Those that work with databases on a regular basis will know that PostgreSQL is more than just a name. It has an impressive history that spans over 30 years, and now it serves as an effective object-relational database system that is open source. Because of its ability to store and grow even the most complex data workloads, it has become the database of choice for a wide variety of applications, ranging from websites to mobile and analytics systems.It has been discovered that the widely used open-source object-relational database system PostgreSQL has a significant security flaw. The vulnerability, identified as CVE-2023-39417, has a significant CVSS score of 7.5 and gives an attacker the ability to execute arbitrary code as the bootstrap superuser if the attacker also has the capability to create databases at the database level.The vulnerability may be exploited in the PostgreSQL extension script if an administrator has installed files of a vulnerable, trusted, non-bundled extension. The vulnerability is present in the PostgreSQL extension script. When using the @extowner@, @extschema@, or @extschema:…@ functions, there is a security flaw because user input is not properly sanitized. This flaw is the root source of the vulnerability.
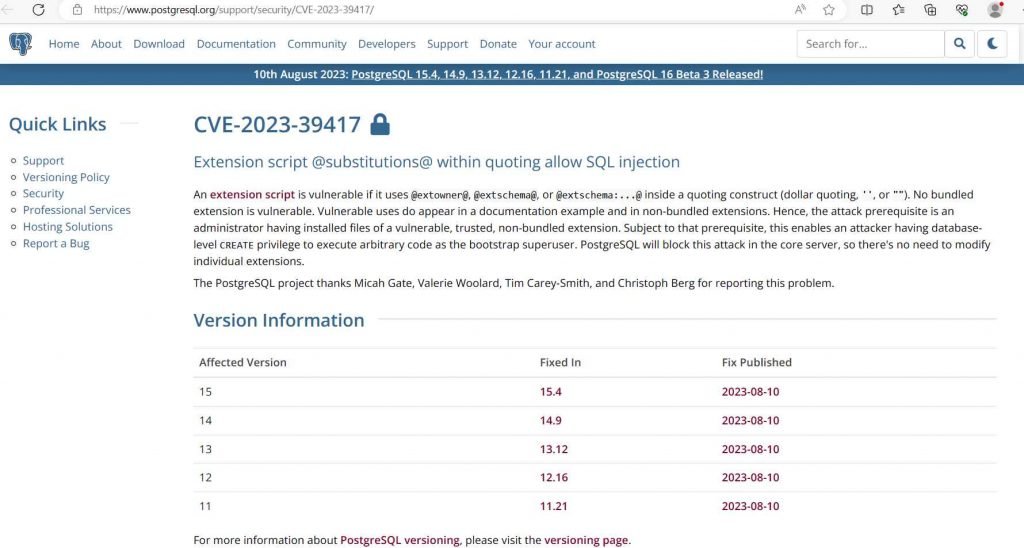
An adversary may take advantage of this flaw by sending malicious data to a PostgreSQL database that is running a version of the program that is susceptible to being exploited. It’s possible that the malicious input will be in the form of a SQL query, or it may be a parameter to a function. As soon as the attacker submits the malicious input, they are able to execute arbitrary code in the context of the bootstrap superuser.
The bootstrap superuser is a unique user account that has full authority over a PostgreSQL database. This account is only accessible via the bootstrap script. This indicates that an adversary who is able to run arbitrary code as the bootstrap superuser has the ability to do whatever they want with the database. This includes stealing data, deleting data, or altering data.
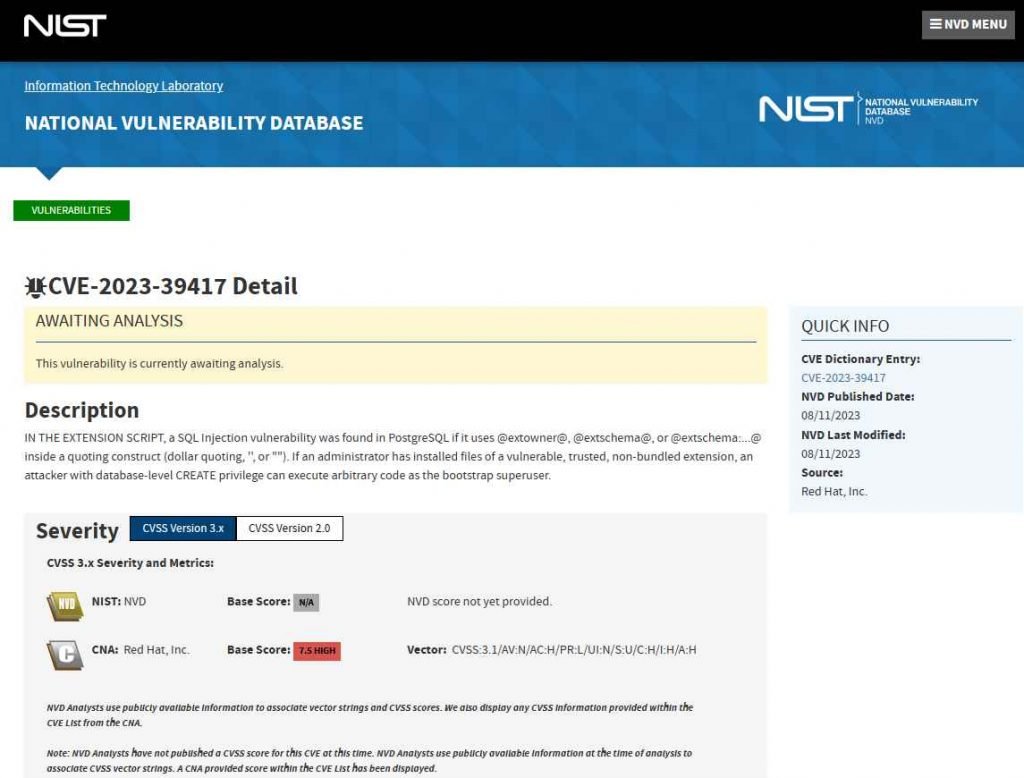
All of the PostgreSQL versions 11, 12, 13, 14, and 15 are susceptible to the CVE-2023-39417 issue. The fixed versions are 11.21, 12.16, 13.12, 14.9, and 15.4. PostgreSQL has made available a patch that prevents this attack from taking place at the fundamental level of the server. The process of remediation is made more straightforward by the fact that users do not have to edit individual extensions. It is imperative that you install this necessary update as soon as possible since the safety of your data relies on it.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.