There is currently a wide range of instant messaging services and, according to information security specialists, many have a security measure known as end-to-end encryption, which prevents third parties from being able to access the content of messages between two users.
However, this does not mean that our information is completely secure, as hackers can still find a way to breach the security of these apps. Using side channel attack techniques, a threat actor could compromise services like WhatsApp and Telegram for malicious purposes.
Information security specialists consider that
the main problem is that users of these apps do not have cybersecurity
knowledge, so hackers can access some resources, such as login tokens, that are
not protected by end-to-end encryption. An example of this is the Telegrab
attack, a malware that allows hackers to take control of a Telegram desktop
session by copying tokens to access the platform. A report published by Talos
reveals some variants of these attacks.
Taking control of a
Telegram desktop session
Session hijacking highly likely when using the Telegram web version. Using the appropriate malware (such as the aforementioned Telegrab), a hacker can extract an access token to login to the victim’s account. When the attacker logs in using the stolen token, the new session starts without the user being able to notice.
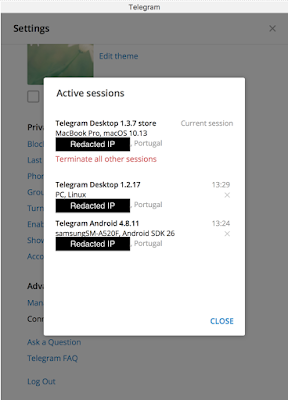
In the end, the messages received by the victim
are replicated to the session under the attacker’s control.
Shadow sessions in
Telegram app
Although it is much more complicated to breach
security in the mobile version of Telegram, this does not mean that it is
impossible. Some malicious apps can create a “shadow session” without
victim interaction, only requiring some minimal permission such as accessing
SMS or killing background processes.

When registering with Telegram, the application
asks the user for a phone number, which will be verified via an SMS with a
unique code. If a user tries to register the same phone number again, Telegram
will send a code via the Telegram channel and not as an SMS.
This change prevents malicious apps from
creating shadow sessions without user interaction, as it ban them from
accessing Telegram’s security code. However, if the time to complete the
registration is exhausted, Telegram assumes that the user does not have access
to the app yet, so it sends a new code via SMS. This creates a race condition
that can be exploited by malicious apps to create a shadow session without user
interaction.
Hijacking a WhatsApp
Web session
Unlike Telegram, WhatsApp does notify users in
case there is a second active session in the web version of the app. According
to information security experts, if an attacker initiated a WhatsApp Web
session, the target user will receive a notification informing about the new
active session.

In this scenario, the attacker will have access
to all the information in the attacked WhatsApp account until the victim
chooses an option to close the second active session from their computer.
However, a flaw in this protection method allows hackers to bypass security by
performing the following steps:
- The
hacker must stop the application on the victim’s computer - The
hacker starts WhatsApp with the stolen information - The
hacker will then disable the network interface on the machine running the
hijacked session - Attacker
logs in again in WhatsApp Web on the victim’s machine - Finally,
the hacker will enable the network interface on the machine running the
hijacked session
Thanks to this method, hackers can access the
contents of the victim’s WhatsApp account, staying online unless the victim
logs out manually on their mobile device.
While these services stand out for being secured,
information security specialists from the International Institute of Cyber
Security (IICS) believe that it is necessary to involve users more in the
implementation of additional security measures for any other attack variant.








