An individual going by the twitter handle leostone was able to create an algorithm that can generate the password used to decrypt a Petya encrypted computer. In my test this, this algorithm was able to generate my key in 7 seconds.
The solution used to generate this key is called a genetic algorithm and is one that that mimics the evolutionary process in order to solve problems. According to MathWorks:
A genetic algorithm (GA) is a method for solving both constrained and unconstrained optimization problems based on a natural selection process that mimics biological evolution. The algorithm repeatedly modifies a population of individual solutions. At each step, the genetic algorithm randomly selects individuals from the current population and uses them as parents to produce the children for the next generation. Over successive generations, the population “evolves” toward an optimal solution.
Leostone has setup a web site that a victim can use to generate the key once they provide some information from the infected drive. Below are instructions on how to retrieve the required information so you can use leostone’s site to generate your decryption key.
How to generate your Petya Decryption key to decrypt your hard drive
To use Leostone’s decryption tool you will need attach the Petya affected drive to another computer and extract specific data from it. The data that needs to be extracted is 512-bytes starting at sector 55 (0x37h) with an offset of 0 and the 8 byte nonce from sector 54 (0x36) offset: 33 (0x21). This data then needs to be converted to Base64 encoding and used on the https://petya-pay-no-ransom.herokuapp.com/ site to generate the key.
Unfortunately, for many victims extracting this data is not an easy task. The good news is that Fabian Wosar created a special tool that can be used to easily extract this data. In order to use this tool, you need to take the encrypted drive from the affected computer and attach it to a Windows computer that is working properly. If your infected computer has multiple drives, you should only remove the the drive that is theboot drive, or C: drive, for your computer.
For those who may find it difficult to remove a hard drive from one computer and attach it to another, you can purchase a USB hard drive docking station. A docking station that I have used and recommend is the Inateck FD1003 docking station as it supports both 3.5″ and 2.5″ SATA drives and comes with everything you need to hook the drive up to a computer. Simply insert the encrypt drive into the docking station and then attach it via the USB cable to a working computer.

Once you have the encrypted drive attached to a working computer, simply download Fabian Wosar’s Petya Sector Extractor and save it to your desktop. Once saved, extract it and execute the PetyaExtractor.exe program. Once the program starts it will scan all of the removable and fixed drives on your computer for ones that contain the Petya Ransomware bootcode. When it detects the drive, it will automatically select it and display a screen like the one below.
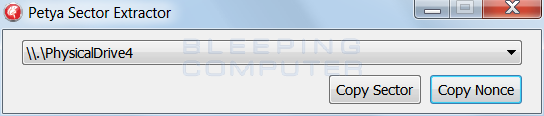
Now, open a web browser and navigate to the https://petya-pay-no-ransom.herokuapp.com site. On this site are two textboxes labeled Base64 encoded 512 bytes verification data and Base64 encoded 8 bytes nonce. In order for leostone’s site to generate your decryption key, you need to enter the data extracted from Fabian’s Petya Sector Extractor into these textboxes.
In Petya Extractor, click on the Copy Sector button, which will copy the 512 byte verification data to your clipboard. Now go back to the decryption site and paste (![]() ) the verification data into the textbox labeled Base64 encoded 512 bytes verification data.
) the verification data into the textbox labeled Base64 encoded 512 bytes verification data.
Then go back to the Petya Sector Extractor and click on the Copy Nonce button to copy the nonce to your clipboard. Once again, go back to the decryption site and Then go back to the decryption site and paste (![]() ) the nonce into the textbox labeled Base64 encoded 8 bytes nonce.
) the nonce into the textbox labeled Base64 encoded 8 bytes nonce.
When you are done, the decryption site should have data in both textboxes as shown below.
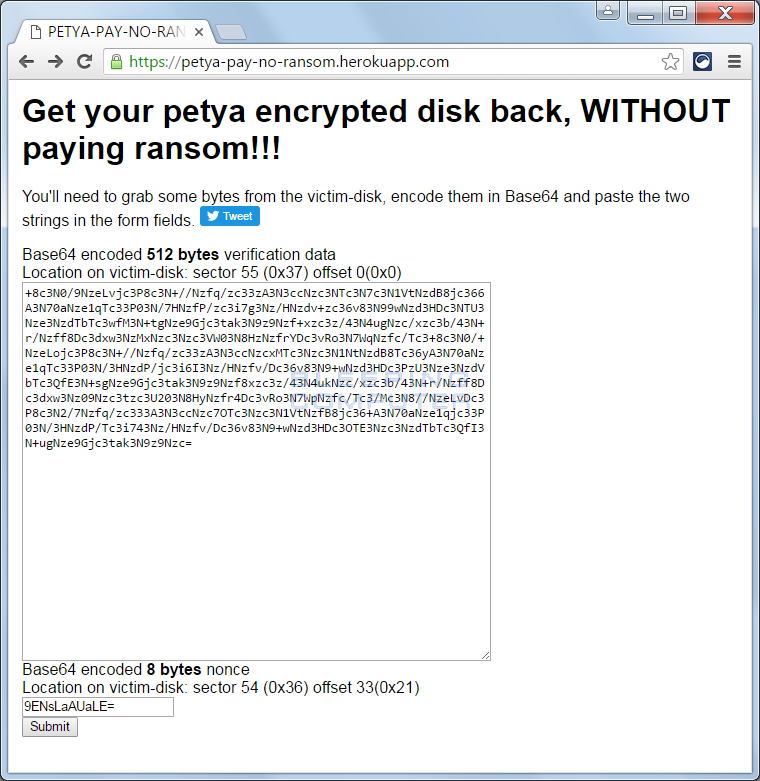
To generate your decryption password, click on the Submit button. Leostone’s site will now execute the genetic algorithm that is used to create your password for the Petya Ransomware lock screen. This process shouldn’t take more than a minute, and when done, will display your password as shown below.
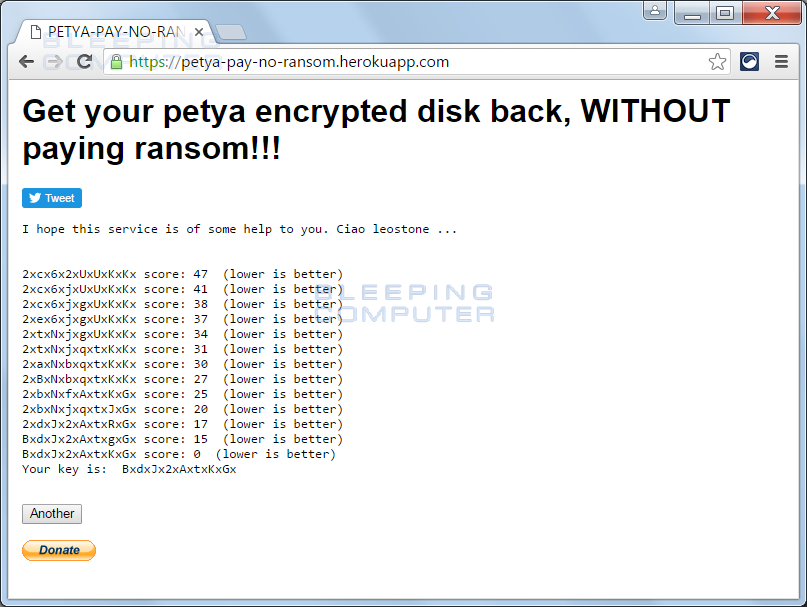
Now write down this password and attach your encrypted hard drive back into the original computer. With the drive attached, boot up the infected computer and when it gets the Petya Ransomware lock screen, enter the generated password. The password should be accepted and the ransomware will begin to decrypt your hard drive.
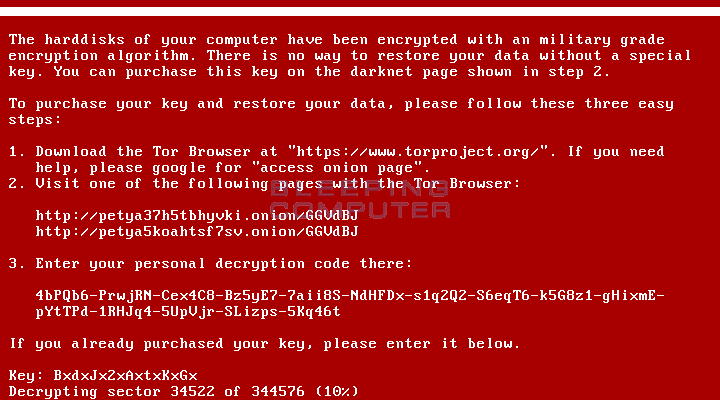
Once the hard drive is decrypted, the ransomware will prompt you to reboot your computer and it should now boot normally.
Source:http://www.bleepingcomputer.com/










