Palo Alto Networks’ Unit 42 researchers have revealed shocking details of a new malware that’s compromising Windows containers to target Kubernetes clusters. Researchers have dubbed it Siloscape.
It is regarded as an unusual malware that focuses on Linux as the preferred OS for managing cloud environments and applications.
Another interesting aspect of the report is that the researchers could access the C&C Server and identified 23 active victims of the malware, and in total, there were 313 victims.
What are Kubernetes Clusters?
Developed initially by Google; Kubernetes are now being maintained by the Cloud Native Computing Foundation. It is an open-source system used to automate the scaling, deployment, and management of containerized services, workloads, and applications over host clusters.
It also organized apps containers into nodes (physical/virtual machines), pods, and clusters. Multiple nodes form clusters, which are then managed by a master cluster that coordinates tasks like updating or scaling apps.
Malware Discovered in March
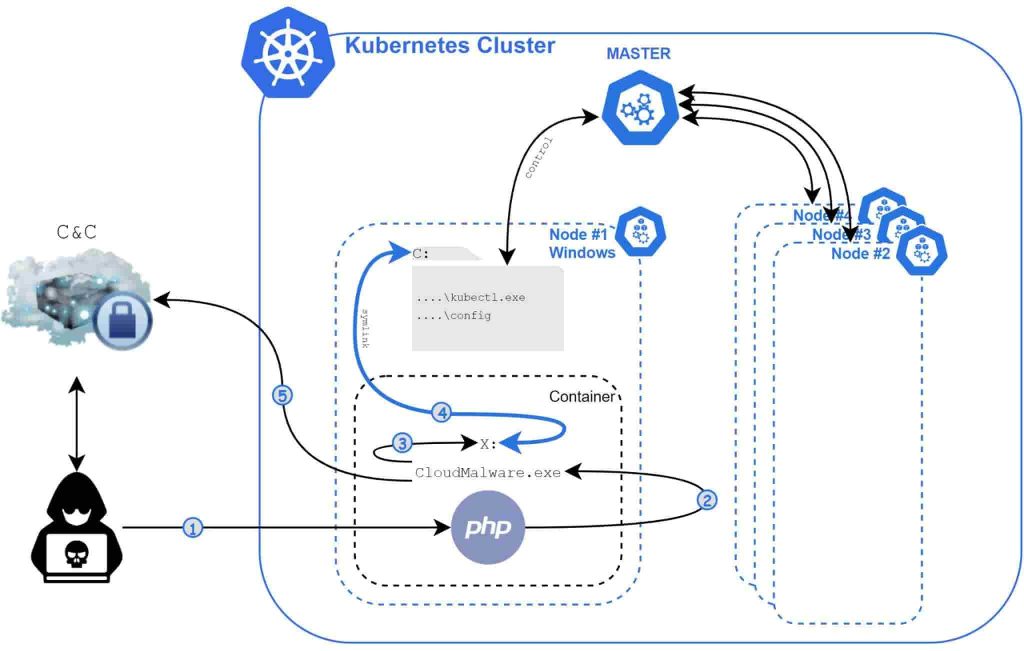
According to Unit 42 researchers, the malware was discovered in March 2021. It has been named Siloscape because it aims to escape Windows containers through a server silo. It uses Tor proxy and .onion domain to communicate with its C&C Server. And, the malware operators use it to exfiltrate data, send commands and manage malware.
How does it attack?
The malware is labeled as CloudMalware.exe. Instead of using Hyper-V isolation, it uses Server to target Windows containers and launches attacks by exploiting known and unpatched vulnerabilities to gain initial access against web pages, servers, and/or databases.
It then achieves remote code execution on the container’s underlying node using various Windows container escape techniques like impersonating the container image service CExecSvc.exe to obtain SeTcbPrivilege privileges.
“Siloscape mimics CExecSvc.exe privileges by impersonating its main thread and then calls NtSetInformationSymbolicLink on a newly created symbolic link to break out of the container. More specifically, it links its local containerized X drive to the host’s C drive,” researchers noted.
If the malware manages to escape, it creates malicious containers, steals data from running/active applications in compromised clusters, or loads up cryptocurrency miners to leverage systems’ resources to mine for cryptocurrency and earn profits for malware operators.
Perfect Obfuscation in Place
The malware developers have tried every trick up their sleeve to keep the malware obfuscated. Its modules and functions can be deobfuscated only at runtime.
Additionally, to keep its activities hidden and make reverse-engineering complex, it uses a pair of keys to decrypt the password of the C&C Server.
The keys are generated for every unique attack. Researchers noted that hardcoded keys make every binary difficult from the rest. It becomes challenging to find its hash anywhere, making it impossible to detect the malware by hash only.