Researchers believe the trojanized version of TeamViewer is being spread by a Russian speaking hacker.
The latest report from Check Point reveals that multiple embassies in Europe were targeted with a trojanized version of TeamViewer. The embassies affected in the latest wave of attacks include Nepal, Lebanon, Italy, Kenya, Liberia, Guyana, and Bermuda.
According to Check Point’s investigation, a hacker using the alias EvaPiks is responsible for singlehandedly carrying out targeted malware attacks on embassies. It must be noted that TeamViewer is a remote desktop sharing and remote access tool that’s widely used around the world. The motive behind the attacks is yet unclear but researchers believe that financial theft could possibly be the primary objective.
Research further revealed that the alleged hacker has links with Russian-speaking groups because of using Cyrillic artifacts. The attacks, reportedly, started on 1st April and since then multiple embassies have been targeted. Check Point’s threat intelligence group manager Lotem Finkelsteen stated that:
“The targets were victimized that day, and then the threat actors moved step by step through a multistaged infection chain to further stages until they gained full remote access to the infected devices.”
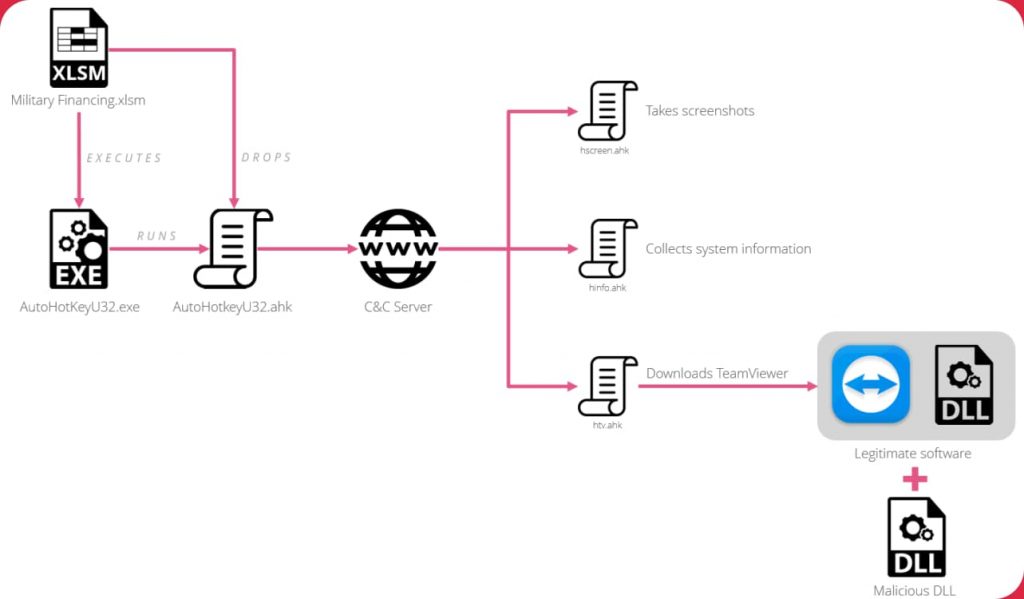
In this campaign, malware is hidden in TeamViewer in the form of a classified US government XLSM document containing malicious macros and sent via email titled “Military Financing Program.” The file has been carefully crafted and bears the authentic logo of the US Department of State while the file itself is marked “top secret.”
Users must disable macros!
As soon as the macros are enabled, two files are extracted from the XLSM document’s encoded cells. One of the files is an authentic AutoHotkey program, while the other is an infected version of the file that creates a connection with the C&C server to download and execute the malware-bearing version of TeamViewer. When this file is executed, the attacker can establish remote access on the infected device.
Furthermore, the infected version of TeamViewer can download and execute additional commands such as the command to hide the TeamViewer interface to deceive the user or to transfer session credentials to a text document.
Threat Point researchers suggest in their blog post that considering the victims that have been targeted and the multi-stage nature of the campaign, it is quite possible that either nation-sponsored hackers or some very sophisticated cybercriminals are involved.
“…We wonder whether he joined others to carry [these] attacks, or he just tunneled others’ attack through his successful infection chain,” said Finkelsteen.
In every attack, the targets were selected quite carefully, and each individual was connected to the government’s revenue-related responsibilities or the financial sector. However, so far there is no evidence of the attacker trying to access the targeted governments’ bank accounts.
Therefore, the other motive behind the attack could be cyber espionage. Currently, researchers aren’t ruling out geopolitical motives as the main reason behind the attacks too. Nevertheless, users must disable macros, use a reliable anti-virus program and keep their system updated.