Reportedly, Carter’s failure to implement proper authentication protocols on the store’s parcel tracking pages exposed data and shoppers to scams.
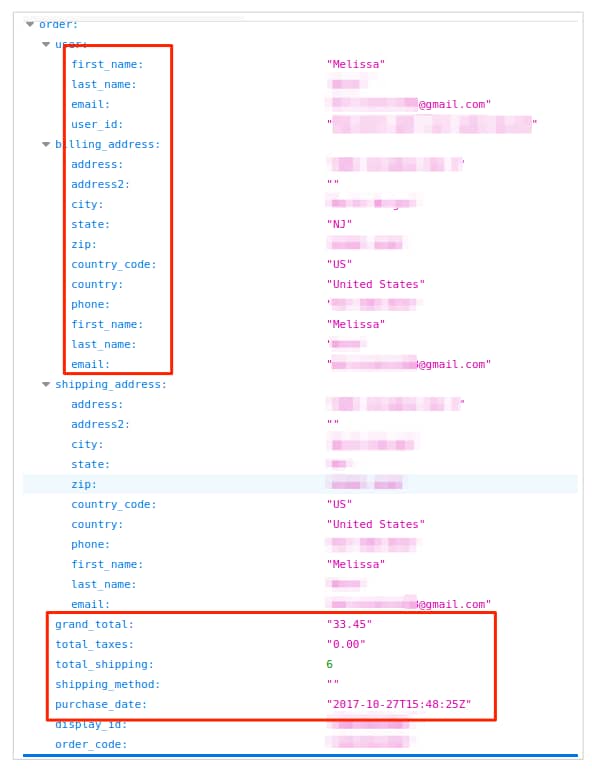
VpnMentor analysts report that the US-based baby clothing retailer Carter’s exposed personally identifiable information (PII) of hundreds of thousands of its customers because of inadequate security of Linc, the automatic online purchases software the company uses.
The Linc system delivered shortened URLs with Carter’s purchases and shipping data without any appropriate security protections. By modifying the Linc generated URLs, it became possible to access backend JSON data revealing even more customer details, which the confirmation pages didn’t expose, like full names, phone numbers, and delivery addresses of Carter’s customers.
In total, the exposed data included the following:
- Full name
- Email addresses
- Billing addresses
- City
- State
- Zip
- Country code
- Country
- Phone number
- Purchasing details
- Shipping tracking IDs and links
Over 410,000 Records Exposed
It is reported that more than 410,000 records have been exposed in Carter’s data leak, including hundreds of thousands of customer records dating back to 2015.
VpnMentor noted that the shortened URLs are not only easy to discover by hackers since there is a “lack of sufficient entropy or compensating security protocols.”
Carter’s didn’t put authentication in place to verify that the person making the purchase has visited the confirmation page. Researchers also noted that the links don’t expire. This means customers purchased from Carter’s online store even years ago will also be at risk.
Customers exposed to phishing scam, fraud
VpnMentor researchers have warned that this kind of data leak involving PII exposed Caster’s customers to all kinds of scams such as malicious cybercriminals can use the data to launch phishing campaigns, sending out fake emails that appear to be from Carter’s, and force the victims to provide even more sensitive data such as credit card information.
For recent orders, threat actors can call a customer and discuss purchases they have made, posing as courier personnel or customer support. They can build rapport with their target and target them in their criminal schemes.
“For any purchases still on their way to a customer, hackers could redirect deliveries and steal them, reselling any Carter’s stolen products online,” vpnMentor researchers warned in their report.
Carter’s was contacted by vpnMentor’s team on March 17. The company asked them to submit a detailed report of their analysis through other channels. The shortened URLs were later deactivated, somewhere between April 4 and April 7, 2021.