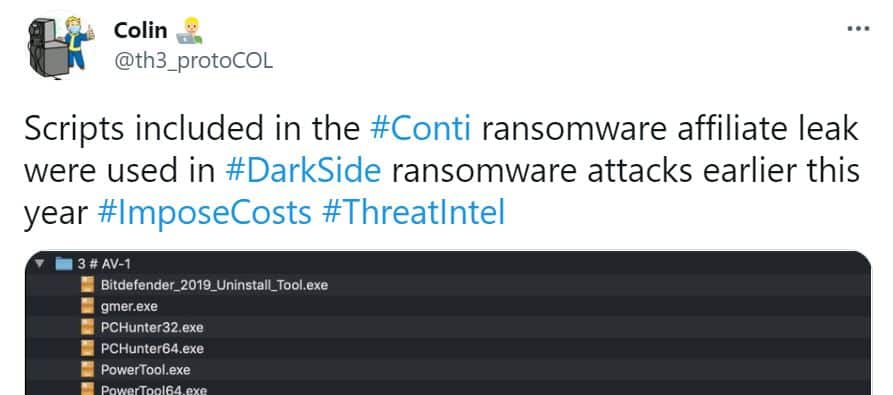
What’s noteworthy is that after analyzing these files, some researchers have found them being used in other ransomware attacks as well:
Moreover, the IP addresses where the group’s Cobalt Strike C2 servers are hosted have also been exposed which helps these groups to gain access to hacked networks. Users are advised to block them:
🤫 go block these 🤫
162.244.80.235
85.93.88.165
185.141.63.120
82.118.21.1— pancak3 (@pancak3lullz) August 5, 2021
Update:
This individual has also received backlash from other individuals in the forum. Criticizing him for sharing content.
Images courtesy of @TheCyberPharaoh && @3xp0rtblog pic.twitter.com/lk6LuO4uNF
— vx-underground (@vxunderground) August 6, 2021
To conclude, all of these files and details can help cybersecurity companies formulate better strategies on how to defend against ransomware attacks.
Furthermore, it will also internally make various black hat groups worried about their own data’s security and may prompt a change in how they hire outsiders.