The new Android ransomware was initially being spread through Reddit and XDA-Developers’ forum.
A new type of Android ransomware attack has been identified which has been targeting unsuspected users worldwide. This ransomware, known as Android/Filecoder.C, has been active since July 12th, 2019 and hides behind a game. According to researchers from ESET, the campaign began to spread through pornographic posts on forums like Reddit and XDA-Developers.
The gaming app is an online sex simulation game. But in the background, it launches contact with a Command & Control (C&C) server to initiate a process of encrypting the files present on the victim’s device. Basically, the app hijacks files on the infected device and requires payment for them to be released.
This practice is similar to WannaCry ransomware, which did the same with Windows computers. The difference is that unlike WannaCry, Filecoder does not lock the device, only its files.
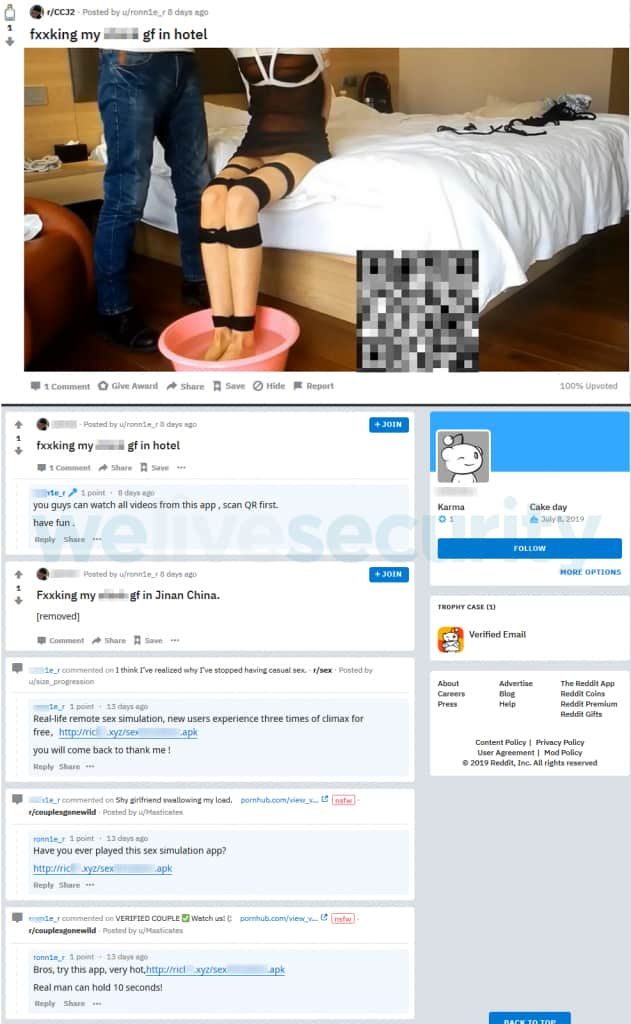
The screenshot shows how crooks have been spreading Android ransomware through Reddit. (Credit: WeLiveSecurity)
When trying to access any of the encrypted files, the user is surprised by an image that requests a bitcoin amount to access the key that will release them. In addition to the recovery amount, the screen displays a message that the data will be deleted within 72 hours if the amount is not paid. It is unclear whether the data is deleted after 72 hours or not.
The Filecoder ransomware is encrypted with asymmetric and symmetric encryption which generates two keys including public and private key which uses RSA-1024 public key.
This “hardcoded key” is an RSA-1024 public key, which can’t be easily broken, hence creating a decryptor for this particular ransomware is close to impossible. Hat tip goes to Alexey Vishnyakov from Positive Technologies who drew our attention to this inaccuracy, wrote Stefanko in his blog post.
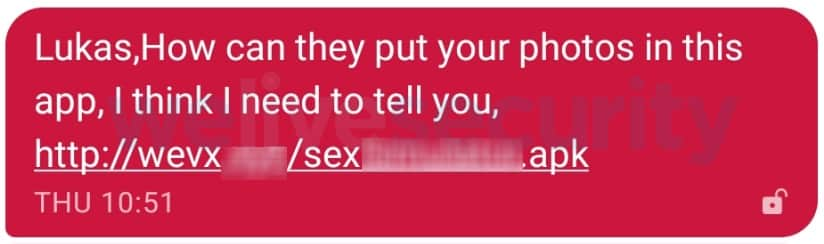
After the attack, the app accesses the phonebook and starts sending text messages to infect more devices. The sent messages talk about a link to an app that is allegedly using the victims’ photos. In an attempt to hide the real address, hackers used URL shorteners including bit.ly.
What’s worse is that this Android ransomware is capable of sending messages in 42 languages. However, as of now, the number of Android devices affected by Filecoder is unknown but upon inspecting the bit.ly URL link posted on Reddit and XDA-Developers, it was noticed that the link was clicked 59 times, with most of the clicks coming from China, the US, and Hong Kong.
This ransomware joins other Android security threats such as Agent Smith, LeakerLocker and DoubleLocker, etc. This, however, is not the first time when pornography app is targeting Android devices with ransomware.
If you are using an Android device watch out of Filecoder ransomware, refrain from clicking links on online forums, avoid apps from third-party app stores, download apps only when necessary and being careful about the permissions requested by apps.
Moreover, use a VPN when browsing, install reliable anti-virus software, keep your device updated and scan it regularly. You can choose any anti-virus program from these two lists (1), (2). Stay safe online!