Cybercriminals have identified a unique method of attacking Mac devices, which involves exploiting executable or .EXE files. Those files that can be executed both on Mac and Windows devices have the potential of infecting Mac computers as these unload a .exe malware.
Discovered by Trend Micro researchers, the new malware can bypass the macOS security system and easily infect Mac devices just by deploying exe files. In the attack, malicious macOS application .dmg acts as an installer for famous software on a torrent site. This app contains an exe application having Mono framework to ensure that it becomes compatible with macOS.
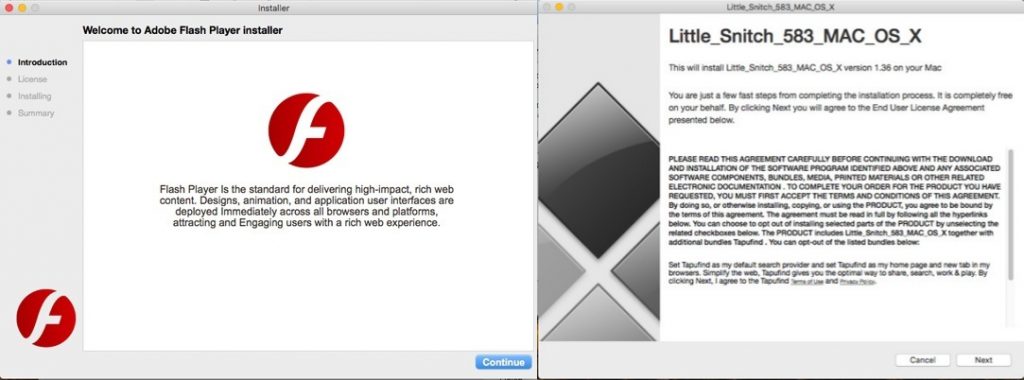
The fake installer makes the user believe that it will install the Little Snitch firewall app but since it contains a mono-compiled hidden payload, therefore, it is able to collect system information and transmit it to a C&C server that is being controlled by the attacker.
After the installation process is complete, the exe malware further downloads adware apps disguised as authentic Adobe Flash media Player or Little Snitch and requests the user to install them on the device.
For your information, Mono is Microsoft’s .NET framework’s open source implementation. The .NET Framework lets developers create a variety of cross-platform .NET apps that support multiple platforms including Windows, Linux, and Mac OS X.
However, researchers could not identify a specific pattern of attack in this particular campaign but telemetry data showed that most of the targeted devices are located in the UK, Australia, USA, Armenia, South Africa, and Luxembourg. It is worth noting that the malware only attacks Mac devices.
“We suspect that this specific malware can be used as an evasion technique for other attack or infection attempts to bypass some built-in safeguards such as digital certification checks since it is an unsupported binary executable in Mac systems by design,” wrote Trend Micro researchers Don Ladores and Luis Magisa in their blog post.
It is often noted that when a Windows executable file is run on Mac systems it displays error and the built-in security systems like Gatekeeper also do not check .exe files for infections. This is how the malicious files are able to bypass the code signature check as well as verification process because Gatekeeper only checks “native Mac files.” said researchers.
The only way to stay safe and protected from such malware is to avoid downloading apps from third-party platforms and only to install legitimate apps.