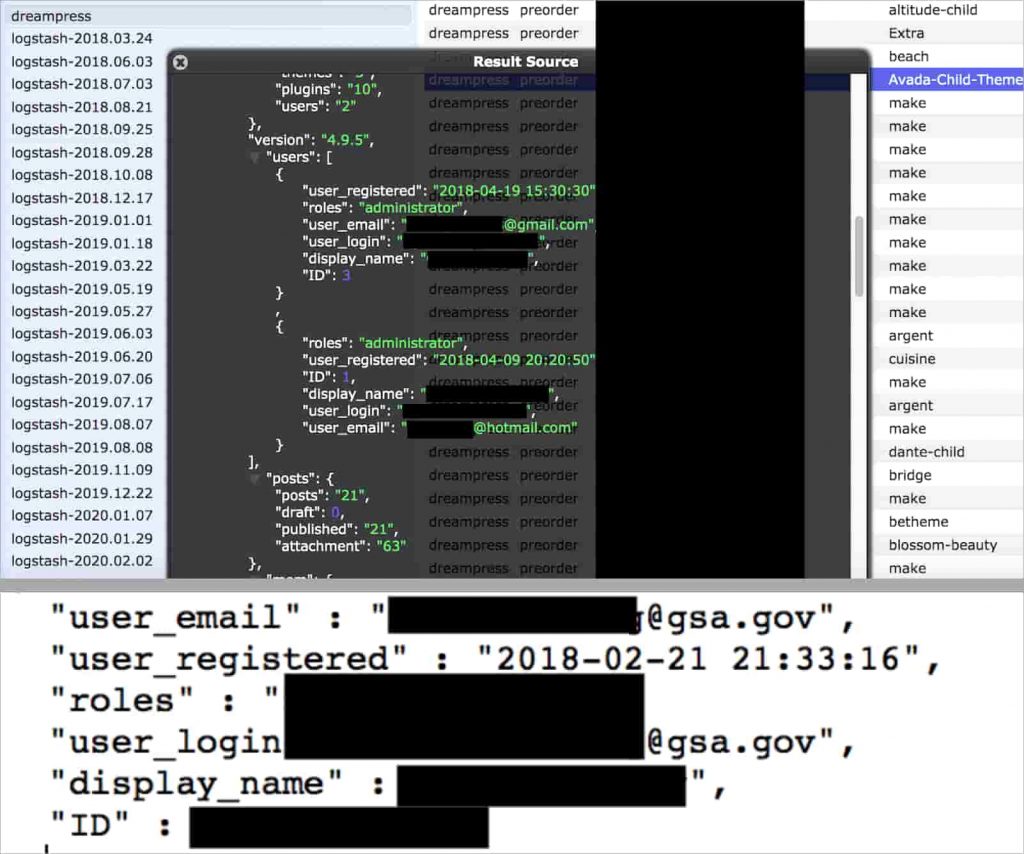
The total size of the exposed data was 86.15 GB with 814,709,344 total records from the past 3 years.
In recent news, the IT security researchers at Website Planet found an unsecured database owned by Los Angeles-based web hosting provider and domain name registrar DreamHost.
The database belonged to DreamHost’s DreamPress managed WordPress hosting that was left exposed without any password or security authentication meaning anyone from the public could have access to it.
Amongst the data it contained, the monitoring and file logs exposed internal records which should not have been publicly accessible. The total size of the data breach was 86.15 GB with 814,709,344 total records.
The exposed log files contained all the records from the past 3 years which contained information about WordPress accounts hosted or installed on DreamHost’s server and their users.
Additionally, admin and user information for DreamPress accounts for WordPress including WordPress login location URL, first and last names, email addresses, usernames, roles (admin, editor, registered user, etc.) was also part of the exposed records.
Moreover, host IP addresses and timestamps were also exposed as well as build and version information that could allow for a secondary path for malware.
Plugin and theme details including configuration or security information that could potentially allow cybercriminals to exploit or gain access deeper into the network were also open to public access.
According to Website Planet’s blog post, after this discovery was made, the research team sent a responsible disclosure to DreamHost and the database was secured within hours. If not for the fast recovery of the database, there could have been serious security threats.
Moreover, email addresses of internal and external users could be targeted in phishing attacks or other social engineering scams. The database was at risk of a ransomware attack due to the configuration settings that allowed public access.
Most cybercrimes are for financial gain and it is estimated that these crimes will cost as much as $10.5 trillion annually by 2025 and that 98% of cyber attacks arise from some form of social engineering.
This leak, if found by unethical actors, could have provided enough information for cybercriminals to target customers with a social engineering attack or try to gain access to the accounts.