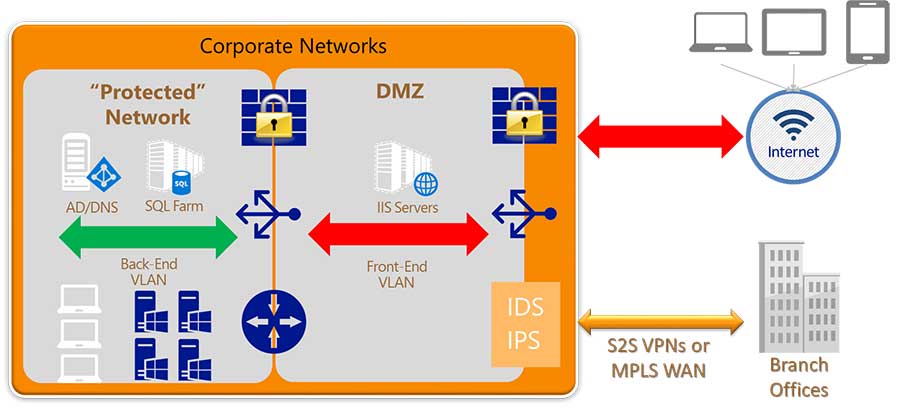
The objective of network security assessment services is to keep data assets secure and protect the enterprise IT infrastructure. Typically, businesses are threatened by technology risks and vulnerabilities for being connected to internet or for handling confidential client information. There are statistical evidences about network security supported by enterprise network security company, which states that in countries such as Mexico, Brazil, United States, Colombia, Argentina, UAE, India; two out of three companies suffer attacks on their IT networks.
Many companies believe that by simply installing an antivirus or firewall in their networks, they are free of risks. This is a very common error as there are risks associated with these, but there are many other risks which can’t be fixed by only antivirus or firewall. To preserve enterprise network security, they must consider all types of IT risks. IT risks can be classified into external risks and internal risks. External risks originate outside the company’s network such as an external network hacker. Internal risks originate within the network such as an employee or an external hacker who has access to network resources.
According to enterprise network security training course professor, many risks arise due to inefficient network security solutions that companies have and because of lack of knowledge related to the implementation of enterprise network security solutions. Network security solutions protect enterprise networks and resources from external and internal risks. As per case studies from an enterprise network security company, network security is the key for meeting the data protection standards and gain customer trust. Below are some of the ways for improving Ethernet and wireless security.
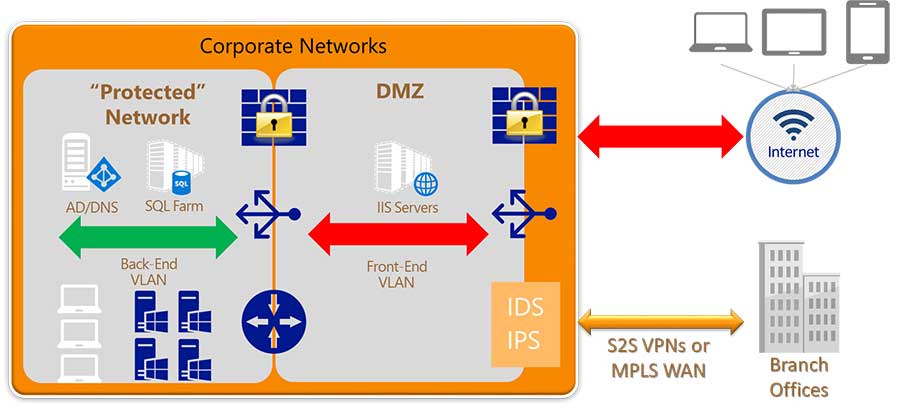
Ways to improve Ethernet network security
If you are configuring a computer network, you can follow some of the below mentioned security mechanisms recommended by enterprise network security company.
- As per enterprise network security training course; to increase security in the network, you should enable automatic software updates for each computer and network device. Normally firmware and operating systems automatically install important updates. An update may include patches for some vulnerabilities or an upgrade to improve the user experience and performance.
- Use a firewall that could prevent hackers from gaining access to network resources. A firewall provides access control and filters all network communications. Implementing other enterprise network security solutions along with firewalls can isolate networks to prevent certain types of data flow. According to enterprise network security company consultants; some firewall can allow access to the local network from the Internet if the user has logged in as an internal user. Some firewalls also have Anti-Spam functionality or you must use a separate Anti-Spam solution in the network.
- Virus can get into your computer for spam, hard disk, USB, CDs or files downloaded from Internet. As there are new kinds of viruses every other day, antivirus software must be updated periodically. Antivirus help detect and sometimes in the removing virus. According to the experience of enterprise network security company consultants; there are different types of antivirus solutions in the market. Consultants of enterprise network security solutions suggest that general users can use free antivirus like Avast but enterprise users should use appropriate solution depending on the type of infrastructure.
- Use IDS- IPS (intrusion detection system and intrusion prevention system). IDS, IPS are network security services that enable intrusion detection and intrusion prevention. An IDS / IPS proactively detects complex traffic patterns and gives an ability to respond to any imminent attack on your network. According to enterprise network security services experts, intrusion detection and intrusion prevention system is a software / hardware used to detect cyber attacks over a computer or a network. The events generated by IDS / IPS should be supervised by your company’s team or company can take the help of enterprise network security company which can analyze network traffic in real time with the help of network security assessment services.
- VLAN (Virtual LAN) is a method of creating independent logical networks within a computer network. A computer network can have multiple virtual networks. VLAN is one of the important enterprise network security solutions that divide groups of network users in a real physical network into logical segmented networks. Enterprise network security training course professor explains that VLAN network is a network of computers that behave as if they were connected to the same switch. You can configure VLANs through software rather than hardware, which makes them considerably flexible. To deploy more security, you can learn how to configure Private VLAN, VLAN Micro with the help of network security training course.
- An access control list or ACL used to implement logical security. ACL is one of the enterprise network security solutions that can help determine the appropriate access permissions for a network resource. ACL filters network traffic and only allows network traffic based on some condition. ACL can also be used to filter out traffic flow in computers, routers and network switches. According to network security assessment services specialists; the access control list is a basic necessity for any network. You must set rules detailing service ports, domain names, and terminal names along with the ACL permissions. A combination of VLAN and ACL is very good for security and you can easily learn how to configure VLAN ACL’s with the help of network security course.
- Implement network security solutions such as IPsec (Internet Protocol Security) for encryption. IPsec is a set of protocols used for secure communications at the network layer and the transport layer, both TCP and UDP. IPsec helps in authentication and encryption of data packets. According to network security assessment services experts, IPsec is very flexible because it can be used to protect Internet Protocol (IP) and Transport protocol (TCP, UDP). You can use IPsec with applications that use SSL or TLS. You can also use VPN for critical communications or implement a complete IPsec solution.
- Install RADIUS, TFTP servers depending on the business requirements along with other enterprise network security services & solutions mentioned before.
- Enable logs server, which will enable you to record all activity on the network. According to enterprise network security training course professor; this part is very important for tracking all the hacking incidents.
- Audit configurations of network devices and select a configuration knowing its purpose. You must also change the default settings and configurations of switch, router and other network devices. For network application security, network security services expert advice that you should disable any unused services. Thus you should check the running services related to all network devices & applications and disable or uninstall the service that you are not using.
- You can also take help of enterprise network security company or provider to implement security, backup policies and to do network security audit with intrusion detection and vulnerabilities testing.
Ways to improve wireless network security
If you are configuring a wireless network, you can follow some of the below mentioned security mechanisms recommended by enterprise network security company.
- You must configure a security key of wireless network with Wi-Fi Protected Access 2 (WPA2-PSK) enabled. With encryption enabled, no one can connect to your network without the security key and is very difficult to do brute force. This would help prevent attempts of unauthorized access to the network and communications. You must choose a very strong security key so that dictionary attacks cannot crack the password.
- You must change the name and default administrator password on your router or access point. In addition you should change default wireless network name known as default network identifier (SSID). You can also use various wireless network security solutions that will change the keys, passwords and SSID periodically.
- You must select the location of the router or access point carefully so that the signal does not reach outside your facilities.
- You can filter MAC addresses and allow WiFi access to known devices. There is also an option to hide SSID so that it is not visible in regular search of available networks.
These network security solutions are basic for any kind of security implementation for wired and wireless network. For more secure networks, you should take help of an enterprise network security company. If you have question “how to learn network security”, you can take our enterprise network security training course for learning network security and implementing the same.
Source: http://www.iicybersecurity.com/enterprise-network-security-assessment-company.html