GriftHorse malware uses malicious apps to subscribe victims to premium services that cost them $42 (£30 –€36) per month.
The IT security researchers at Zimperium Labs have reported an Android malware campaign affecting devices around the world to carry out financial scams and steal user data.
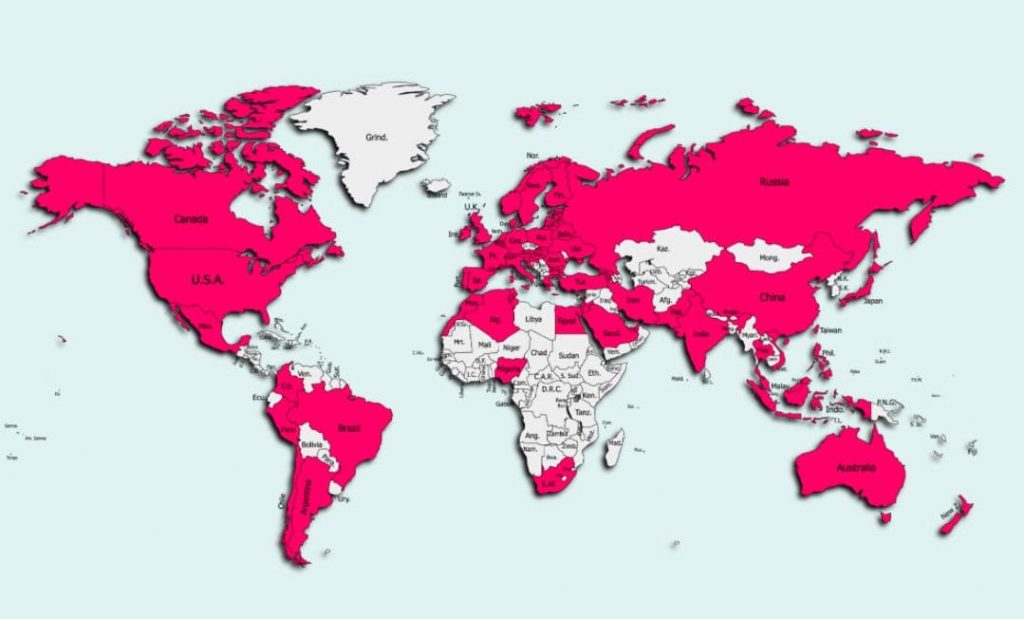
According to researchers, nearly 10 million devices across 70 countries were affected by their newly discovered ‘aggressive’ campaign.
The researchers noted that cyber criminals used malicious Android applications to trap their victims. These apps request the victim to subscribe to premium services that cost €36 (£30 – $42) per month.
The campaign was detected after Zimperium’s z9 on-device malware detection engine alerted about it.
Zimperium researchers Nipun Gupta and Aazim Yaswant stated that this is a typical global premium service scam where hackers lure victims through phishing techniques so that they download malicious Android apps, which act as trojans.
About GriftHorse Malicious Trojan
The company reported that threat actors behind this campaign are using a new trojan called GriftHorse. This scheme has been under active development since November 2020 and has claimed victims across the globe including in:
- India
- China
- Brazil
- Spain
- Russia
- Canada
- Australia
- United States
- The United Kingdom.
In this particular campaign, around 200 authentic-looking applications were used, making it the most widespread of all scams discovered in 2021.
About the Malicious Apps
In their blog post, researchers noted that scammers had created malicious applications for a varied set of categories, including lifestyle, tools, entertainment, dating, and personalization.
Hence, the attack scale is wider than it is in similar other campaigns involving infected applications.
The apps boast a high number of downloads. For instance, one of the malicious apps, Handy Translator Pro, has around 500,000 downloads.
Attack Mechanism
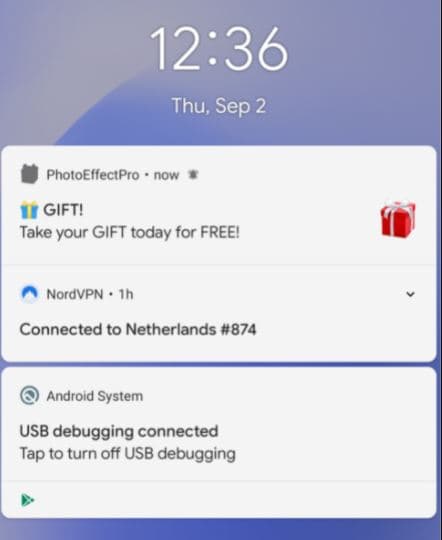
The applications are not only distributed via third-party app stores but also through Google Play. After successfully infecting the device, the apps bombard the phone with deceptive alerts, offering a free gift to the user after clicking on it.
These then redirect the users to a geo-specific webpage to submit their phone numbers to verify, but in reality, they submit their numbers to a premium SMS service that will charge their phone bill for more than €30 per month.
After the campaign was disclosed by Zimperium, following responsible disclosure, Google removed the apps from the Play Store. However, researchers reported that the malicious apps are still available on unsecured third-party repositories.
“Overall, GriftHorse Android Trojan takes advantage of small screens, local trust, and misinformation to trick users into downloading and installing these Android Trojans, as well frustration or curiosity when accepting the fake free prize spammed into their notification screens,” Yaswant and Gupta noted.