Dark Web has become the hub of illegal activities over the Internet. Everything from credit card numbers to personal information and even classified data about military equipment is being sold for peanuts. Just yesterday, it was reported that a hacker stole classified information on U.S Airforce’s MQ-9 Reaper Drone and sold it on Dark Web.
Now, according to the latest research from McAfee’s Advanced Threat Research Team, remote desktop protocol (RDP) access is also on sale, which they have termed as a “huge business” opportunity for cybercriminals.
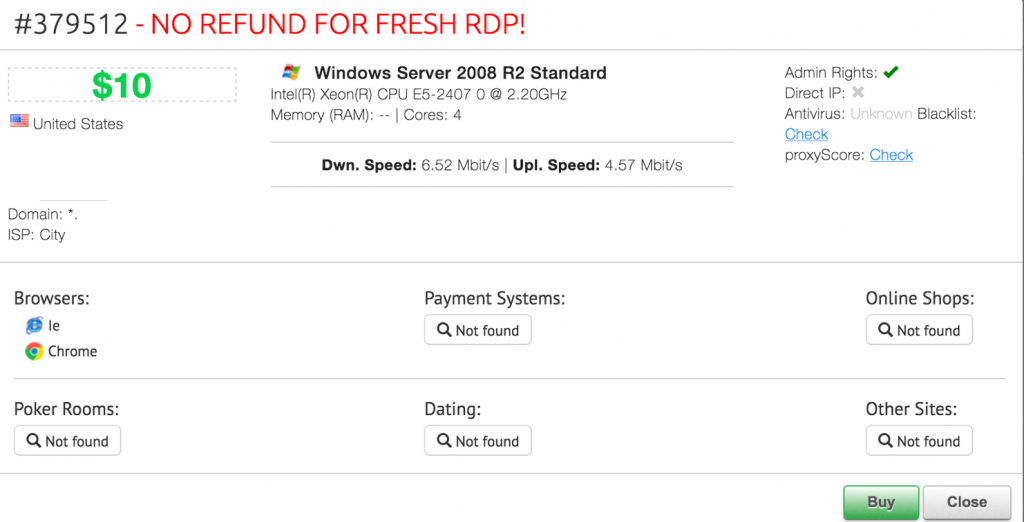
RDP access available for $10
Reportedly, cyber-criminals are offering stolen access to RDP, which is responsible for key security systems including transit and surveillance as well as building automation system of a high-profile international airport for only $10.
According to researchers, RDP access is available at a number of shops at the Dark Web while an open search analysis of a Russian RDP shop USA (Ultimate Anonymity Service) led McAfee researchers to this discovery.
The purpose of the search was to identify open RDP ports at certain organizations. Their search was narrowed down to three IPs from 65,536 and once a complete IP address was acquired, they managed to search for the WHOIS data to get all the addresses that belonged to a mainstream airport. The name of this airport is yet undisclosed.
Researchers write that the RDP access can lead cybercriminals to perform almost any activity such as creating false alerts to disrupt internal security team, steal login credentials and confidential data, send spam emails, conduct crypto-mining and launch ransomware attack on the organization.
RDP what?
Basically, RDP access serves as a route to target systems and attackers may even not need to use other attack tactics like exploit kit, phishing or malware, etc.
It is worth noting that Microsoft developed RDP as a proprietary protocol to facilitate access to various machines through a graphical interface and ideally it is used by system administrators. However, if attackers get access to key systems of an organization using RDP as an entry point, there can be dire consequences.
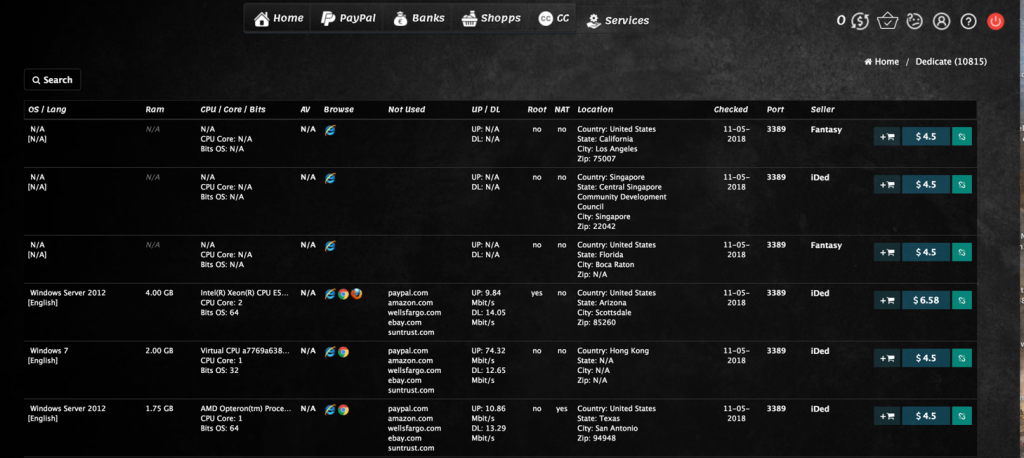
RDP shops have become the basis for large-scale cyber-attacks and the UAS is the largest of these shops. Currently, RDP shops are selling entry to systems accessible via the RDP port or port 3389. Systems are being marketed in their country, state, IP address, date of addition, ZIP code and bandwidth while their rate varies between $3 and $20. Rate fluctuates according to bandwidth.
Automated transit system of the airport at risk
Researchers identified user accounts including one sys-admin account, two accounts of companies that specialized in airport security and a domain linked with the automated transit system of the airport.
In the official blog post, McAfee’s head of cyber investigations John Fokker wrote that it is indeed concerning that such a system of vital public impact can be accessed through the internet. RDP access was also sold to various government systems including some that linked to the US, healthcare institutions, and medical equipment suppliers.
In order to secure their systems, organizations are urged to use complicated passwords and enable 2FA to ensure that brute-force RDP attacks are prevented or thwarted. Furthermore, RDP connections should not be allowed over open internet and IPs should get blocked after multiple failed login attempts.
“Just as we check the doors and windows when we leave our homes, organizations must regularly check which services are accessible from the outside and how they are secured. Protecting systems requires an integrated approach of defense in depth and proactive attitudes from every employee,” Fokker concluded.