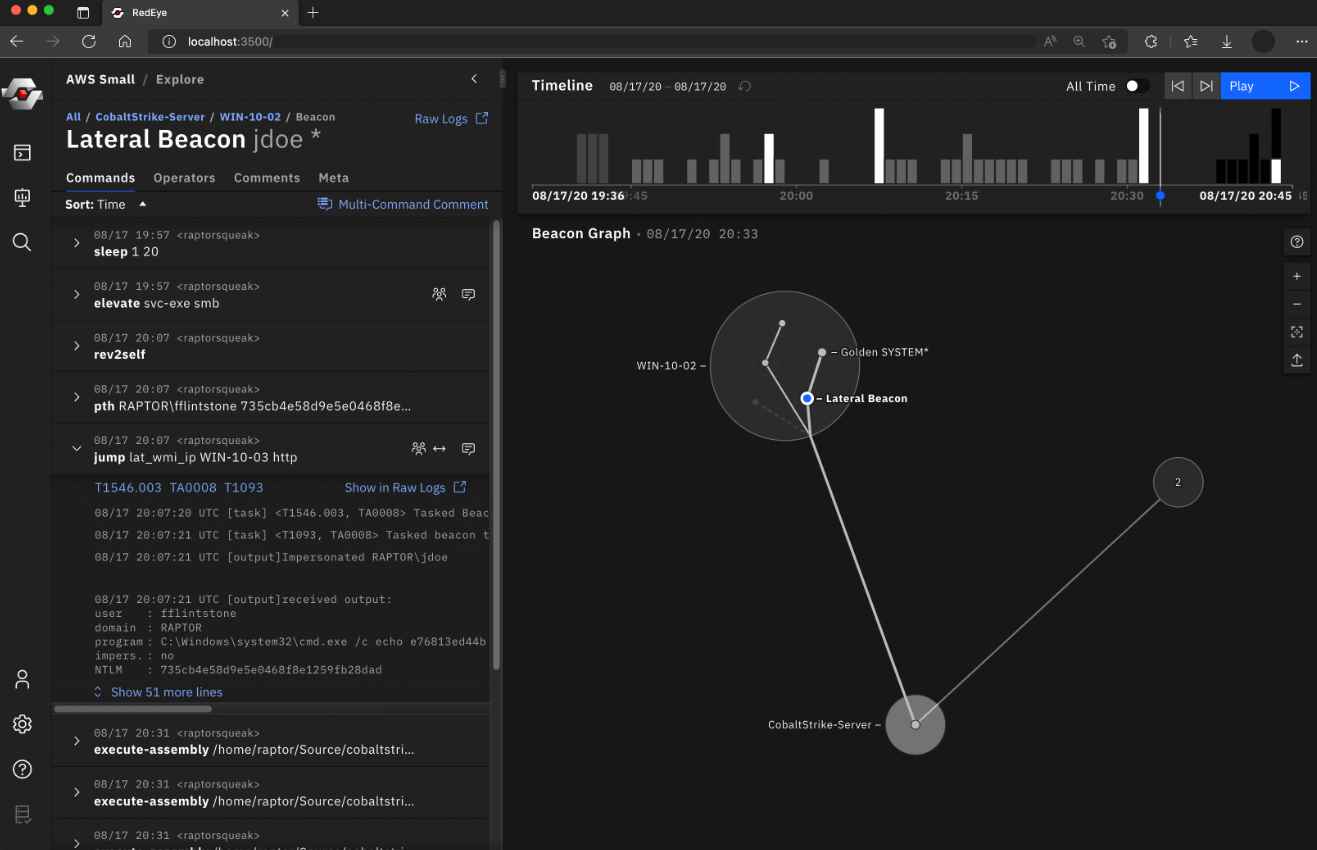
MITRE ATT&CK reveals the intentions of the attackers to the defenders, which results in a significant reduction in the number of criminals hiding behind rocks and structures. MITRE offers a consistent pattern that may be altered as required to match the “score” of an organization’s threat intelligence requirements. This is similar to the concept of ostinatos, which are repetitive patterns. MITRE ATT&CK is a knowledge base on adversary strategies and methods that is available all around the globe and is based on observations from the actual world. The ATT&CK knowledge base serves as a platform around which specialized threat models and approaches may be built by the commercial sector, the government, and the community of cybersecurity product and service providers.
A framework known as MITRE ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, is comprised of adversarial tactics, techniques, and procedures (TTPs) that are used by threat actors. It is a paradigm that is built on matrices that gives a methodical manner to study, analyze, and explain the numerous strategies, methods, and processes that attackers may utilize at various phases of an attack.
A more straightforward explanation may be found on another page inside the MITRE website, which states that “MITRE ATT&CK is a knowledge base that helps simulate cyber attackers’ strategies and techniques—and then illustrates how to identify or stop them.”
The MITRE ATT&CK framework, often known as MAF, is valuable for a number of applications, including the following:
Assessing the cybersecurity posture of an organization: Mapping the TTPs used by attackers to the defenses that are currently in place within an organization is one way that MAF can assist in identifying potential vulnerabilities and areas for improvement within an organization’s cybersecurity posture.
Development and testing of cybersecurity controls: Based on the strategies and methods often used by attackers, the framework may be used to identify and rank the most crucial measures to put in place.
The ATT&CK framework may assist security teams in better detecting and reacting to cyberattacks by assisting them in better understanding the tactics, methods, and procedures that are being employed by attackers. This understanding will allow security teams to better identify and respond to attacks.
MAF offers a common vocabulary and understanding of cyber dangers, which may be used to promote communication and cooperation among information security experts. This can be accomplished via the sharing of knowledge and best practices.
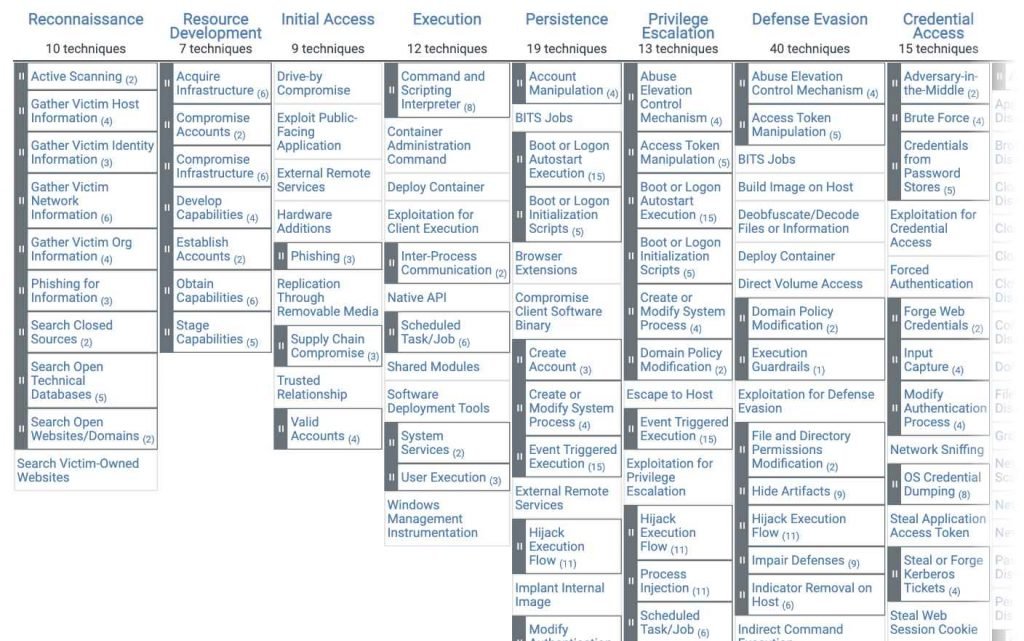
There are 14 tactics, and beneath each strategy are well-known methods. Many of the techniques have sub-techniques, and some of the techniques have sub-sub-techniques.
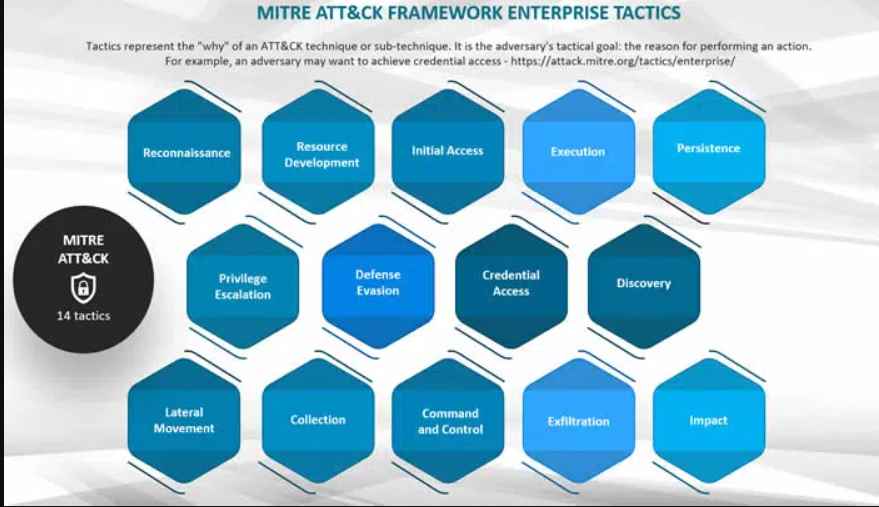
The following is a list of all 14 strategies, which are presented as headers in the matrix:
The process of gathering intelligence about an intended target in order to plan for future hostile activities is known as reconnaissance.
The process of creating an infrastructure for command and control as well as resources to support operations is known as resource development.
Initial access refers to the strategies that adversaries use in order to get into a network by exploiting vulnerabilities in systems that are exposed to the public. One illustration of this would be spear-phishing.
Execution: These strategies lead to the adversary executing code on the system that is the target of their attack. One example of this would be a hostile hacker who executed a PowerShell script in order to either obtain further attack tools or scan other computer networks.
Persistence is the ability for an adversary to keep access to a target system even after it has been restarted and new credentials have been entered. An attacker may, for instance, set up a scheduled job to execute malicious code at a certain point in time.
Privilege escalation refers to the process through which adversaries get increasing levels of privileges (e.g., root, local admin).
Defense evasion involves concealing dangerous code inside already running programs or directories, encrypting hostile code, or turning off security software. These are all examples of evasion strategies.
Credential access: These strategies include the theft of usernames and other credentials for later use.
Discovery is the process of gathering knowledge about computer systems and networks that an adversary intends to exploit or utilize to their advantage in a tactical conflict.
Lateral movement: Attackers have the ability to travel laterally from one system to another during an attack. Pass-the-hash and inappropriate usage of RDP are two examples.
Collection: In order to carry out their aims, adversaries amass the information they targeted in the first place.
Command and control: Attackers connect with a system that is under their control. This is known as command and control. For instance, in order to avoid detection, an attacker may interact with a system by using a port that is not often used.
Exfiltration occurs when data is moved from a network that has been infiltrated to a system that is under the control of the attacker.
Impact: Attackers use these strategies in order to adversely influence the availability of systems, networks, and data in their target environments. These methods include denying service, erasing data and disks, and denying access.
In order to assist enterprises in evaluating and bettering their cybersecurity defenses, the MAF is used extensively across a broad number of industries and sectors. The following are a few examples of how the framework might be utilized:
Financial services: Financial institutions use the framework to identify and prioritize the most important controls to implement based on the strategies and methods that are commonly used by attackers targeting the financial sector. This is done by basing the framework on the tactics and techniques that attackers use.
Healthcare: Organizations in the healthcare business utilize the framework to better understand the strategies and methods that attackers use when aiming their attacks at the healthcare industry, as well as to create and test controls to better protect against these threats.
Critical infrastructure: Organizations in the critical infrastructure sector, such as utilities and transportation systems, use the framework to understand and defend against the strategies and methods used by attackers targeting these types of systems. Specifically, the framework focuses on understanding and defending against the techniques and strategies used by attackers in the energy sector.
Government: Government agencies utilize the framework to analyze and enhance their cybersecurity defenses, as well as to understand the tactics and strategies employed by attackers targeting the government sector. Using this information, government agencies may better defend themselves against cyberattacks.
Retail: Retail organizations use the framework to understand and defend against the tactics and techniques used by attackers targeting the retail industry, including tactics such as point-of-sale attacks and data breaches. Healthcare: Healthcare organizations use the framework to understand and defend against the tactics and techniques used by attackers targeting the healthcare industry.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.