So far, the ongoing phishing attack has utilized more than 350 unique domains to target Microsoft Office 365 users.
Microsoft has warned about a new widespread phishing campaign in which scammers are abusing open redirect links to divert users to malicious websites and steal MS Office 365 credentials.
In a detailed report, the IT security researchers at Microsoft wrote that this campaign is widespread but didn’t clarify the number of attacks they detected. It is suspected that some phishing emails sent in this campaign had January dates, while researchers claim the campaign is still active.
Scammers using social engineering to lure users
According to the report published by Microsoft, in this campaign, threat actors are using social engineering techniques to impersonate popular productivity tools/services so that users are compelled to click malicious links.
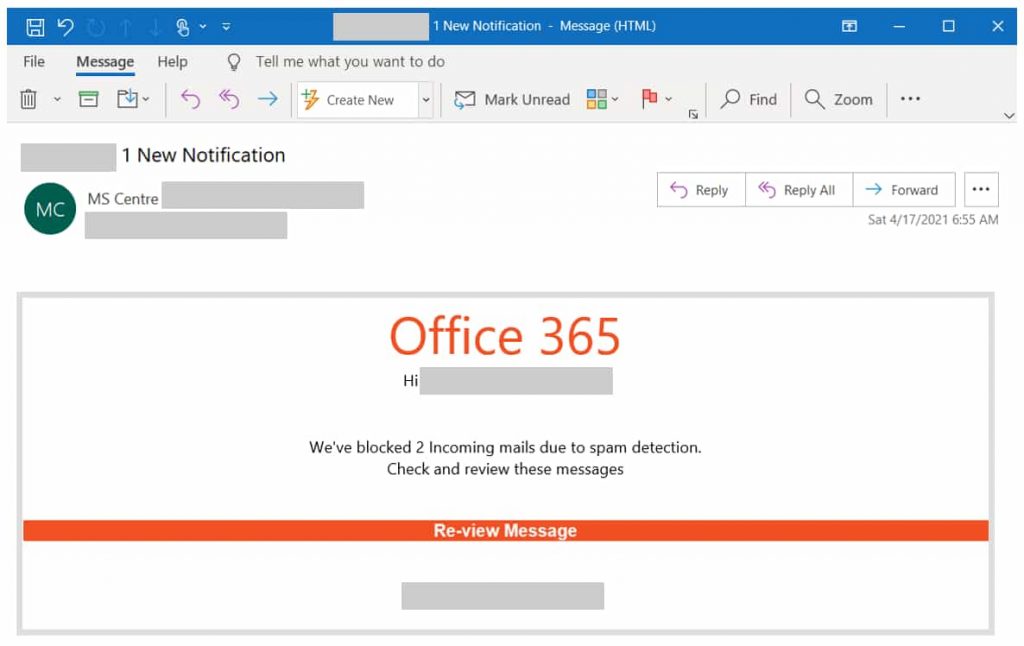
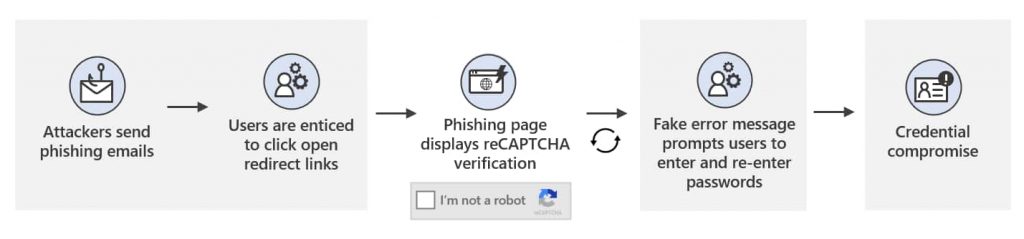
For instance, in some attacks, attackers deploy an inauthentic CAPTCHA verification page to take unsuspecting users to a phishing site and harvest their credentials. When users complete this CAPTCHA page, they receive a malicious domain designed to look like an authentic Office 365 login page.
In its blog post, Microsoft 365 Defender Threat Intelligence Team explained that:
“The site is prepopulated with the recipient’s email address to add legitimacy to the request. This technique leverages familiar single sign-on (SSO) behavior to trick users into keying incorporate credentials or other credentials associated with the email address.”
How do attackers abuse Open Redirect links?
Open redirect is a common feature used in email-based sales and marketing campaigns to redirect customers to particular landing pages to track click rates and other website tracking metrics.
SEE: ‘Safe Documents’ tool in Office 365 will automatically detect malware
Apart from social engineering tactics, this particular campaign is unique because scammers are using open redirect links to trick users into visiting malicious links. This also helps attackers evade detection by security tools like email gateways.
Fraudsters abuse open redirect links so that users land on a phishing page. Microsoft researchers revealed that attackers could link a trusted domain to any URL through open redirect links and embed the final malicious URL as a parameter in this campaign.
“For instance, users trained to hover on links and inspect for malicious artifacts in emails may still see a domain they trust and thus click it,” researchers noted in their blog post.
Attackers used 350+ unique domains.
So far, the scammers have used a wide range of sender domains to evade detection. According to Microsoft, threat actors have used more than 350 unique domains so far, including free email domains from various country-code top-level domains, attacker-owned domains, compromised authentic domains, and domain-generated algorithm domains.
SEE: 10 Crucial Security Tips to Reduce Data Loss in MS Office 365
The fraudsters also use various subject lines in phishing emails as part of their social engineering techniques. These include notifications to reset passwords or alerts for a Zoom meeting, according to the report.
“Since the actors set up open redirect links using a legitimate service, users see a legitimate domain name that is likely associated with a company they know and trust.
We believe that attackers abuse this open and reputable platform to attempt evading detection while redirecting potential victims to phishing sites,” researchers explained.