Defibrillators are electronic devices manufactured to save the lives of people with life-threatening heart conditions such as Hypertrophic Cardiomyopathy (HCM). But now, according to the Department of Homeland Security (DHS), Medtronic defibrillators are vulnerable to cyber attacks allowing hackers to remotely control the device within “short-range access.”
In total, 20 Medtronic products are vulnerable affecting over 70,000 devices including 16 different implantable heart defibrillator being sold worldwide while other devices include home monitors and programmers, etc.
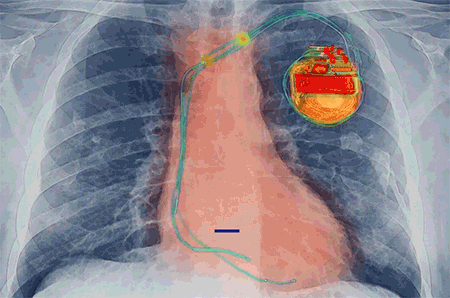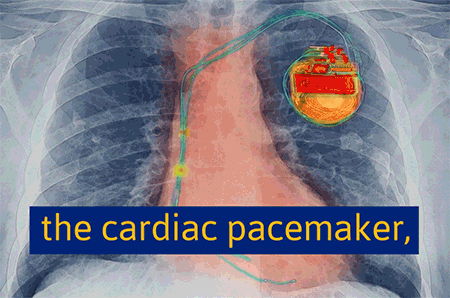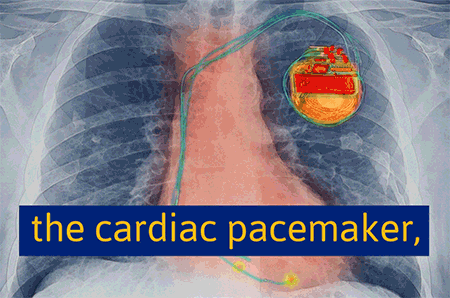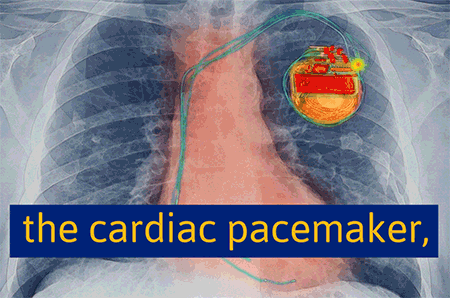
An implantable defibrillator is a device placed under the skin near the collarbone to monitor the heart activity of the patient. In case of sudden cardiac arrest where the heart suddenly stops functioning and pumping blood, the defibrillator is programmed to hit the heart with a high voltage of electric shock to bring the heart back to life.
According to a medical advisory issued by DHS, these defibrillators are currently at risk of being hacked by malicious elements who can alter with adjacent short-range access to a vulnerable device can inject, alter, replay, modify and intercept data within the telemetry communication.
The advisory further revealed that the problem lies in the Conexus telemetry system used by Medtronic’s device. This system does not implement any authorization or authentication leaving device vulnerable to cyber attacks.
This communication protocol provides the ability to read and write memory values to affected implanted cardiac devices; therefore, an attacker could exploit this communication protocol to change memory in the implanted cardiac device, said the advisory.
List of vulnerable devices:
- MyCareLink Monitor, Versions 24950 and 24952,
- CareLink Monitor, Version 2490C,
- CareLink 2090 Programmer,
- Amplia CRT-D (all models),
- Claria CRT-D (all models),
- Compia CRT-D (all models),
- Concerto CRT-D (all models),
- Concerto II CRT-D (all models),
- Consulta CRT-D (all models),
- Evera ICD (all models),
- Maximo II CRT-D and ICD (all models),
- Mirro ICD (all models),
- Nayamed ND ICD (all models),
- Primo ICD (all models),
- Protecta ICD and CRT-D (all models),
- Secura ICD (all models),
- Virtuoso ICD (all models),
- Virtuoso II ICD (all models),
- Visia AF ICD (all models), and
- Viva CRT-D (all models).
It is worth mentioning that these vulnerabilities were identified and reported by researchers from the University of Birmingham and University Hospital Gasthuisberg Leuven. The good news is that these vulnerabilities can only be exploited if the attacker is nearby the patient using Medtronic product.
Medtronic, on the other hand, has acknowledged the issue and plans to release software patches to fix these vulnerabilities. However, the company maintains that there has been no incident involving the exploitation of these vulnerabilities to cause physical damage to patients.
Moreover, Medtronic is urging users not to connect unapproved devices to home monitors through USB ports or other physical connections and only use those devices taken directly from a healthcare provider.
This, however, is not the first time when life-saving defibrillators have become life-threatening due to security vulnerabilities. In February Last year, Journal of the American College of Cardiology published a report stating how pacemakers and defibrillators can be hacked to turn on and off posing danger to the patient’s life.
In May last year, Abbott had to recall around 350,000 implantable cardioverter defibrillators (ICD) and pacemakers for firmware upgrading because these devices were identified to be containing life-threatening flaws and vulnerable to exploitation.