PowerShell scripts seen in around 38% of malware incidents. Microsoft’s PowerShell task automation framework is becoming one of the most popular tools for coding and enhancing malware, a Carbon Black study has discovered.
Aggregating data from over 1,100 separate investigations from 20 security firms, Carbon Black says that PowerShell was used in 38 percent of all the attacks they analyzed.
Respondents said that, in 31 percent of all the situations, their clients reported not receiving any warnings about the ongoing attacks.
PowerShell, a favorite tool for targeted attacks and commodity malware
In 87 percent of cases, the PowerShell malware was part of a shotgun approach, while for the rest, the malware was part of a targeted attack, specific to hacker groups and state-sponsored actors.
By shotgun approach malware, we mean common malware such as ransomware, click fraud bots, and other threats where the attacker doesn’t care whom they infect as long as they infect someone.
Carbon Black claims that over half of these incidents were related to Vawtrack, a banking trojan that heavily uses PowerShell in its source code.
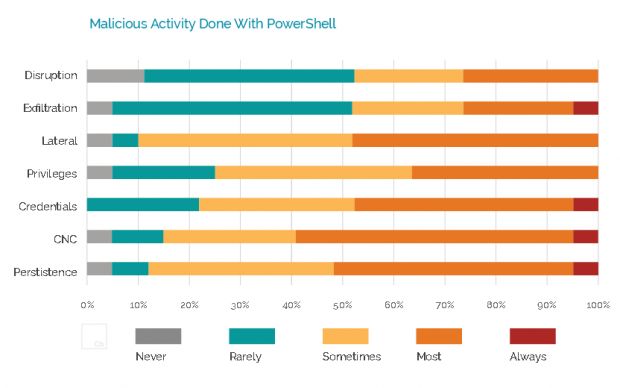
Respondents said that, most of the time, the PowerShell-based malware was distributed via social engineering techniques and that it targeted mostly corporate networks and financial data, aiming to steal information or disrupt services.
Detecting PowerShell malware is as impractical as banning PowerShell
Because PowerShell is a ubiquitous technology within the Windows ecosystem, detecting PowerShell-based malware is almost impossible, since there’s no technical method of distinguishing between good and malicious PowerShell source code.
For this reason, security researchers expect PowerShell to become a prevalent technology in malware design, but also because toolkits like PowerSploit, PowerShell Empire, p0wnedShell, and the Social-Engineer Toolkit are making it easier to use PowerShell exploits out of the box.
As for blocking PowerShell, security researchers say this is impractical. “Unlike other common technologies such as Java and Adobe Flash, which IT administrators can more easily remove or ban, many organizations and applications rely on PowerShell to manage their critical systems.”
One of the most recent PowerShell-based malware families is the PowerWare ransomware.
More intricate details are offered in Carbon Black’s ‘PowerShell’ Deep Dive report, available for download.