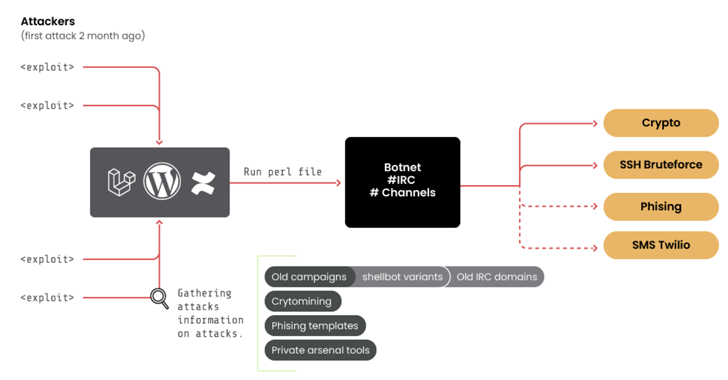
Kromtech’s security researchers have identified two point-of-sale (POS) malware strains namely AlinaPOS and JackPOS hosted on more than 4,000 ElasticSearch servers. It is the same platform that was targeted in the MongoDB ransomware campaign. In total there are over 15,000 servers on ElasticSearch that don’t possess any authentication and password protection while the POS malware strains are hidden in more than 4,000 servers.
It is surprising that the infections have been there since 2016 while the latest infection activity was noted in August 2017. Researchers also discovered that the two malware strains are now available for sale on the Dark Web hacking forums while cyber criminals have been using them since 2012.
The command and control servers of the two malware strains run on the infected hosts. Therefore, every infected server at ElasticSearch becomes part of a wider POS Botnet network providing command and control facility to POS malware clients, who then collect, encrypt and transfer sensitive financial data like credit card information. The data is stolen from infected Windows based computers, POS terminals and/or RAM. What’s even more surprising is the fact that almost 99% of these infected servers are hosted in AWS/Amazon Web Services, which is an otherwise trusted source.
According to the blog post from Bob Diachenko from Kromtech security, the reason of distribution of infection is that when taking up offers of free AWS T2 micro instance from AWS, which is part of the Elastic Compute Cloud, users skip the necessary security configuration to ensure quick installation. This offer is available for versions 1.5.2 or 2.3.2 of ElasticSearch only and this simple mistake have serious consequences such as sensitive data is exposed to cyber criminals. This hints at the fact that the malware acquires full administrative privileges on the infected machines.
“The absence of authentication on some ElasticSearch servers allowed attackers to take full administrative control on the exposed instance. This opened a range of possibilities for them – starting from the hidden use of resources and remote code execution to complete destruction of previously saved data,” noted Diachenko.
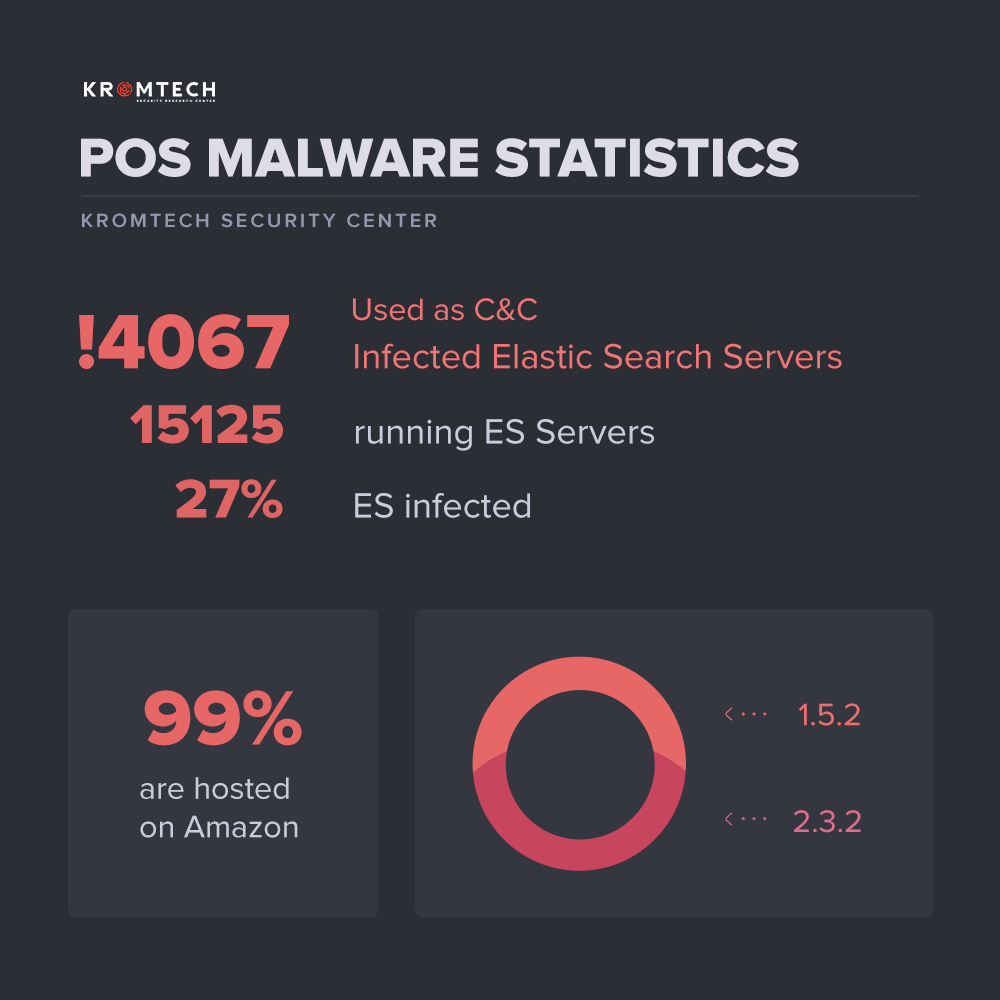
PoS malware stats via Kromtech
But why cyber criminals opted to host the malware strains on Amazon? The reason, according to Diachenko, is that on AWS we get a free T2 micro (EC2) instance of around 10 GB of disk space. Diachenko explains why hackers opted for ElasticSearch servers:
“The main reason for malicious actors to use ES servers is that (if open) their configuration allows not only read but write/install external files without additional confirmation. ES interface (Kibana) does not see these files. It’s highly effective because even if one or several infected servers shut down, the rest will work as usual and stolen cc data will be processed in other ways.”
Kromtech has notified Amazon as well as the affected organizations regarding the hidden POS malware strains. A majority of the affected systems are located in the US. When the malware takes over control of a machine, cybercriminals can remotely access the server’s resources. This allows criminals to steal, delete or save the data stored on the server.
It is, therefore, important that Sysadmins check their ElasticSearch requests and duly patch or reinstall and block the external ports. “Reinstall all compromised systems. Otherwise, you need to clean up all suspicious processes, check your systems with antivirus and also monitor you system during next three months for any anomaly connection,” says Diachenko.
[fullsquaread][/fullsquaread]