A group of entrepreneurs hacked the doorbell of their office using services such as Slack, MessageBird and Now
Mollie is a technology company dedicated to payment processing; currently serving more than 50K customers and each day have more employees. When the company reached 80 employees last April, some of its activities were transferred to a new space right in front of its main offices.
Instead of traditional doorbell systems, Mollie’s owner installed one that works with a SIM card. Every time a visitor rings the bell, a call is made to a cell phone that is located somewhere in the office. Then, any of Mollie’s employees can answer the phone and press “3” on the keyboard to open the office door. Still, due to the use of noise-isolation headphones, most employees never hear the doorbell ring.
Mollie’s employees began to think of an alternative: Wouldn’t it be amazing to be able to open the door using your own Slack bot?
Mollie’s cyber security organization managers discovered that MessageBird, a communications service, had just launched a new product: Flow Builder. This allowed them to create a visual flow for incoming calls through the phone number purchased through MessageBird.
For Mollie’s cyber security organization team it was easy enough to establish a basic flow for:
- Greet visitors with the phrase “Welcome to Mollie Studios. Please wait while we find someone to open the door for you”.
- Send an HTTP request to the Mollie web server.
Or, if the doorbell sounded out of office hours:
- Tell the visitor: “Mollie Studios is closed right now. Contact a Mollie employee for urgent matters” and end the call.
To accomplish this, Mollie’s team configured a basic Node.JS web server using Express that sends a message to a specific Slack channel each time a call is made.
MessageBird sends a couple of additional parameters with each request, including a callID. When a new request comes in, an API call is made to MessageBird to verify if this voice call really happened and if it happened within the last 2 minutes. The destination and source query parameters of the incoming call are also used and compared to the MessageBird data. This would ensure that only “real” calls to the doorbell will trigger Slack notifications.
If the call is legitimate, a random token is generated that will be stored in the memory.
The next step was to attach interactive buttons to the Slack notification. The “Open door” action was attached to each message sent by the bot. Each time someone presses that button, Slack makes a call to the Mollie web server and verifies the tokens that have passed to the callback URL with the token stored in the memory during the previous step.
In order to open the door (after a Mollie employee has pressed the button attached to the Slack notification), MessageBird must be asked to press the “3” button on the phone keyboard during the call. Unfortunately, this is not something that MessageBird can do, as all communications are made through API, so Mollie’s cyber security organization managers had to find a more creative solution.
The good news is that MessageBird allows you to add a step to the call flow diagram that will capture a dynamic call flow from an external URL. This can be used for the doorbell to interpret a person pressing “3” on the phone’s keyboard. To understand how someone can send the “open” signal to a doorbell using a dynamic call flow, it is important to know the basics of telecom signage.
In telecommunications, signage works use dual-tone multi-frequency signaling (DTMF) technology. That means that when someone presses a button on the phone keyboard, the sent sound has a high frequency and a low frequency. In other words, if you emit a sound with a related high and low frequency, you can interpret the number related to that frequency.
The cyber security organization managers at Mollie recorded the sound that their cell phone did when the “3” button was pressed and stored it as a static .wav file on their web server. The missing part is that they just needed to get MessageBird to recognize the sound and the door would open itself.
To accomplish this, a few more steps were added to the MessageBird call visual flow. Each time MessageBird makes the call, the Mollie server verifies if someone authorized to open the door for the last 10 seconds. Otherwise (which means no one pressed the “open door” button on Slack), it will return a 200 OK response code. MessageBird will wait for 1 second and try to recover the reestablished call flow.
If someone pressed the “open door” action button and the authorization tokens match, the following flow will be returned:

MessageBird will play the same sound you would hear when you press “3” on the phone’s keyboard, and the doorbell opens the door.
Real-time deployment
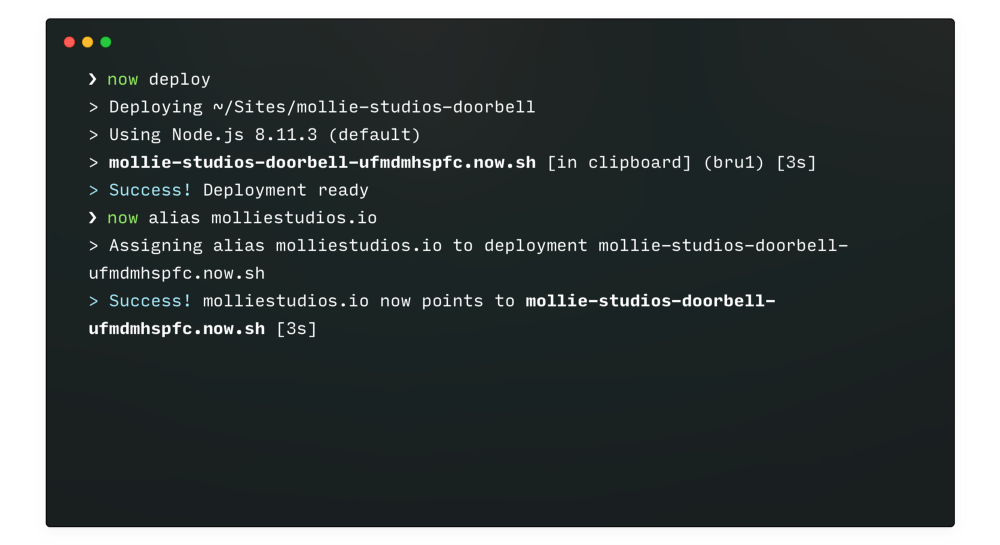
Once the web server was ready, in Mollie they had to implement it somewhere. As it was a small parallel project, the company’s cyber security organization managers used the ZEIT hosting service called Now. This would allow them to deploy the Node.js in seconds, simply by executing the command “Now“.
Every time they make a change, they have to run two commands and everything was implemented in the cloud in one minute.
Mollie is constantly working to solve problems using the latest technological developments by various companies, which has enabled them to achieve constant growth in the payment processing market.











