This week, Microsoft security teams reported the discovery of a phishing campaign characterized by the inclusion of a novel technique that consists of attaching a malicious device to the network of the affected organization, trying to spread the infection. This campaign was detected in countries such as Australia, Indonesia, Singapore and Thailand.
The cyberattack is divided into two main stages. In the first stage, attackers steal the credentials of exposed users in the affected organizations to subsequently access the compromised networks and expand their hacking activities beyond the reach of the malicious email.
According to Microsoft, connecting a malicious device allows threat actors to spread the attack very discreetly, which experts already consider a growing trend in cybercrime. The researchers also mention that the attack works best against organizations that do not use multi-factor authentication, since it is enough to know the passwords of users to complete the intrusion.
Apparently, it all starts when affected users receive a Phishing email branded with DocuSign, as shown in the following screenshot:
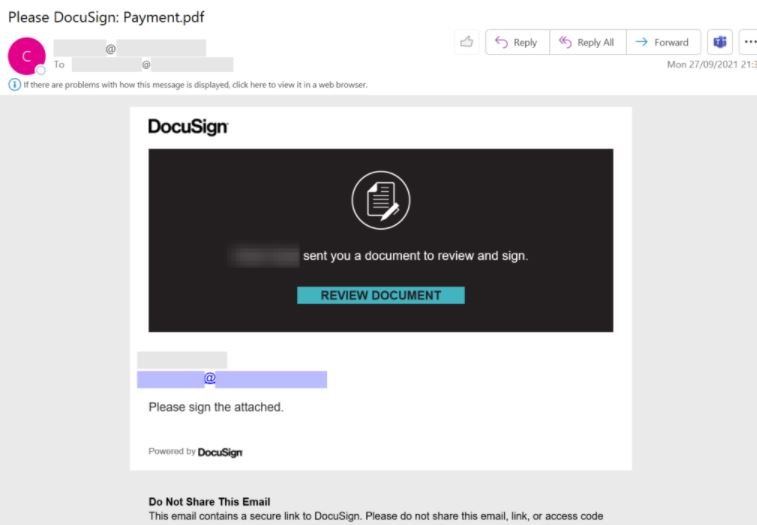
The threat actors employed a set of phishing domains registered under the .xyz top-level domain. This URL domain can be described with the following regular expression syntax:
UrlDomain matches regex @”^[a-z]{5}.ar[a-z]{4,5}.xyz”
At this point a unique phishing link is generated for each email, with the victim’s email address encoded in the query parameter of the URL. After clicking on the link, the target user will be redirected to a phishing website on newdoc-lnpye.ondigitalocean.app posing as an Office 365 login page.
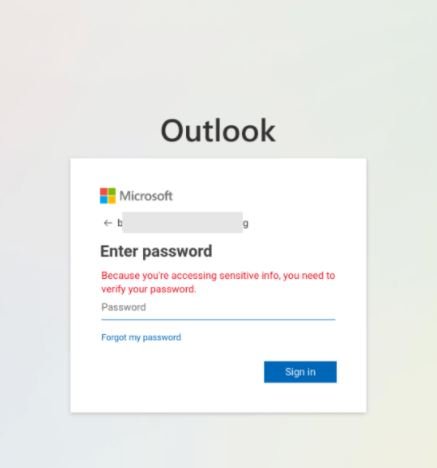
When hackers obtain the target user’s credentials, they will use them to establish a connection to Exchange Online PowerShell. This remote connection allows attackers to establish an inbox rule through the New-InboxRule cmdlet, deleting certain messages based on some keywords; the arbitrary inbox rule allows hackers to avoid detection by removing error reports, spam alerts, and phishing attacks.
In an example of this campaign, the creation of the inbox rule in the affected organization eventually led to the compromise of additional accounts by sending side, internal, and outgoing phishing emails. The connection of the malicious device also allowed hackers to send emails within the organization without anyone being able to detect a single hint of suspicious activity, managing to deploy a wide-ranging attack.
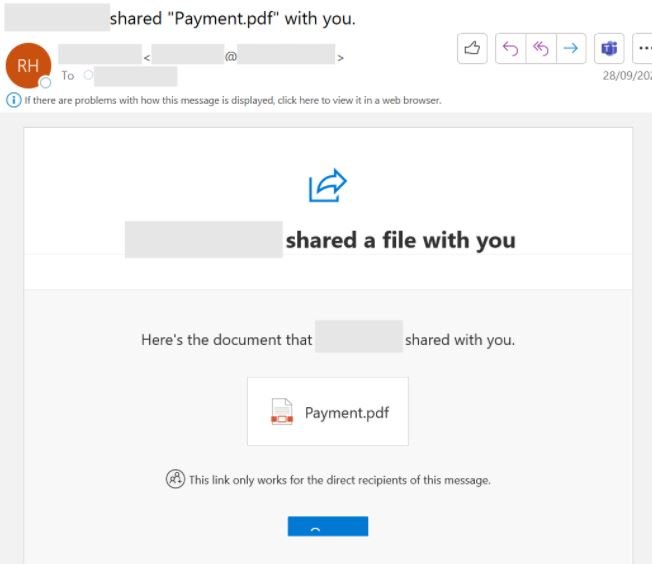
In this case, the attackers used the compromised inbox to send phishing messages to more than 8,500 email accounts inside and outside the affected organization. These messages resemble any other malicious email campaign.
This is a new example of how important it is to enable multi-factor authentication mechanisms as a standardized protection measure, as the success of an attack like this depends largely on the absence of these protections.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.















