TeaBot malware is in the early stages of development yet, so far, it has targeted 60 banks all over Europe.
The Threat Intelligence and Incident Response (TIR) team at Italy, Milan-based online fraud prevention firm Cleafy’s has discovered a new Android malware that is targeting unsuspected users across Europe since January 2021.
Dubbed TeaBot by researchers; the malware is in the early stages of development yet equipped with capabilities like remotely taking full control of a targeted device, steal login credentials, send and intercept SMS messages for additional scams including extracting banking data.
So far, Cleafy’s threat research team has identified more than 60 banks targeted by TeaBot malware in European countries like Italy, Spain, Germany, Belgium, and the Netherlands. The malware supports 6 different languages German, English, Italian, French, Spanish, and Dutch.
Watch out: New Android malware spreads through WhatsApp
Other capabilities of this malware let its operators delete existing apps from the device, change audio settings such as muting the device, read its phone book, read the ‘phone state’ meaning attackers can identify the victim’s phone number, the status of ongoing calls, current cellular network information, etc.
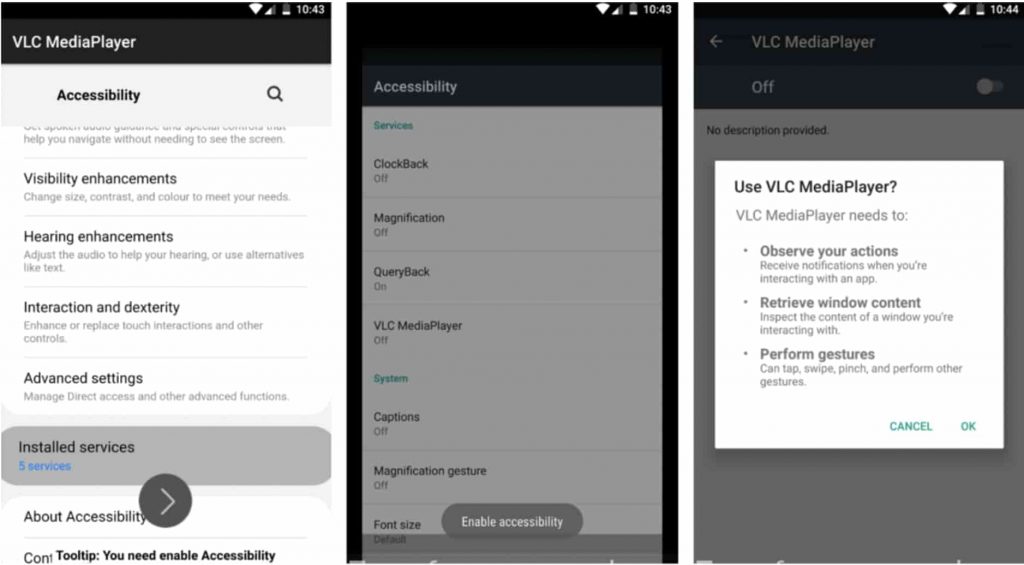
Furthermore, TeaBot malware constantly takes screenshots of the compromised device and abuses Android Accessibility Services by showing up a popup that forces victims to accept the accessibility service permissions. This lets the malware act as a keylogger and tracks everything victim does on their phone.
In its report, Cleafy’s TIR noted that:
We assume that TeaBot, similar to Oscorp, is trying to achieve real-time interaction with the compromised device combined with the abuse of Android Accessibility Services bypassing the need for a “new device enrollment” to perform an Account Takeover scenario (ATO).
In addition, upon infecting the device TeaBot steals Google Authentication 2FA codes, compromises other accounts on the device, and last but not least it also disables the Google Play Protect feature.
For your information, Google Play Protect automatically scans all of the apps on Android phones and works to prevent the installation of harmful apps.
SEE: New Android malware poses as “System Update” to steal your data
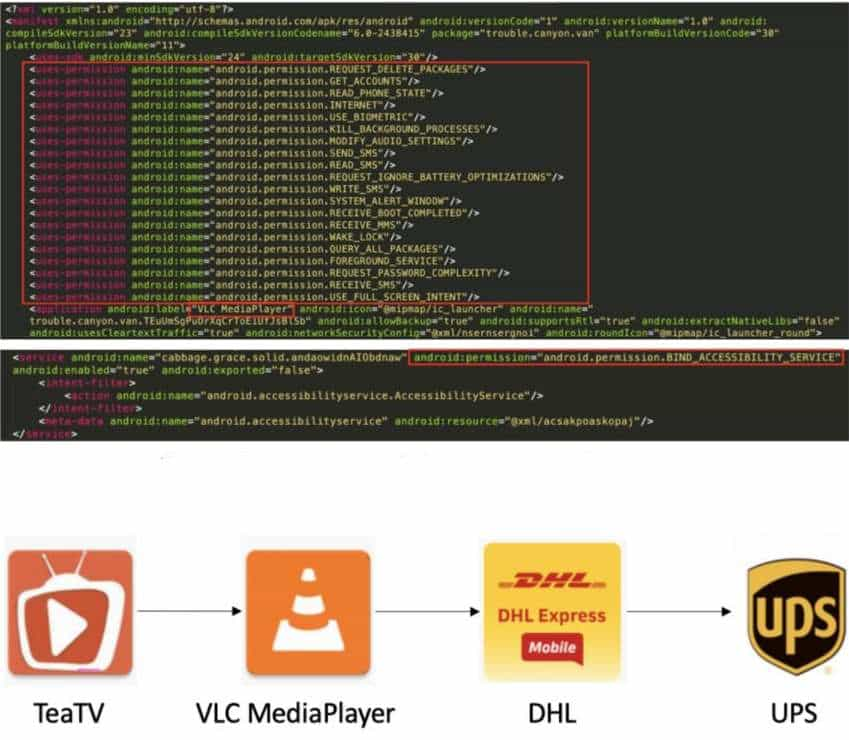
According to researchers, the threat actors behind TeaBot malware initially used a malicious app called “TeaTV” to spread its infection. However, in April 2021, the app’s name was changed to pose as some of the popular apps such as DHL, UPS, VLC MediaPlayer, and (now shut down) Mobdro.
It is worth noting that the infamous Flubot banking trojan also uses the same decoy to infect Android devices yet the researchers did not mention any connection between the two malware.
Nevertheless, if you are an Android user make sure of the following things:
- You are scanning your phone regularly for the latest threats
- You have installed all the latest Android updates on your phone
- You avoid downloading unnecessary apps from third-party sites and even from Google Play Store.