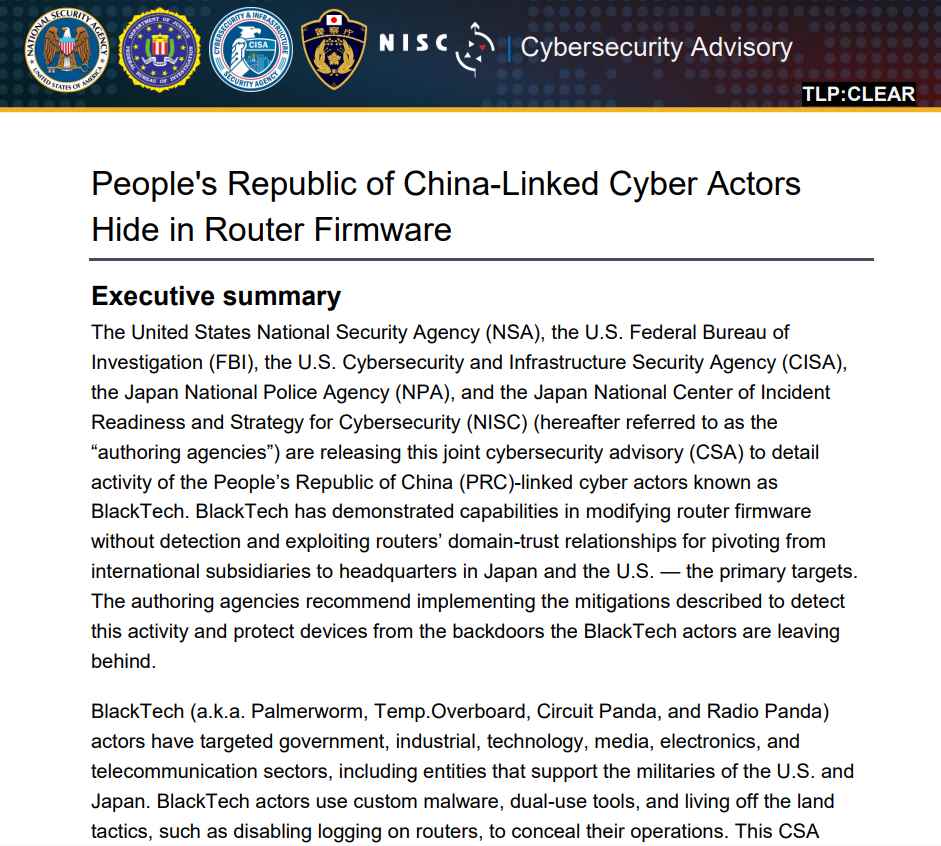
A notorious threat actor with presumed ties to the Chinese government, known as “BlackTech”, has reportedly been exploiting Cisco routers to infiltrate major corporations in the United States and Japan, according to cybersecurity experts. Using various aliases like Palmerworm, Temp.Overboard, Circuit Panda, and Radio Panda, BlackTech has stealthily replaced original device firmware with malicious counterparts.
By infiltrating these Cisco routers, BlackTech successfully gains consistent access and leverage within organizations, allowing them to navigate from smaller international subsidiaries to the main headquarters. Targets of these quiet cyber-attacks have been varied, including governmental bodies, industrial complexes, and companies within the technology, media, electronics, and telecommunications fields, among others. Notably, some of the affected entities are known to provide support to the U.S. and Japanese military forces.
A collective cybersecurity advisory released by the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), along with Japanese national police and cybersecurity agencies, alerted the public to these activities. However, the advisory didn’t specify particular vulnerabilities in Cisco routers but noted that the observed tactics, techniques, and procedures (TTPs) are not exclusive to Cisco products, suggesting that similar strategies could compromise other network equipment as well.
Tom Pace, a former Department of Energy cyber head who now leads NetRise, indicated that these incidents highlight broader challenges in securing edge devices. He argued that regardless of the manufacturer—be it Cisco, Juniper, Huawei, or Arista—the same security issues seem to persist across the board.
Since its inception around 2010, BlackTech has been actively involved in compromising Cisco routers and stealing intellectual property. The group is known for its deployment of twelve distinct custom malware families, designed to penetrate Windows, Linux, and FreeBSD operating systems. These malware appear legitimate due to code-signing certificates and are regularly updated to avoid detection by antivirus programs.
Once embedded within a target’s networks, the group employs tools that allow it to stealthily avoid endpoint detection, including NetCat shells, Secure Shell Protocol (SSH), and Remote Desktop Protocol (RDP). BlackTech’s primary objective is to acquire administrator privileges over vulnerable network routers, which sets it apart from other threat actors in the field.
The group typically targets routers located at smaller, remote branches of larger corporations where security protocols may not be as stringent. By controlling these routers, BlackTech not only carries out its malicious activities undetected but also blends into the organization’s main IT network, potentially accessing other systems and victims within the target organization.
In an effort to gain and maintain control over routers, while simultaneously hiding its malicious endeavors, the group known as BlackTech executes a sophisticated downgrade attack.
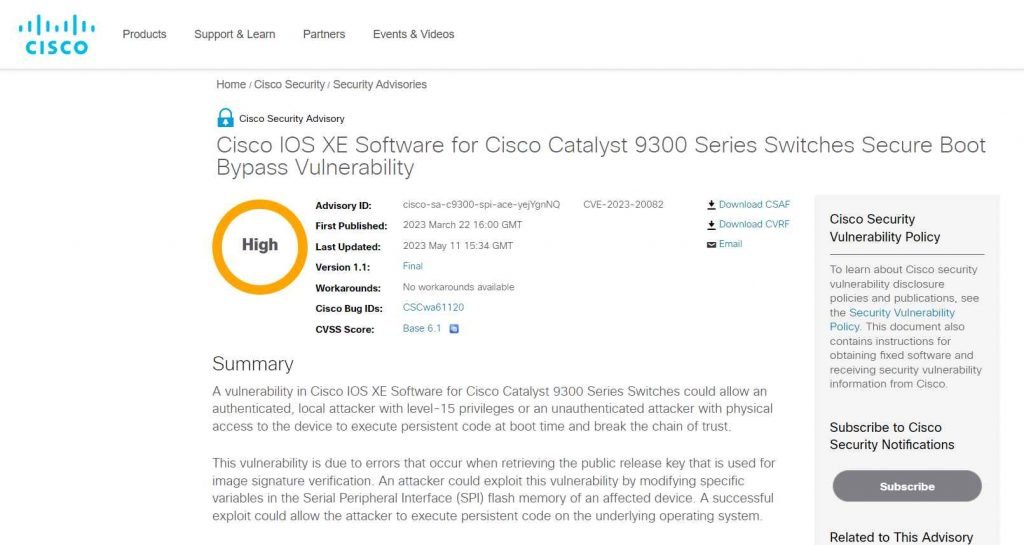
This operation commences with the installation of an outdated version of the router’s firmware. Cisco permits individuals possessing specific privileges on the device to revert the operating system image and firmware to a previous version. The ability to downgrade the firmware is crucial for the attackers to persistently embed themselves in the system. The attackers to ensure their sustained presence and to alter the firmware image for delivering harmful code onto the device, an authentication bypass vulnerability is requisite. Although the joint advisory did not mention particular vulnerabilities exploited, experts referred to CVE-2023-20082. This vulnerability, identified in Cisco Catalyst switches, possesses a medium-risk score of 6.8 on the Common Vulnerability Scoring System (CVSS) and serves as an illustrative example of the potential weaknesses exploited.
Following the initial step of the downgrade attack, BlackTech proceeds to implement “hot patches” on the antiquated firmware residing in the device’s memory. This delicate operation entails modifications to the old firmware without necessitating a system shutdown or reboot. Through this technique, the group adeptly facilitates the installation of a bootloader and subsequently implants its malicious firmware, which is intricately designed with a built-in Secure Shell (SSH) backdoor. This stealthy backdoor grants the group unfettered access to the compromised devices.
Consider finding yourself working on a computer where a malicious actor has stealthily substituted your entire Windows operating system, and it’s done so imperceptibly. Quite a startling scenario to contemplate, isn’t it?
To mitigate the risks posed by BlackTech’s tactics, companies are advised to monitor connections with network devices, review firmware changes, and maintain robust password policies. However, we believethat these measures are merely superficial solutions to deeper, systemic issues in edge security. He advocates for a significant enhancement in the security measures implemented by device manufacturers, or a substantial investment by customers in this traditionally neglected area, to prevent the recurrence of such incidents in the future. Without such steps, the industry is likely to witness similar stories unfolding over the next decade or even longer.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.