Some fake piracy websites have also been found distributing Crypto Bot and Raccoon Stealer malware in cracked software.
Sophos Labs’ security researchers have published a report on the emerging new threat of droppers-as-a-service. According to their research, droppers for hire are installing unwanted content and malware on devices of those who use cracked software of popular business/consumer applications.
SEE: This malware hides behind free VPN, pirated security software keys
The report’s authors Sean Gallagher and Yusuf Polat noted that paid download and droppers services, although they have been operating for a long time, their continuous evolution is a cause of concern for the cyber community. They identified several networks using some basic tactics.
“All of these networks use search engine optimization to put a “bait” webpage on the first page of results for search engine queries seeking “crack” versions of a variety of software products.”
Droppers Delivering Malicious Backdoors and Info Stealers
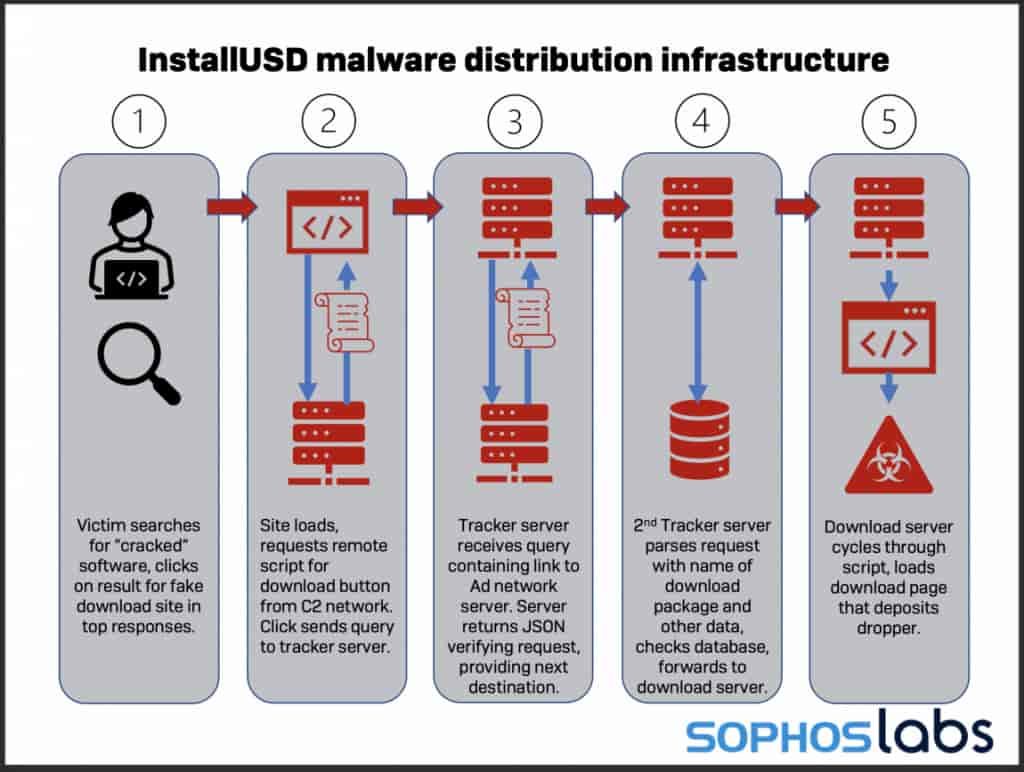
Sophos researchers wrote that attackers are using numerous bait pages hosted on WordPress. These bait pages contain download links to different software packages. When a user clicks on these links, they are redirected to a malicious website containing unwanted browser plug-ins and malware.
The researchers identified droppers delivering information stealers like Crypto Bot and Raccoon Stealer, as well as backdoors, including Glupteba. Though such malware are easily detectable by the security software, since malicious droppers are in encrypted archives, their files cannot be detected until they get unpacked.
In their report, Sophos researchers noted that:
“During our recent investigation into an ongoing Raccoon Stealer campaign, we found that the malware was being distributed by a network of websites acting as a “dropper as a service,” serving up a variety of other malware packages—often bundling multiple unrelated malware together in a single dropper.”
What are the Possible Repercussions?
There are several drastic repercussions if your device gets targeted by Dropper-as-a-Service. As per Sophos Labs researchers, there’s tremendous demand for account access credentials, and such paid services allow novice and less-skilled cybercriminals to carry out “bulk credential theft and cryptocurrency fraud at a minimal cost.”
SEE: Malicious Office documents make up 43% of all malware downloads
Moreover, the Dropper for Hire services providers has bundled a wide range of malicious content in each dropper to maximize their profits. With millions of people working from home using personal devices, the risk of downloading malicious droppers can expose businesses to a broad range of entry-level adversaries.
How to Stay Protected
Researchers suggest that businesses and organizations should implement stringent security settings and policies and review the effectiveness of their security software to detect/block unwanted, malicious downloads before they cause any damage. They must adopt a robust approach to web filtering as the malware could be hiding inside the network.
So, a web filter will scan regular downloads, protect the network from connecting to malicious servers, and will inspect encrypted traffic too, which is extremely important as most malware use Transport Layer Security encryption for communications.
“It is also good security practice to avoid downloading and installing unlicensed software from any source. Always check first to make sure it’s legitimate,” researchers added.