Researchers published research detailing a method for taking control of smart speakers, which would allow threat actors to make phone calls, access e-commerce websites, and control appliances, doors, and lockers linked to these devices.
According to the report, the attack works by using the speaker to issue voice commands, as long as the command issued contains the device’s wake word. The research was published by Royal Hollowat University in London and the University Of Catania, Italy.
The researchers mention that a threat actor could also exploit a full voice vulnerability (FVV), allowing Amazon Echo devices to execute self-emitting commands without temporarily reducing the volume of the exploited device.
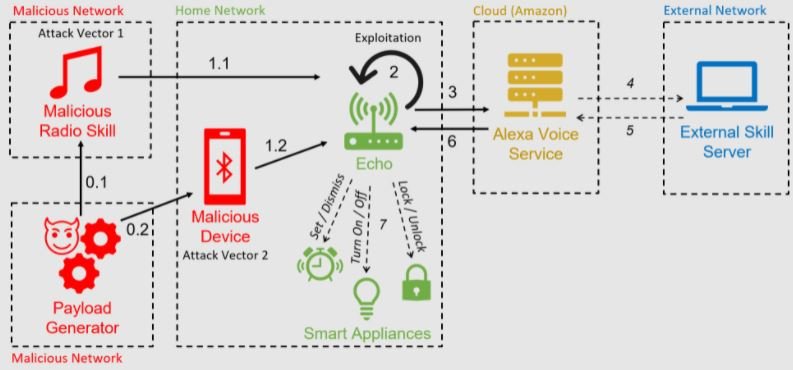
This attack relies on Alexa’s functionality to force devices to perform self-emitting commands, in what researchers have described as an “Alexa vs. Alexa” scenario. It takes a few seconds of proximity to an exposed device for a threat actor to pronounce the voice command to pair it with the attacker’s device.
Other variants of the attack are based on the use of a malicious radio station, responsible for generating the self-emitting commands. That attack is no longer possible due to the way Amazon mitigated the reported flaws, though some third- and fourth-generation Echo Dot devices could still be vulnerable.
The Alexa vs. Alexa scenario begins when a vulnerable Echo device connects via Bluetooth to the attacker’s device. From that point on, the attacker can use a text-to-speech application or other means to transmit voice commands; the researchers published a video as a proof of concept (PoC):
It is possible to exploit the Alexa vs. Alexa scenario to execute commands that could put at risk an entire home environment where an Echo or Alexa device is used, exposing users to malicious activities such as:
- Hijacking of other home Internet of Things (IoT) devices
- Make calls to any phone number for malicious purposes
- Make unauthorized purchases using the affected user’s Amazon account. Users could still be alerted to malicious activity
- Manipulation of a user’s previously linked calendar to add, move, delete, or modify scheduled events
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















