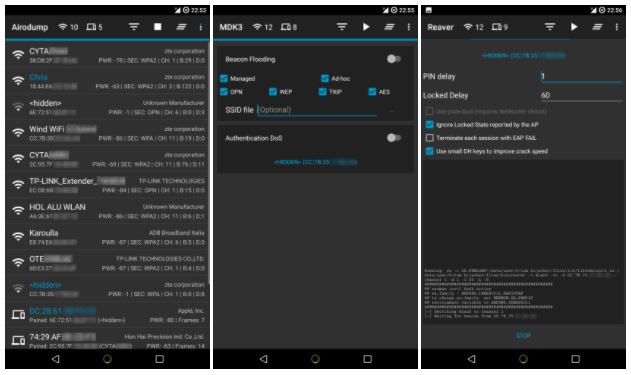
To begin with, the experts explain that Hijacker is a graphical user interface for the penetration test tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. This application offers a simple and easy user interface to use the tools without writing commands in a console and copying and pasting MAC addresses.
The information security professionals comment that this application requires an Android ARM device with an internal wireless adapter that supports the monitor mode. Some Android devices can do it, but none of them natively. This means that you will need a custom firmware. A device using the BCM4339 chip set (MSM8974, such as Nexus 5, Xperia Z1 / Z2, LG G2, LG G Flex, Samsung Galaxy Note 3) will work with Nexmon. Also devices that use BCM4330 can use bcmon.
An alternative that the experts give is to use an external adapter that supports the monitor mode in Android with an OTG cable.
The necessary tools are included for the armv7l and aarch64 devices as of version 1.1. The Nexmon driver and the administration utility for BCM4339 and BCM4358 are included.
Information security researchers say that root access is also necessary, since these tools need a root to function.
Characteristics
Information gathering
- See a list of access points and stations (customers) around you, including hidden ones
- View the activity of a specific network measuring beacons and data packets, and their clients
- Statistics on access points and stations
- Consult the manufacturer of a device from the OUI database
- See the signal strength of the devices and filter the ones that are closest to you
- Save the captured packets in the .cap file
Attacks
- Disabling all clients of a network, either for each of them or without a specific objective
- Disabling a specific client from the network to which you are connected
- MDK3 Beacon Flooding with custom options and SSID list
- MDK3 Authentication DoS for a specific network or for each nearby AP
- Capture a WPA handshake or join IV to break a WEP network
- Reaver WPS cracking
Other
- Leave the application running in the background, optionally with a notification
- Copy commands or MAC addresses to the clipboard
- Includes the necessary tools, without the need for manual installation
- Includes the Nexmon driver, required library and administration utility for devices BCM4339 and BCM4358
- Set commands to enable and disable the monitor mode automatically
- Crack .cap files with a custom word list
- Create custom actions and easily execute them at an access point or client
- Sort and filter access points and stations with many parameters
- Export all collected information to a file
- Add a persistent alias to a device for easier identification

For the installation, experts comment that you must ensure that:
- you are on Android 5+
- is rooted, SuperSU is required, if it is in CM / LineageOS install SuperSU
- you have a firmware to support monitor mode on your wireless interface
Whenever you run Hijacker for the first time, you will be asked if you want to install the Nexmon firmware or go to the start screen. If you have installed your firmware or use an external adapter, you can go to the home screen. Otherwise, and if your device is compatible, click on ‘Install Nexmon’ and then ‘Install’. Then, you will land on the home screen and airodump will start. Information security professionals say you should make sure you have enabled your WiFi and it is in monitor mode.
It is also important to know that on some devices, changing the files in / system could trigger an Android security feature and the partition of your system will be restored when you reboot the system.
For the problems solution. This application is designed and tested for ARM devices. All the included binaries are compiled for that architecture and will not work on anything else. You can check if your device is compatible in Settings: if you have the option to install Nexmon, then you are in the correct architecture, otherwise you will have to install all the tools manually (busybox, aircrack-ng suite, mdk3, reaver, wireless tools, library libfakeioctl.so) in an accessible PATH directory and set the option ‘Prefix’ for the tools to preload the library they need: LD_PRELOAD = / path / to / libfakeioctl.so.
In configuration, you will find an option to test the tools. If something fails, you can click on ‘Copy test command’ and select the tool that fails. This will copy a test command to your clipboard, which you can manually run in a root shell and see what is wrong. In the case where all the tests pass and you still have a problem, do not hesitate to open a problem here to solve it, or use the option “Send comments” in the configuration of the application.
If the application should fail, a new activity will be started that will generate an error report in your external storage and give you the option to send it by email. The report is displayed in the activity so you can see exactly what will be sent, say information security researchers.
Keep in mind that Hijacker is just a GUI for these tools. The way you run the tools is pretty simple, and if all the tests happen and you’re in monitor mode, you should get the results you want. Information security professionals tell us to also keep in mind that these are audit tools. This means that they are used to test the integrity of your network, so there is a possibility that attacks will not work on your network. This is not the fault of the application; it is really something to be happy about.